Can IT Security and Maintenance Be Less of a Time Hog?
Ivanti commissioned the downloadable IDG Connect research report entitled The CIO’s Conundrum: Can IT Move from ‘Keep the Lights On’ to Creative Thinking? Page 5 of the report addresses how IT security and maintenance gobble up tons of time, leaving less of it to pursue opportunity and innovation.
The report states that IT teams “can’t let go of the everyday, systemic controls but they’re also expected to be forces for ideation and creativity. The ability to defend on the security/governance/operations front while attacking on the opportunity/innovation flank is characteristic of successful business technology teams today.”
Page 5 of the report says “security is a notable time hog, but maintenance and monitoring are also big areas of activity and together they squeeze the precious hours available for investigating new technologies or finding the people who might deliver those ideas and bring them to reality.
Included on page 5 is this graphic that illustrates where IT professionals who responded to the IDG Connect research survey spend most of their time:
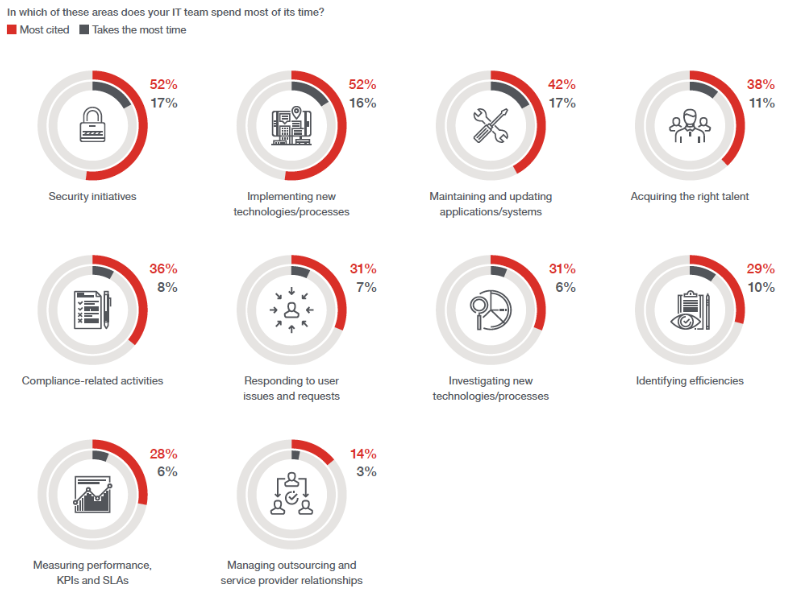
The IDG Connect report also notes that the stakes for not providing a secure and compliant IT environment have only been raised—there’s no room for letting the ball drop in these areas. But on the flip side, if organizations fail to innovate and create compelling customer experiences, they risk losing market share to more nimble companies that do so.
Where to Start: Do the “Everyday” Better and Faster
When it comes to strengthening your security stance, the best place to start is with discovery—determining what you have in your network. As Ivanti product manager Eran Livne wrote in a recent blog, discovery is the most important security requirement because you can’t protect or defend against what you don’t know you have in your environment.
As part of its Critical Security Controls, the Center for Internet Security (CIS) ranks hardware discovery and software discovery as the No. 1 and No. 2 things any organization must do in order to establish an efficient security posture.
Ireland-based Ivanti product manager David Murray writes that the CIS Critical Security Controls are a prioritized set of actions to defend against pervasive cyber threats.
“Each step along the way,” Murray says, “you are maximizing your impact on improving your defenses. This is particularly true of the first five controls, which are the things that you must do to create a strong security foundation. In other words, get these in place first and build from there. It removes a lot of the mystery in how to get started and how to develop your security strategy.”
The Need to Patch
Ivanti product manager Robin Rowe writes that patching remains an important security prerequisite. It ranks as No. 3 among the top 5 CIS Critical Security Controls. Rowe says that according to Gartner, 99 percent of the vulnerabilities exploited at the end of 2020 will continue to be ones known by security and IT professionals at the time of the incident.
Ivanti Helps You Speed Your Security Efforts
The IDG Connect report states on page 11 that security is woven into the fabric of business today. The IT audience that was surveyed for the report views security “as the table stakes of doing business” but many also view it as a financial burden that can slow down business and is a hindrance to driving competitive differentiation.
Ivanti can help you automate and streamline your security efforts to save time and money. We’ve aligned our security solutions and our product strategy to the CIS Controls mentioned above. We claim a solid heritage in asset discovery, vulnerability management, application control, device control, and privilege management, so we can help you get your cyber-security foundation in place. Take some time to learn more.

