Preventing the Jeff Bezos iPhone Hack in a BYOD Deployment
Okay, I’ve been receiving pushback from several people regarding the recent Jeff Bezos iPhone hacked blog posted a couple of days back. The solution assumes that the mobile device is company-owned and more stringent policies can be enforced like banning known vulnerable versions of WhatsApp by blocking the entire app bundle completely. Some of the feedback has been, WhatsApp is the most popular and downloaded messenger app around the world! How do you protect mobile devices from malicious threats if there is a personally enabled component like a BYOD policy?
To answer the latter question, BYOD deployments assume that there are two personas that co-exist on the managed mobile device. The function of Unified Endpoint Management (UEM) and Mobile Threat Defense (MTD) is to protect the Android Enterprise work profile or iOS user enrollment partitioned apps and content without interfering with the personal side to ensure privacy. The personal side is controlled by the owner and they have the option to install any app they wish into that partition. If a malicious app is downloaded on the personal side that roots an Android device or jailbreaks an iOS device, UEM and MTD will detect the new device state and can enforce a compliance policy because the exploit has evolved to the device level. In a rooted or jailbroken state, the personal and work partition separation security is no longer reliable.
So, how can a CISO and security architect implement a company security policy that satisfies employees who want to use a popular messaging app like WhatsApp in a BYOD deployment? First, the app must be properly vetted. MTD provides an advanced app analytics service built into the solution that provides an enormous amount of details about app characteristics and behavior based on privacy and security risks – including data leakage assessment. Additional company red team activities can involve app security penetration including using a protocol fuzzer on all apps that will be installed on managed mobile devices.
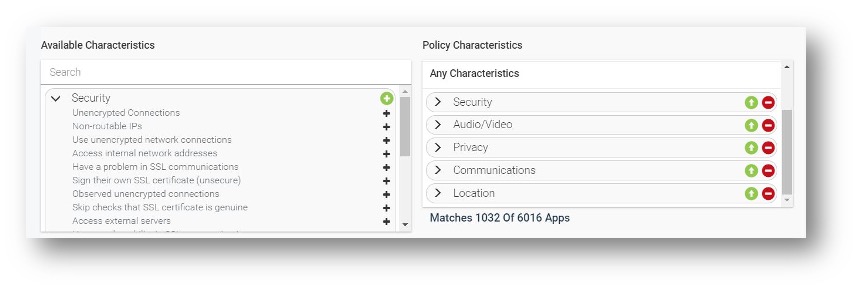
Figure 1 – App characterizes within App Policies of MTD management console
The company security policy can allow only the vetted version of the app to be installed, designate older versions of the app as out-of-compliance, and block known vulnerable versions from the work partition. The procured app can also be managed and silently installed into the work profile so versioning can be managed by the UEM administrator via the App Catalog or pushed by the enterprise app store.
If this best practice is not implemented, the device compliance action for an out-of-compliant app could be to notify the user and admin that an older version is installed on a managed device. The next step is to apply a tiered compliance policy to allow the user to manually update the app to the allowed version in a specified grace period like 1 to 4 hours. If the user fails to update the app, the device can be blocked from accessing corporate resources or quarantined by removing or hiding the other managed apps and content until the device state is returned to a compliant state.
Below is the list of known vulnerable versions of WhatsApp to the Pegasus spyware implant. These versions should be blocked from installation into any mobile device. Rooted or jailbroken versions of any app from a non-sanctioned (third party) app store will automatically be blocked by UEM and MTD as an unknown source or as a sideloaded app.

Figure 2 – List of vulnerable versions of WhatsApp
The screenshot below shows the Apps list and different versions of WhatsApp installed on managed iOS and Android devices. The app policy depicted below is showing how vulnerable versions are blocked (Deny), older versions are marked as out-of-compliance, and only the latest versions can be installed onto the managed devices.
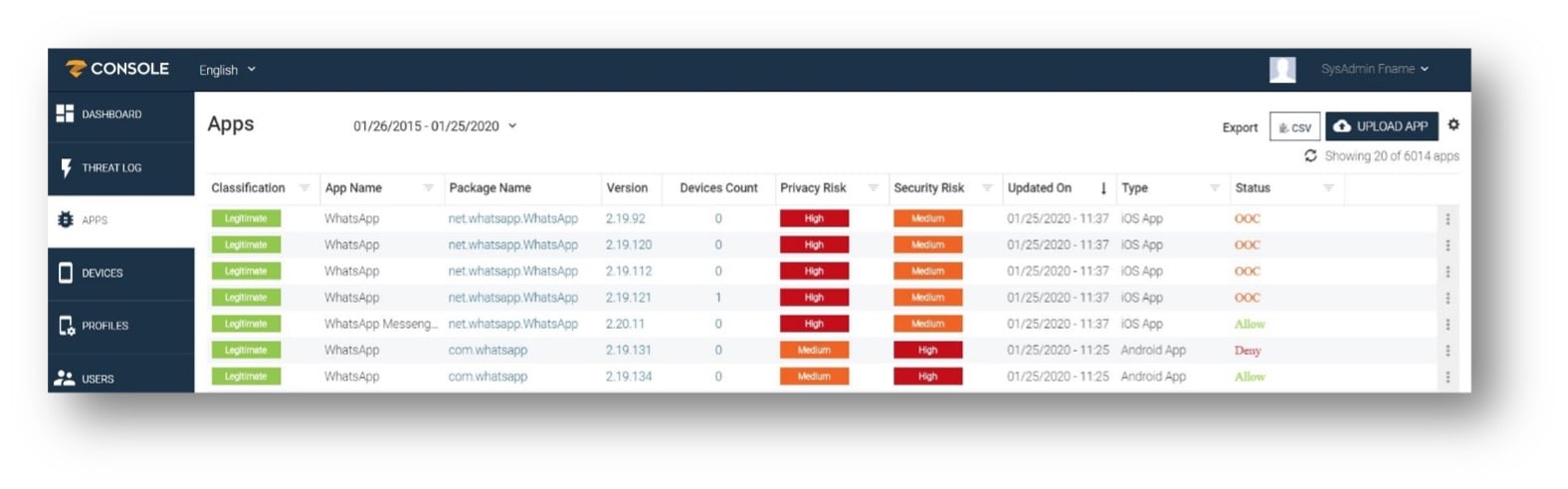
Figure 3 – App policy
Proactively, the UEM administrator can manually upload the latest versions of the app directly from the iOS App Store or Google Play Store using the app URL. Once imported, MTD will perform an advanced app analysis checking for privacy and security risks. This data can be the basis for their corporate app policy for all apps installed on a managed device.
Employing a UEM with the integrated MTD client ensures protection of both managed and lightly-managed mobile devices from malicious apps and phishing, as well as, device and network threats.

