June 2023 Patch Tuesday
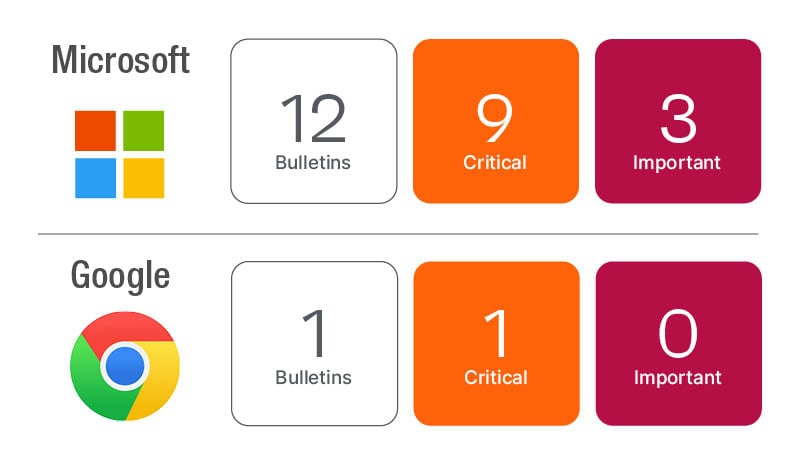
We are at the half-way point for Patch Tuesday releases in 2023. Microsoft has resolved 78 new CVEs and has made updates to seven previously released CVEs for 85 CVEs in this month’s update. This month’s update will have a lot more operational focus for organizations as Microsoft has advanced changes in Kerberos and Netlogon to address vulnerabilities originally discovered in 2022.
Microsoft updates
Microsoft made updates to two previously resolved CVEs that were confirmed to be exploited in the wild.
CVE-2023-24880 is a Security Feature Bypass in Windows SmartScreen and was first resolved in March 2023. Microsoft updated the CVSS score of this vulnerability (CVSSv3.1 4.4/4.1). Most organizations have likely patched this already, but the fact that it is confirmed exploited supersedes the CVSS and Microsoft severity of Moderate and should be considered in your prioritization.
CVE-2021-34527 is a vulnerability in Windows Print Spooler that could allow Remote Code Execution. Yes, this is a blast from the past known as PrintNightmare! The change is documentation-specific. Microsoft “added all supported editions of Windows 10 version 21H2, Windows 11 version 21H2, Windows 11 version 22H2 and Windows Server 2022 as they are affected by this vulnerability.”
Drilling into the KB articles and looking at the downloads, if you have done any updates since November 8th, 2022 or later, you should be covered from an update perspective, so this should be an information only change for most organizations.
Microsoft has implemented the third phase of Windows security updates to address an Elevation of Privilege vulnerability in Windows Kerberos (CVE-2022-37967). The first phase was implemented in November 2022 and added PAC signatures to the Kerberos PAC buffer and added security measures to address the security bypass vulnerability.
Phase two was implemented with the December 2022 update and put all devices into Audit mode by default, but still allowed the authentication.
With this month’s release, Microsoft is removing the ability to disable PAC signature addition. Next month (July 11th, 2023), Microsoft will start the initial enforcement by default, but still allows some override. In October 2023, Microsoft will transition to full enforcement, meaning any service tickets without the new PAC signature will be denied. For more details, see the following.
Microsoft has implemented the second phase of Windows security updates to address an Elevation of Privilege vulnerability in Netlogon (CVE-2022-38023). The first phase was implemented in November 2022 and implemented a default compatibility mode that removed the ability to disable RPC sealing. This enforced RPC sealing for Domain Controllers and use of Trusted accounts.
In the June update, Microsoft has moved to Enforced mode by default unless an administrator is explicitly configured to be in compatibility mode. In next month’s release, Microsoft will implement Phase three of the Netlogon changes to remove the ability to run in compatibility mode. For more details, see the following.
Chrome and Adobe updates
Google Chrome has released a security update resolving five CVEs including one Critical and three High severity CVEs. The most concerning of these five is a use after free in Autofill payments (CVE-2023-3214).
Adobe has released four Priority 3 updates, three of which include one or more Critical CVEs. The updates affect Adobe Experience Manager, Commerce, Animate and Substance 3D Designer. Adobe’s priority definitions identify a priority 3 as an update that “resolves vulnerabilities in a product that has historically not been a target for attackers. Adobe recommends administrators install the update at their discretion.”

