Patching in Review – Week 29
July Patch Tuesday may have wrapped up last week, but this week was far from quiet. Three vendors released updates remediating a total of 103 CVEs while Microsoft pushed out a set of non-security fixes from Patch Tuesday’s aftermath.
I strongly recommend you consider including the patches below in another wave of updates before the next month. Your usual monthly patching cycle may be over, but patches continue to release with numerous vulnerability and stability fixes.
Security Releases
A new quarter means a new Java release, and this release fixes a total of eight vulnerabilities. Notably, 100% of the Java SE severities can be remotely exploited without authentication.
The highest severity vulnerability is CVE-2018-2938 with a CVSS v3 score of 9.0, pushing it into the Critical category. This vulnerability includes Java SE 8 and affects the Java DB component where no user interaction is required for successful exploitation. Three more vulnerabilities (CVE-2018-2964, CVE-2018-2941, and CVE-2018-2942) have a CVSS v3 score of 8.3, classifying them as a High severity. All three require user interaction to successfully exploit while two of the three affect the newer Java 10 branch.
Here's a list of the CVEs and their color-coded severity:
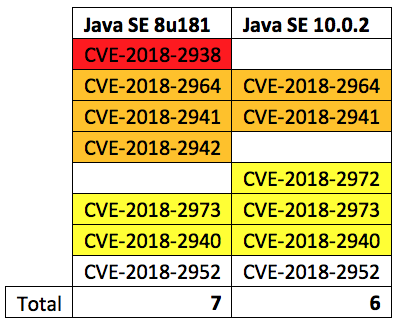
Further details are available on Oracle’s July security advisory page.
Wireshark also released new builds on their three branches with a total of ten CVEs. All these CVEs have yet to be classified by Mitre, but do not underestimate the severity of these vulnerabilities.
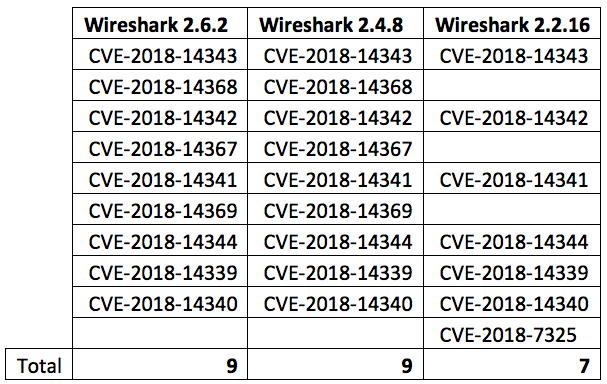
Further details are available on Wireshark’s release notes:
Finally, Foxit released version 9.2 of their Reader and Phantom PDF software with a whopping 85 CVEs. 83 of these CVEs were discovered through the zero-day initiative. The two highest rated CVEs, CVE-2018-14279 and CVE-2018-14280 both have a CVSSv2 score of 7.5, classifying them as a High severity.
Foxit is currently ranked #12 for most vulnerabilities in 2018 on CVE Details from the two previous releases. The vulnerabilities in this third release of the year should land them a top 10 spot. This is a prime example of how vulnerable unpatched software can be if endpoints are out of date by more than one release.
Further details can be found in Foxit Software’s release notes.
Emergency OS Non-Securities
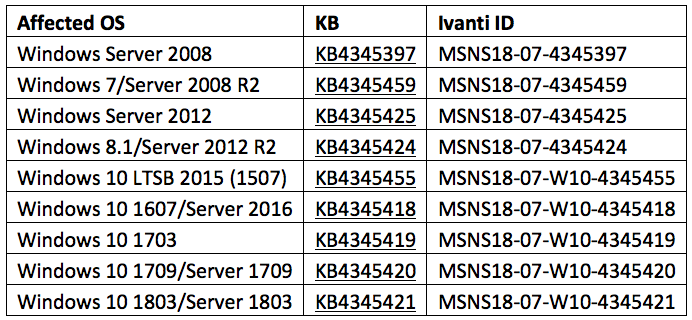
This Patch Tuesday will not go down as the most stable set of updates with reports of numerous endpoints experiencing system crashes after last week’s updates were deployed. This week Microsoft released a series of emergency non-security fixes for all supported operating systems. These updates fix the following:
- Some devices may experience stop error 0xD1 when you run network monitoring workloads
- The restart of the SQL Server service may fail with the error, “Tcp port is already in use”
- An issue may occur when an administrator tries to stop the World Wide Web Publishing Service (W3SVC)
This update also resolves the issue for Server 2016 where an updated DHCP failover server will cause result in loss of connectivity for endpoints.
Be sure to expedite the distribution of these patches to your environments as blue screens can ruin anyone’s day. Here’s a table of KBs and the operating system each one applies to:
Third-Party Updates
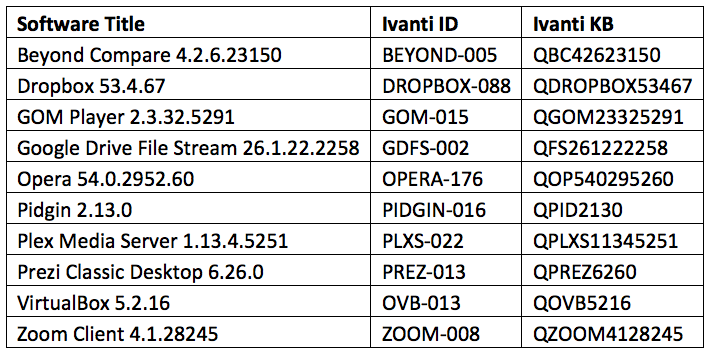
These updates might not have CVEs, but they may still have helpful stability fixes as well as undisclosed security fixes. These are the updates we released in our content for the week:
More Patch Resources:
