Locky / Zepto Ransomware Now Being Installed From DLL… We Don't Care…
*This post originally appeared on the AppSense blog prior to the rebrand in January 2017, when AppSense, LANDESK, Shavlik, Wavelink, and HEAT Software merged under the new name Ivanti.
It’s not just US healthcare organizations falling victim to malware and ransomware. Last week the BBC reported that the UK National Health Service and educational institutions are also feeling that pain.
One example cited in the story was Bournemouth University, the establishment which awarded me a Bachelor of Science degree in Business Information Technology all those years ago. The University has been attacked no less than 21 times in the last 12 months.
Also last week BleepingComputer.com reported on a new version of the Locky ransomware. Whilst still distributed by JS attachments, the payload has now morphed to utilise a DLL file to carry out the task of encrypting all those user files and displaying the ransom note. BleepingComputer noted “This is probably being done for further obfuscation and to bypass executable blockers as rundll32.exe is typically white listed.”
These two news stories unfortunately demonstrate scary trends in cyber threats seen over the last 12 months:
- Ransomware threats are increasing
- Ransomware is a global problem
- No vertical market and no organization is safe
- Attackers are using increasingly sophisticated and ever-changing techniques
The good news here is that organizations utilizing AppSense Application Manager for application control and endpoint protection will be protected from this ransomware due to its unique approach to application whitelisting.
Application Manager whitelisting can be configured in the same way as any list-based technology. But, our Trusted Ownership™ technology developed in 1999 has protected thousands of customers from known and unknown threats without requiring them to maintain and manage a list of known executables.
Anyone who has tried to implement AppLocker knows that a list-based approach to application control is difficult to implement, let alone maintain. Unless you have Second Sight, you don’t know what the next bad executable is, so you can’t implement a truly comprehensive list of known bad actors. Implementing a list of known good applications is the ideal protection against the unknown, but listing and updating hundreds if not thousands of good executables is an enormous and daunting challenge.
The AppSense approach is simple. If a user introduces the file, it is blocked by default, and the user receives an error message. If the business introduces the file, (typically via administrator accounts, SCCM, LANDESK LDMS, AppV, etc.), then AppSense allows it to run by default. You have to see it to believe how simple and effective this approach is and we would be happy to give anyone a demo.
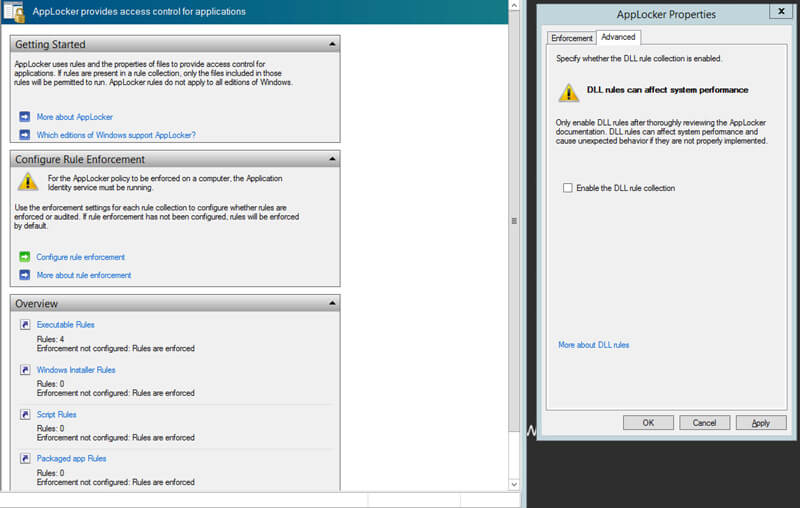
If the task of managing executables wasn’t hard enough, the current need to filter and control DLL’s, OCX files, batch files, MSI installers, and VB scripts becomes an even bigger challenge. Because the most recent versions of ransomware use both scripts and now DLL files, the need to whitelist more than just executables is a nightmare come true for both security folk and Windows admins. Even Applocker shudders at the thought of you monitoring and implementing a whitelist for DLL control.
Fear not! AppSense uses the same proven Trusted Ownership technology to protect users from even new ransomware variants.
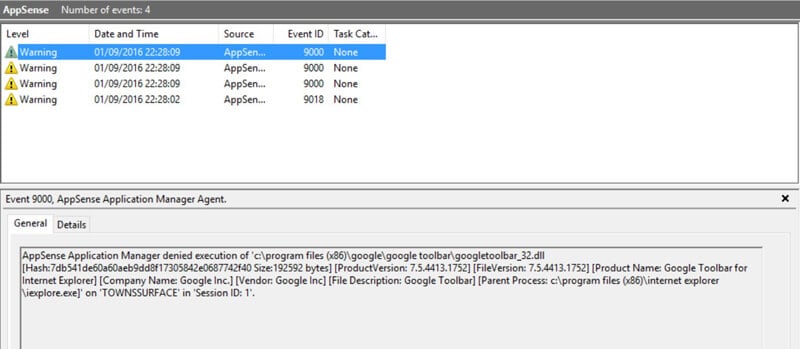
Whilst Application Manager won’t display an error message when it blocks a DLL file, rest assured that every execute request is being checked. Admins can always see which files are being blocked by checking audited events in either the event log or the centralised management server database.
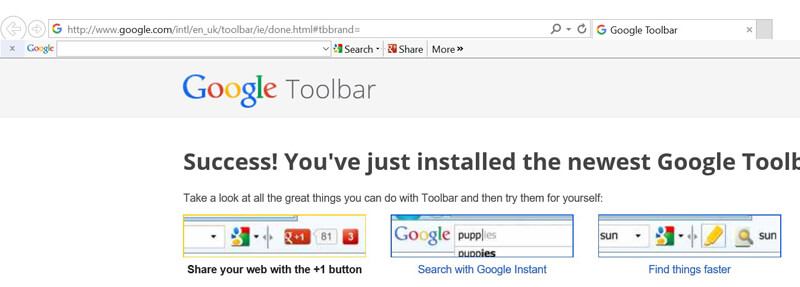
Want to test this in Application Manager? Load a user-introduced web browser plugin or toolbar—as an example, the IE Google toolbar utilises DLL files, which load when IE loads. A system without Application Manager installed will allow both IE AND the plugin to run so the toolbar is displayed. A system secured with AppSense would allow IE to run, but the DLL would be blocked, so the toolbar will not be visible.
Here’s IE installed on a system not secured by AppSense Application Manager:
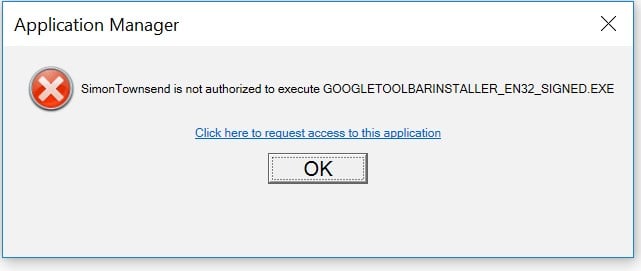
The Google toolbar uses an .exe installer which Application Manager blocks at the .exe level before the install even starts. I tried it and got this error message:
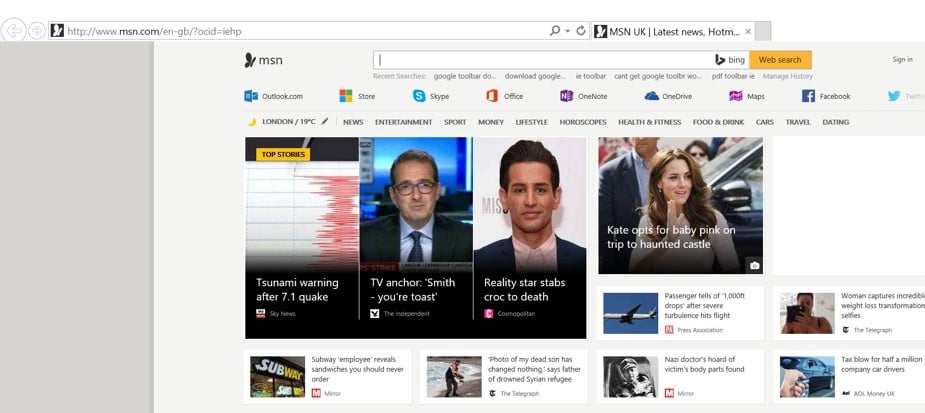
With Application Manager enabled, the DLL file doesn’t load and the Google toolbar is nowhere to be seen in the new IE installation.
Auditing events showing the blocked DLL file:
Happily, should the ransomware introduce the DLL file another way (that is, not as part of an .exe installer), Application Manager will still block the DLL.
So, the next time a user accidently clicks on a seemingly innocent email, and the payload tries to execute a hidden DLL file, script, batch file, or exe, AppSense Application Manager will simply block and audit…
It’s whitelisting made simple.