NIST and the Evolution of Zero Trust
It’s important for every cybersecurity professional to understand the work of the National Institute of Standards and Technology (NIST). That’s because it plays a pivotal role in shaping the cybersecurity landscape, particularly through its groundbreaking NIST zero trust efforts.
Zero trust is a security paradigm that transforms the traditional approach to network security. Instead of assuming that everything (and everyone) inside an organization’s network is trustworthy, zero trust operates on the principle of “never trust, always verify.”
Why does this matter? The NIST zero trust model directly responds to the evolving threat landscape, where cyberattacks are increasing in sophistication and frequency.
Statistics underscore the critical nature of this situation. In their most recent annual data breach report, the Identity Theft Resource Center found the number of breaches in 2023 had jumped by 72% compared to the previous record set in 2021. The impact of this increase isn’t limited to medium and large enterprises: SMBs can be disproportionately damaged as they typically don’t have access to the same level of IT resources as bigger organizations.
Responding to an inadequate approach
The concept of zero trust emerged as a response to the limitations of traditional perimeter-based security models. The latter relied on the assumption that threats primarily originated from outside the network and that once entities were inside, they could be trusted.
But perimeter security measures like firewalls and VPNs have proven deficient in the face of insider threats, advanced persistent threats (APTs) and the increasing mobility of users and devices. Recognizing these challenges, NIST began to explore and advocate for a more robust security framework.
NIST’s involvement with zero trust is multifaceted, encompassing the development of guidelines, frameworks and collaborative initiatives. One of the foundational documents in this effort is NIST Special Publication (SP) 800-207, titled "Zero Trust Architecture.”
It lays out a comprehensive framework for implementing zero trust principles within an organization. It outlines the core components of a zero trust architecture, including identity verification, access control and continuous monitoring.
Key components of NIST SP 800–207
- Identity verification — NIST zero trust principles stress the importance of verifying the identity of users and devices before granting access to resources. Verification involves robust authentication mechanisms, such as multi-factor authentication (MFA), to ensure that only authorized entities can access sensitive data and systems.
- Access controls — Access to resources should be granted based on the principle of least privilege, meaning users and devices should only have the minimum level of access necessary to perform their functions. NIST provides guidelines for implementing role-based access controls (RBAC) and just-in-time access provisioning to minimize the attack surface.
- Continuous monitoring — NIST advocates continuous monitoring and real-time assessment of security postures. This involves using advanced analytics and machine learning to detect and respond to anomalies and potential threats. By continuously evaluating the trustworthiness of users and devices, organizations can dynamically adjust access controls and mitigate risks more effectively.
The National Cybersecurity Center of Excellence (NCCoE) and practical implementations
NIST’s relationship with zero trust extends beyond the publication of guidelines. It actively collaborates with other government agencies, academic institutions and industry partners like Ivanti to advance the adoption of zero trust principles.
The National Cybersecurity Center of Excellence (NCCoE) is a collaborative hub where experts from industry, government and academia come together to address cybersecurity challenges and provide best practices and guidance. In the context of zero trust, the NCCoE has developed several projects and real-world use cases demonstrating how organizations can implement zero trust principles in their environments.
These projects provide valuable insights and practical guidance for organizations striving to improve their security postures and seeking guidance on executing a zero trust strategy.
Ivanti’s role in NIST and NCCoE zero trust architecture
Ivanti actively works with the NIST and NCCoE on various initiatives, particularly the Implementing a Zero Trust Architecture (ZTA) project. NIST and industry partners like Ivanti have collaborated to build no less than 17 example ZTA solutions in the NIST NCCoE Lab to solve real-world zero trust use cases.
Lessons learned from implementations and integrations can help your organization save time and resources. Detailed technical information on each build can serve as a valuable resource by supplying models your technology implementers can emulate.
Ivanti offers a unique combination of solutions built around NIST zero trust principles to solve real-world use cases including Ivanti Neurons for Zero Trust Access, Ivanti Neurons for Modern Device Management and Ivanti Zero Sign-On. These provide Policy Enforcement Points, Policy Decision Points and Policy Information Points in the overall zero trust architecture.
Relevant components of these solutions are shown in the diagram below. Additional information on the architecture and use cases enabled by Ivanti can be found in the NIST SP 1800–35 Enterprise 1 Build.
