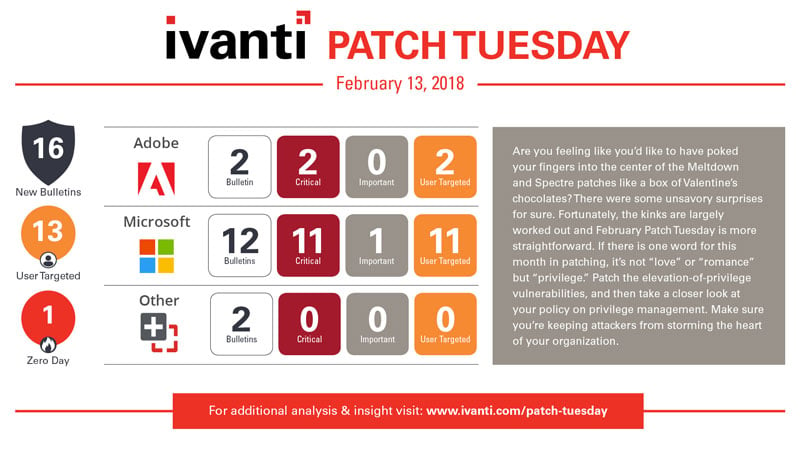
February Patch Tuesday 2018
Microsoft has released a pretty typical lineup this month. All the Operating System updates, Internet Explorer, Flash for IE, Edge, Office, and SharePoint are accounted for in February. There are a total of 50 unique vulnerabilities being resolved by Microsoft this month with one public disclosure. CVE-2018-0771 is a Security Feature Bypass vulnerability in the Edge browser that could allow an attacker to host a specially crafted website designed to exploit the vulnerability. Compromised websites and websites that accept or host user-provided content or advertisements are also susceptible. The attacker could force the browser to send data that would otherwise be restricted.
As I was reading through some of the vulnerabilities I came across this one that stood out. CVE-2018-0825 is a vulnerability in StructuredQuery that could allow Remote Code Execution. This is a user-targeted attack scenario that could allow the attacker to craft a file that could be used in an email or web-based attack. This vulnerability is in the OS though, so all systems are potentially vulnerable. The vulnerability can also be exploited through the Preview Pane, which makes this one a bit more threatening than some of the similar Office-based vulnerabilities this month.
I also noticed there are a number of elevation of privilege vulnerabilities this month. While these vulnerabilities cannot be exploited remotely, they could be used by a threat actor to gain elevated privileges on a system they have compromised through some other means. These would often be used in an APT (Advanced Persistent Threat) situation where the attacker is slowly working their way through an environment and need to gain additional permissions to gain access to move further toward their goal. CVE-2018-0820 (a vulnerability in the Windows Kernel), CVE-2018-0821 (a vulnerability in Windows AppContainer), CVE-2018-0822 (a vulnerability in NTFS Global Reparse Point), CVE-2018-0826 (a vulnerability in Windows Storage Services), CVE-2018-0844 (a vulnerability in Windows Common Log File System Driver), CVE-2018-0846 (a vulnerability in Windows Common Log File System Driver), and CVE-2018-0823 (a vulnerability in Named Pipe File System) each have an exploit index of 1 for the latest Windows versions. These updates cover a lot of services and the kernel so the monthly OS updates will affect a broad surface area. This is also a good example of the importance of layered security. If you are running least privilege for users in your environment, vulnerabilities such as these can still enable an attacker to gain full control of a system.
Microsoft has resolved six office vulnerabilities this month including several that could allow Remote Code Execution. These vulnerabilities could be exploited through a hosted website, via an attachment in email, etc. If exploited the attacker would gain equal rights as the current user, so if the user is a full administrator, the attacker would gain full control of the system. This is a good example of why privilege management is so important. It is hard to take admin rights back from a user once granted, but there are other methods to take away specific capabilities to take some of the risk out of that full administrator user as well. It is recommended to look into options to address this.
On the third party front, Adobe has released an update for Acrobat and Reader this month. APSB18-02 resolves 41 total vulnerabilities (CVEs) and 17 of those are rated Critical, but the more concerning release from Adobe this month was the February 6th update to Adobe’s Flash Player that resolved a Zero Day vulnerability being used to target South Korea. CVE-2018-4878 was discovered in targeted attacks against South Korea since around mid-November 2017. This and another Remote Code Execution vulnerability (CVE-2018-4877) were resolved in APSB18-03 last week. Both Adobe releases should be top of the priority list this month.
As always tune into Ivanti’s Patch Tuesday landing page for updated analysis as Patch Tuesday unfolds and sign up for our monthly Patch Tuesday webinar.