August 2024 Patch Tuesday
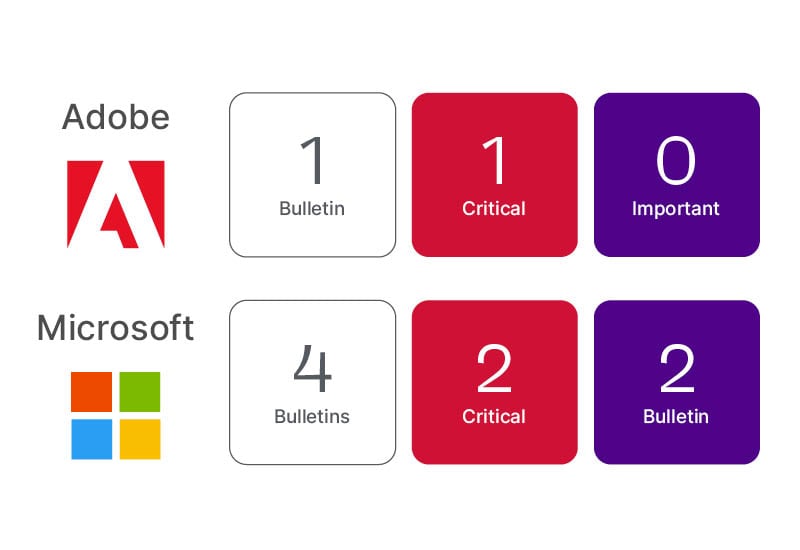
The Patch Tuesday lineup for August 2024 brings the typical lineup from Microsoft, an Adobe Acrobat and Reader update and an anticipated update for Google Chrome. Ivanti has some additional security updates to add to the mix this month.
Microsoft update summary
Microsoft has released updates for the Windows OS, Office, Edge, .Net and Visual Studio and several Azure services. The total new CVE count resolved was 87 (90 if you count updated CVEs and Advisories) from the Microsoft side and 12 non-Microsoft CVEs for Edge Chromium and Red Hat. Six CVEs have confirmed exploits, and there were two public disclosures that are worth taking a closer look at. The good news is the Windows OS and Office will knock out most of the risk pretty quick.
Microsoft known exploited and publicly disclosed CVEs
Microsoft has resolved a Remote Code Execution vulnerability in Microsoft Project (CVE-2024-38189) that could allow an attacker to socially engineer entry into execution arbitrary code on the affected system. CVSS rating is 8.8, Severity is Important and exploits have been detected in the wild. There are mitigating factors like policies to block macros from running in Office files from the internet and VBA macro notification settings. If these are enabled, the attack could be thwarted. Somewhere out there these policy settings were obviously disabled, allowing an attacker to exploit the CVE in the wild. Risk-based guidance would be to get your Office installs update this month. If you have limited control over the mitigating policy settings or have an open BYOD policy, updating Office could be more urgent to reduce your exposure.
Microsoft resolved an Elevation of Privilege vulnerability in Power Dependency Coordinator (CVE-2024-38107), which could let an attacker gain SYSTEM level privileges on the affected system. CVSS rating is 7.0, Severity is Important and exploits have been detected in the wild. The exploit does require the attacker to win a race condition, but as this has been detected in attacks already this is not cause to defer remediation. The vulnerability affects Windows Server 2012 and later OS editions. Risk-based guidance would treat this update as a higher severity than Important for remediation as soon as possible.
Microsoft resolved an Elevation of Privilege vulnerability in Windows Kernel (CVE-2024-38106) which could allow an attacker to gain SYSTEM level privileges on the affected system. CVSS rating is 7.8, Severity is Important and exploits have been detected in the wild. The vulnerability affects Windows 10 and later OS editions. Risk-based guidance would treat this update as a higher severity than Important for remediation as soon as possible.
Microsoft resolved a Security Feature Bypass vulnerability in Windows Mark of the Web (CVE-2024-38213), which could allow an attacker to bypass the SmartScreen user experience. CVSS rating is 6.5, Severity is Moderate and exploits have been detected in the wild. The vulnerability affects Windows Server 2012 and later OS editions. Risk-based guidance would treat this update as a higher severity than Moderate for remediation as soon as possible.
Microsoft resolved an Elevation of Privilege vulnerability in Windows Ancillary Function Driver for WinSock (CVE-2024-38193), which could allow an attacker to gain SYSTEM level privileges on the affected system. CVSS rating is 7.8, Severity is Important and exploits have been detected in the wild. The vulnerability affects Windows Server 2008 and later OS editions. Risk-based guidance would treat this update as a higher severity than Important for remediation as soon as possible.
Microsoft resolved a Memory Corruption vulnerability in the Scripting Engine (CVE-2024-38178), which could allow an attacker to initiate remote code execution on the affected system. CVSS rating is 7.5, Severity is Important and exploits have been detected in the wild. The vulnerability affects Windows Server 2012 and later OS editions. The attacker would need to prepare the target so that it would use Edge in Internet Explorer Mode to execute a specially crafted file. Risk-based guidance would treat this update as a higher severity than Important for remediation as soon as possible.
Microsoft resolved a Remote Code Execution vulnerability in the Windows Line Printer Daemon (CVE-2024-21302), which could allow an attacker to send a specially crafted print task across the network, allowing remote code execution on the affected system. CVSS rating is 9.8, Severity is Important and exploits have been publicly disclosed, increasing the risk of exploitation. The vulnerability affects Windows Server 2008 and later OS editions. Most environments should be mitigated against the vulnerability as the Line Printer Daemon (LPD) Service is disabled by default. For organizations that know they are using the LPD Service, a risk-based prioritization approach is recommended and you should remediate as soon as possible.
Microsoft resolved an Elevation of Privilege vulnerability in the Windows Secure Kernel Mode (CVE-2024-38199), which could allow an attacker to reintroduce vulnerabilities resolved by Virtualization-based security. CVSS rating is 6.7, Severity is Important and exploits have been publicly disclosed, increasing the risk of exploitation. The vulnerability affects Windows 10 and later OS editions. Risk-based guidance would treat this update as a higher severity than Important for remediation as soon as possible.
Third-party updates
Adobe has released a security update for Adobe Acrobat and Reader (APSB24-57) resolving 12 CVEs, eight of which are rated Critical.
Google has released an update for Chrome but has not announced CVEs at this time. Given they have targeted weekly updates that include CVEs, it is suggested to take a risk-based approach and ensure that Google Chrome is updated across your environment to resolve previously resolved CVEs as quickly as possible.
Ivanti security releases
Ivanti has released a Security Advisory including security updates for three products for Aug. 13. The affected products include Ivanti Neurons for ITSM (two CVEs), Ivanti Avalanche (five CVEs) and Ivanti Virtual Traffic Manager (one CVE).
Ivanti is not aware of exploits against the resolved CVEs, but there is one publicly disclosed CVE in the Ivanti vTM release (CVE-2024-7593). For details on the CVEs and affected versions, follow the links in the blog post to each of the product security advisories.
Remediation guidance
The highest urgency this month is the Windows OS and Office updates to resolve known exploited and publicly disclosed vulnerabilities and the Ivanti vTM to resolve the publicly disclosed vulnerability.