The Ultimate Guide to Intune Migrations to Ivanti UEM: Connect to your Enterprise Resources
When migrating from Intune, Ivanti UEM can provide users secure access to enterprise services, either on-premises or via the cloud based. This is another key pillar of our ultimate guide to migrations from Intune to Ivanti UEM.
Ivanti provides Ivanti Access for cloud authentication infrastructure and Ivanti Sentry for on-premises resources. Both components leverage conditional access to ensure only secure, known devices are allowed to authenticate.
If you are using Entra Conditional Access as part of your Intune deployment and wish to continue using this, Ivanti UEM has an out-of-the-box integration to send compliance information from Ivanti-managed devices into Entra. This is configured in the Ivanti UEM admin console under the Admin-Microsoft-Device Compliance header.
Ivanti Sentry
Ivanti Sentry is a highly scalable appliance server that can be deployed in your environment as a virtual machine (VM) on-premises or in the cloud (AWS or Azure). With the right resources, up to 20,000 device connections can be supported on a single VM. This gives you the flexibility to place Sentry servers where needed. Customers can freely deploy as many Sentry instances as required – for example behind a load balancer for High Availability or regional instances for optimal connectivity.
Installation is mostly automated; admins only need to provide environment variables (network details). The final step registers Sentry to your Neurons UEM instance.
Once installed, Sentry can be configured to accept VPN connections from the Ivanti Tunnel VPN end user application, and/or behave as an ActiveSync proxy for both on-premises and Exchange Online implementations.
Sentry configuration post-installation is done entirely from within the Ivanti UEM console under the Admin-Infrastructure-Sentry tab. The only time you need to directly interact with the Sentry server is for upgrading or troubleshooting.
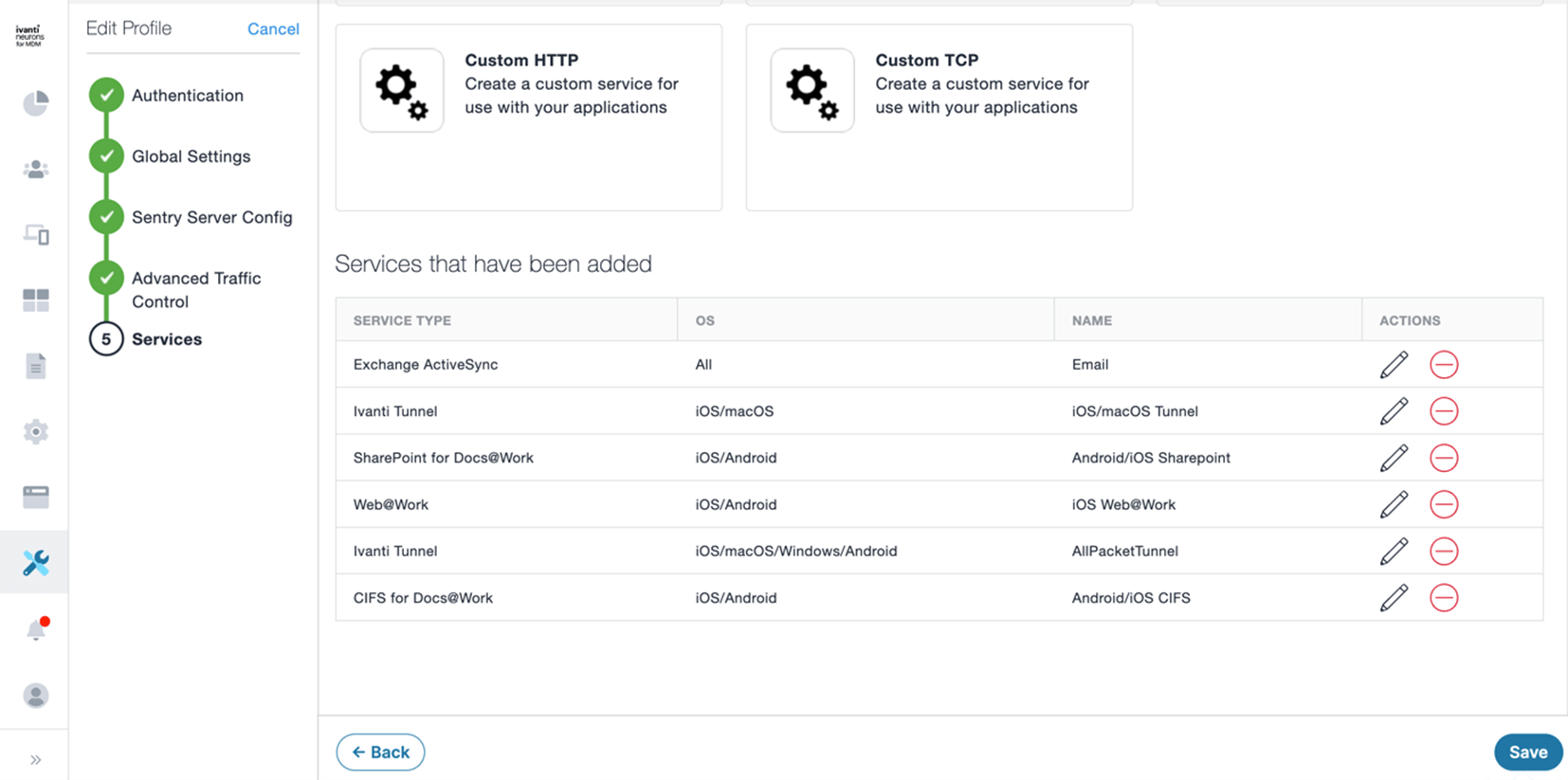
After configuring the services you wish to use on Sentry, the profile is assigned to the server(s) and automatically pushed/updated to make changes live.
As part of the device authentication process (certificate or Kerberos authentication is supported), Sentry checks the device posture with the UEM console to ensure the device is managed, in a compliant state and will block or revoke connections should a device fall out of compliance. This protects the services that sit behind Sentry from bad devices/actors.
Ivanti Access
Ivanti Access is an Ivanti-hosted cloud service that secures access to business cloud services such as Box, G Suite, Office 365, Salesforce, etc.
Ivanti Access can provide conditional access based on the following:
- Device identity: Ensures only enrolled and compliant devices can authenticate. Ivanti Access is also able to distinguish between company- and employee-owned devices.
