Infographic: Your Quick Guide to Simplifying Endpoint Security
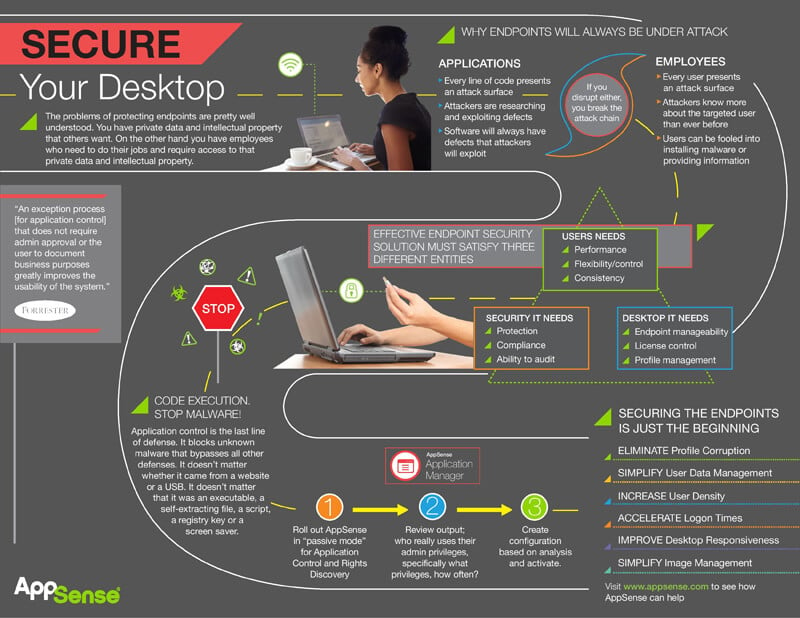
The problems of protecting endpoints are pretty well understood. You have private data and intellectual property that others want.
On the other hand, you have employees who need to do their jobs and who require access to that private data and intellectual property.
Endpoints will always be under attack. Every line of code in an application presents an attack surface that cybercriminals can exploit. These hackers are constantly researching and exploiting defects in code.
The overarching problem is that software will always have defects making it susceptible to attacks.
Similar issues exist for every user on your network. Employees also present an attack surface that can be exploited. As hackers become more sophisticated, they’re learning more about the targeted user than ever before. Users can easily be fooled into installing malware or providing sensitive information.
If you disrupt either the application or the user, you break the attack chain.
Effective endpoint security solutions must satisfy three different entities: user’s needs, security IT needs and desktop IT needs.
The top needs of the user are performance, flexibility and control, and consistency. The most important security IT needs are protection, compliance, and the ability to audit. Lastly, desktop IT needs are endpoint manageability, license control, and profile management.
Application control is the last line of defense. It blocks unknown malware that bypasses all other defenses. It doesn’t matter whether it came from a website or a USB. It doesn’t matter that it was an executable, a self-extracting file, a script, a registry key or a screen saver.
Using Ivanti, you can boost endpoint security in three steps:
- Roll out Ivanti in ‘passive mode’ for Application Control and Rights Discovery.
- Review output; who really uses their admin privileges, specifically what privileges and how often?
- Create configuration based on analysis and activate.
That’s just the beginning. Ivanti can also eliminate profile corruption, simplify user data management, increase user density, accelerate logon times, improve desktop responsiveness, and simplify image management.