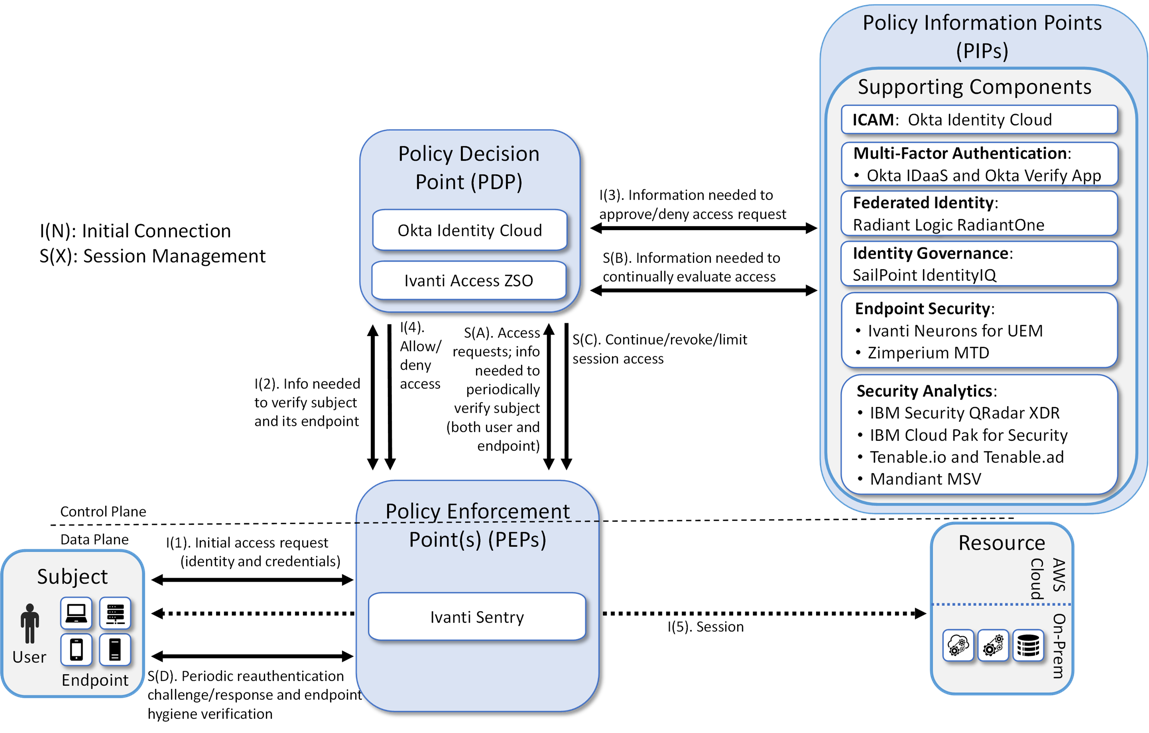 NIST NCCoE Enterprise 1 Zero Trust Architecture
NIST NCCoE Enterprise 1 Zero Trust Architecture
Continuous improvement and adaptation
The NIST zero trust architecture has the principle of least privilege as a fundamental element. This dictates that users and devices should only have the minimum level of access necessary to perform their functions. By limiting access rights, organizations can reduce the attack surface and minimize the potential impact of a security breach. NIST zero trust guidelines provide practical recommendations for implementing least-privilege policies. Those include role-based access control and just-in-time access provisioning.
NIST also recognizes that, while the cybersecurity landscape is constantly evolving, so must strategies to protect against emerging threats. As part of its commitment to continuous improvement, NIST regularly updates its guidelines and frameworks to reflect the latest advancements in technology and threat intelligence.
This iterative approach ensures that organizations have access to the most current and effective strategies for implementing zero trust, underscoring NIST's adaptability and commitment to staying ahead of emerging threats.
Challenges and considerations in implementing NIST zero trust
While adopting NIST zero trust principles offers security benefits, it also poses challenges. Implementing a zero trust architecture requires a comprehensive understanding of an organization's assets, users and workflows. It also demands the integration of various security technologies and the establishment of robust identity and access management (IAM) systems.
NIST recognizes these challenges and provides guidance for addressing them. For example, NIST SP 800–207 includes recommendations for conducting thorough asset inventories, mapping data flows and establishing clear policies and procedures for access control. NIST also stresses the importance of user education and awareness enabling employees to understand and adhere to NIST zero trust principles in order to strengthen overall security posture.
The future of zero trust
As cyber threats continue to evolve, the importance of zero trust will only grow. NIST's ongoing and dedicated efforts to refine and promote zero trust principles will play a vital role in helping organizations stay ahead of these threats.
By providing practical guidance, advocating for continuous improvement, fostering collaboration and partnering with cybersecurity industry leaders like Ivanti, NIST zero trust principles can provide the bedrock for a more secure and resilient digital ecosystem. And that, in turn, provides a real cause for optimism about the future of cybersecurity.
Read more about Ivanti’s Zero Trust Access solution and learn how you can adopt a robust security model built on continuous verification and least-privilege access.