- User identity: Ensures the user trying to authenticate is allowed to access the resource.
- App identity: Ivanti Access can block authentication on any unknown or disallowed apps, ensuring only IT-approved applications are allowed to authenticate.
The technology Ivanti Access is based on utilizes federation and authentication with SAML or WS-Fed services and authentication with FIDO2 or certificate-based authentication. If your identity provider (Idp) and service provider (Sp) supports one or more of these, it should work with Ivanti Access.
Depending on the capabilities of your Idp, Ivanti Access can be configured in:
- Full-federation mode, in which Ivanti Access sits in the middle of your authentication flow.
- Delegated-Idp mode, in which your Idp controls which authentication requests are sent to Ivanti Access for conditional access and authentication.
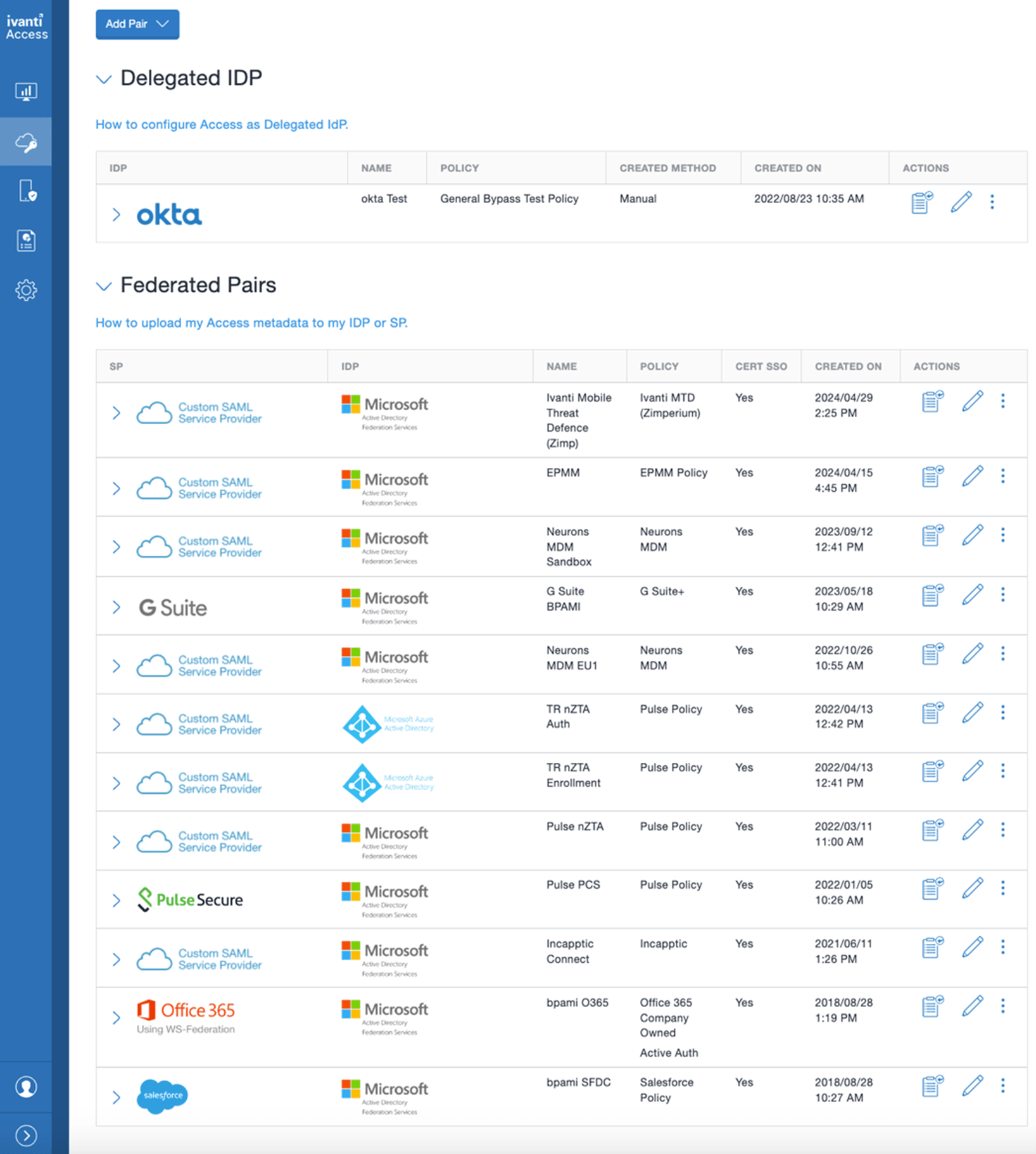
Multiple Ivanti UEM instances can be linked to a single Ivanti Access instance (on-premises or cloud-based), as well as support out of the box for SCCM- and JAMF-managed devices.
Ivanti Access is configured on a per-service basis, so organizations can onboard services at their own pace; it doesn’t have to be a “big bang” approach. Flexibility is a big benefit of Ivanti Access; I have over 10 Sps configured across three Idps, as the screenshot below shows.
