The User: Always Your Weakest Link
The Verizon Data Breach Investigations Report (DBIR) is one of the most respected annual reports in the security industry.
Every year, the Verizon Research, Investigations, Solutions and Knowledge (RISK) team, one of the largest IT investigative entities in the world, shares deep insights into the state of cybersecurity for the year, including the largest trends.
In 2017, the team found phishing is used in more than 90 percent of security incidents and breaches.
And at equally alarming rates, users with their many devices are falling victim to ransomware and other malware via these user-targeted attacks. According to Verizon, 30 percent of phishing messages were opened in 2016—up from 23 percent the year before—and in 12 percent of those events users clicked to open the malicious attachment or link.
The Verizon RISK team highlights the rise of a three-pronged phishing attack:
- The user receives a phishing email with a malicious attachment or a link pointing to a malicious website.
- The user downloads malware, which attackers can use to look for secrets and internal information, steal credentials to multiple applications through key logging, or encrypt files for ransom.
- Attackers can also use stolen credentials for further attacks: for example, to log into third-party websites like banking or retail sites.
So, how is it that even the biggest corporations out there, with what one can only imagine are high-powered security tools in the arsenal, still fall victim to these attacks?
For one thing, many of the tools in place aren’t protecting the most vulnerable assets.
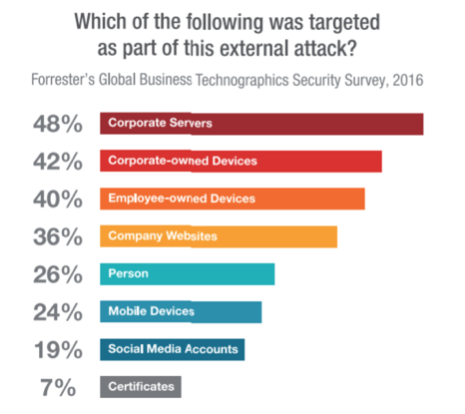
For its 2016 Global Business Technographics® Security Survey, Forrester surveyed 192 network security decisionmakers whose firms had an external security breach in the past 12 months (1,000+ employees). As part of that survey, they asked respondents which aspects of their infrastructure were targeted in the external attack. The results showed definitively that it’s the clients and servers in your network that need to be your primary focus—not the perimeter of your IT environment.
Unfocused Security Strategies? They Lead Only to Expense in Depth
Unfortunately, even if you have the tools in place to protect against these threats, they remain just a few of the many you’re configuring and managing daily. Network firewalls, web application firewalls, intrusion prevention systems, vulnerability scanners… oh my! Device sprawl is costly, and IT teams spend too much time managing these devices—time taken away from working with Security to protect against and respond to real threats to the environment.
Where Do We Go From Here?
Try focusing more on the tools you need to take on most cyber intrusions today. We call it getting back to basics. Patching, for example: Make sure you have a plan in place for patching comprehensively and efficiently, and that you’ve considered the solutions needed to help support your security initiatives when patching isn’t an option. To see why malware protection is more important than ever, click back to the first blog in the series: Malware Protection Against Today’s Extreme Cybersecurity Threats.
And for an even fuller picture of the cybersecurity landscape and the tools that need your focus today, check out our white paper: What to Do BEFORE All Hell Breaks Loose.