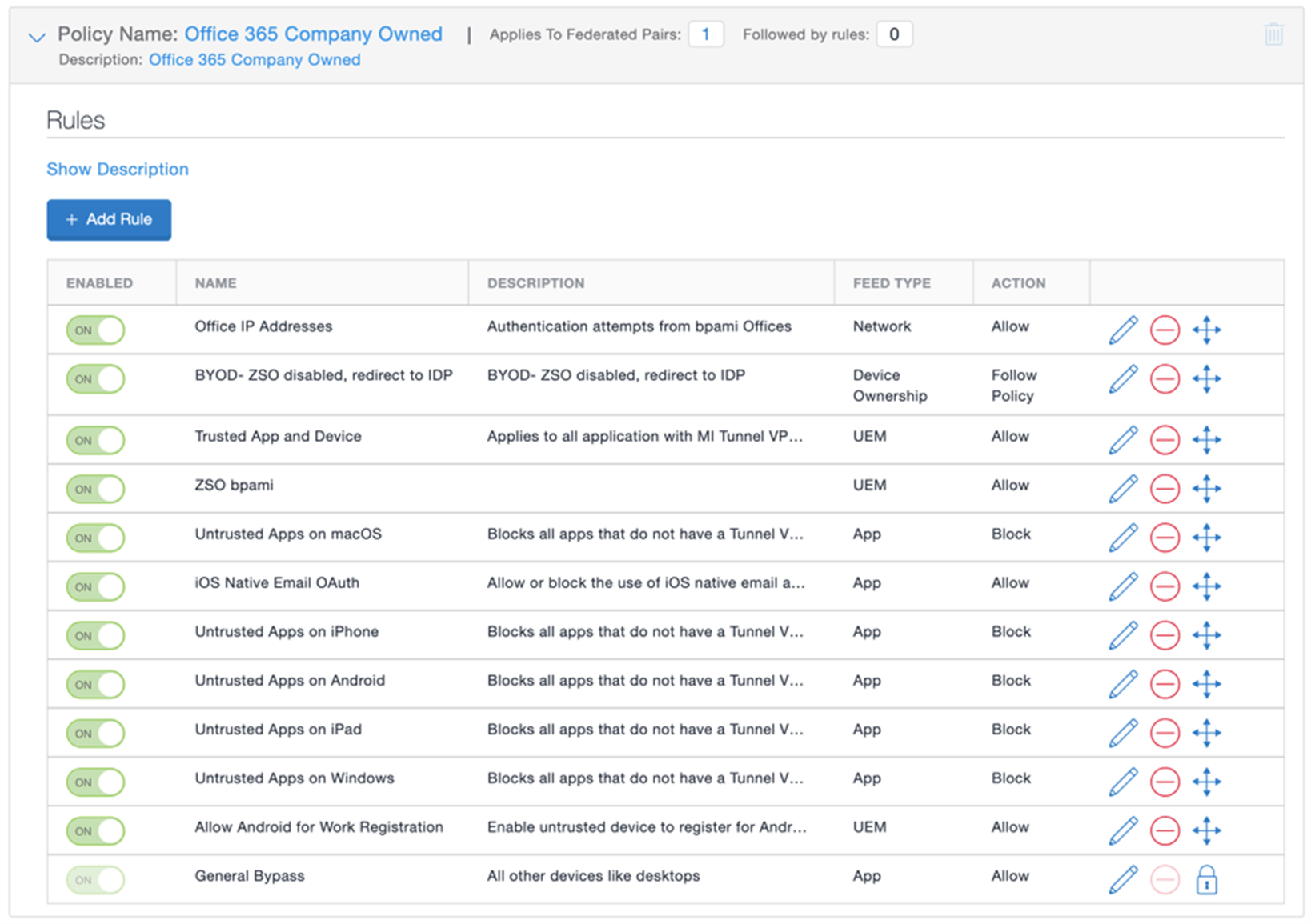
After adding services, the next step is to create or assign a conditional access policy. Each service can use the same policy, or you can create separate policies. The configuration possibilities can be very granular and utilize templated/default options, custom policies, set Allow/Warn/Block or policy-chaining actions.
The final step is to set the user experience for when users are blocked. Ivanti Access displays customizable remediation pages, allowing you to tell users not only that they have been blocked, but also what they need to do to gain access. This is a much more intuitive user experience than showing “Access Denied” with a long error code – or worse, no additional context. This can help reduce the number of help desk calls related to authentication issues.
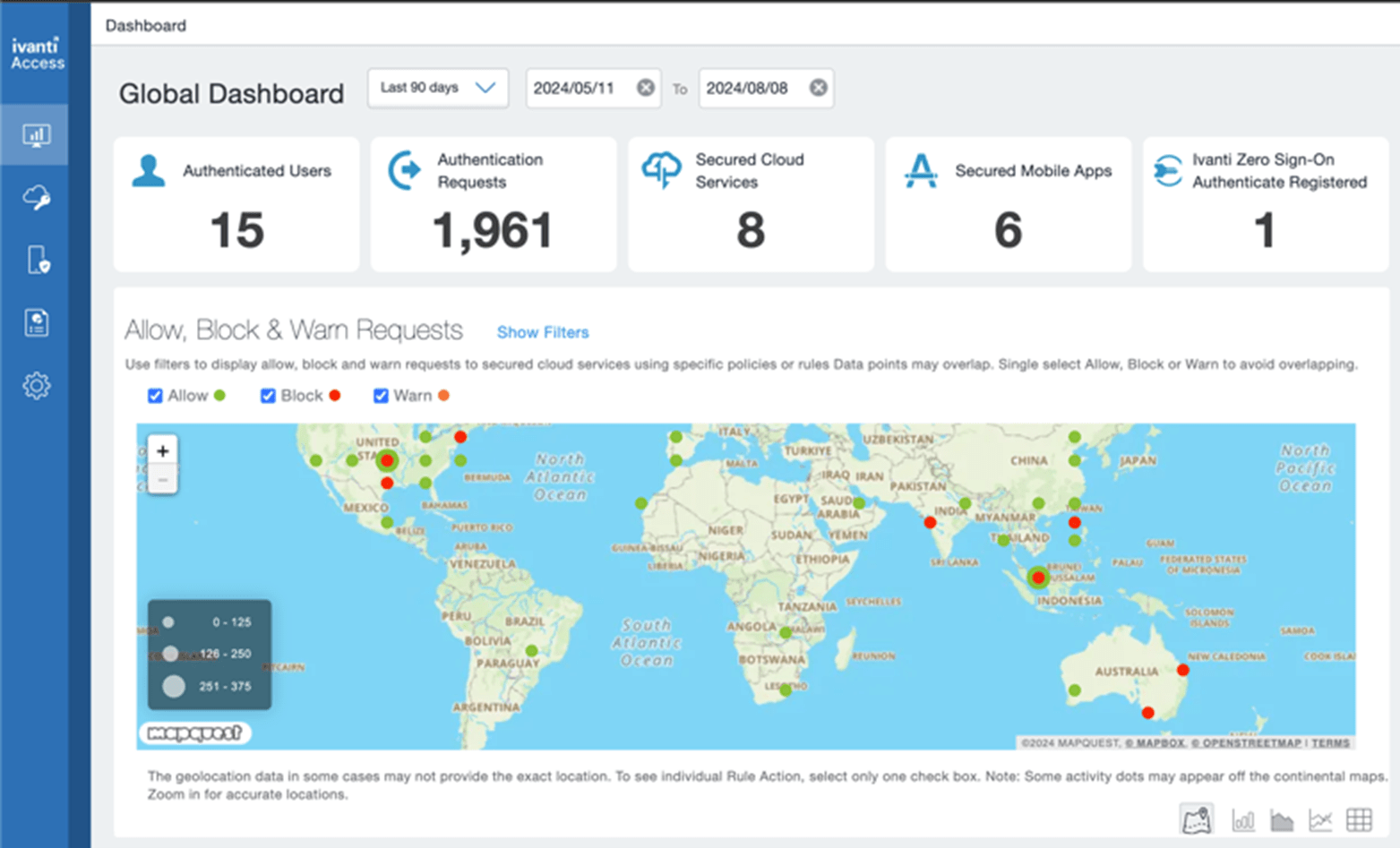
User authentication attempts are visible in near real time under the reports tab. Admins can view granular-level records or use the dashboard available on the home page that will show your entire user estate at a high level.
User experience
Sentry and Ivanti Access are designed to be invisible services to your end users when using devices managed by Ivanti UEM.
A significant benefit for your users with Ivanti Access is our Zero Sign On technology. Ivanti can replace the password with certificate-based or FIDO2-based authentication for true password-less authentication. Depending on configuration, this can be an entirely invisible process when using a compliant device. Authorized apps are installed by admins or users and start working without the user entering any information.
For desktop users, administrators can allow any mix of QR code, security key (e.g., YubiKey), device biometrics (Windows Hello or TouchID), Ivanti Authenticate ZSO client or redirection to the original Idp for users to authenticate. The screenshot below shows the user desktop experience, which is what a user would see when logging in from portal.office.com, for example:

The QR code capability is part of the Ivanti UEM client on mobile – no additional MFA app required. Should users run into an issue with authentication, they will be able to get themselves up and running or be able to provide clear information should they need to contact the help desk.
In my next article, I will cover the last main pillar of infrastructure – Mobile Threat Defense – before we move on to devices.
