Fighting Ransomware: Using Ivanti’s Platform to Build a Resilient Zero Trust Security Defense – Part 2
Within the initial blog in this series, we discussed ransomware attacks and their remediation on Android mobile devices. Part 2 addresses potential ransomware exploits and their remediation on iOS, iPadOS mobile devices and macOS desktops.
iOS and iPadOS Exploits
The quickest method to check for the presence of malware on your iPhone, iPad or macOS devices is to look for the presence of an unknown configuration profile within the Settings > General > VPN & Device Management settings. Malicious third-party apps commonly sideloaded from non-sanctioned internet websites, or from an infected personal computer, or downloaded from package managers like Cydia or Sileo along with unofficial app stores like TweakDoor (formerly TweakBox) or TutuApp, will add their own configuration profile into the Device Management settings. Package managers, commonly installed after performing a jailbreak of your iOS or iPadOS device, and unofficial app stores that do not require a jailbreak, are repositories for alternative apps, tweaks, and software tools to customize your Apple iDevice. Often these third-party apps have not been rigorously tested for vulnerabilities and can contain malware and malicious exploits that can then take complete control of your device without you knowing.
Apple’s mobile device management (MDM) enables your company’s IT department to remotely enroll and deploy corporate and personally owned iOS, iPadOS or macOS devices over-the-air using a unified endpoint management (UEM) platform like Ivanti Neurons for UEM by deploying a root MDM profile within the same Device Management settings. UEM then fully manages, distributes applications and content, and enforces restrictions and security configurations to these managed devices.
A configuration profile can contain many payloads that store key value pair settings for MDM, with a partial list below. The link to the full itemized list is located here. The good news is as of iOS version 12.2 and later, the profile must be manually installed and then trusted by the user as additional security steps to explicitly approve its installation within the Device Management settings. The partial list includes:
- Restrictions on device features
- Credentials like identity and chain of trust certificates, secrets, and keys
- Wi-Fi profiles
- VPN profiles
- Email server and Exchange settings
- LDAP directory service settings
- CalDAV calendar service settings
- Web clips.
The other good news is these suspicious or untrusted configuration profiles, malware, and other malicious exploits including the Pegasus spyware will be detected by Ivanti Mobile Threat Defense (MTD) and trigger compliance actions like block access to corporate resources or quarantine actions on the device. Ironically, another indication of the presence of a threat on your mobile device is as part of a quarantine compliance action, UEM provisioned managed apps and their content are removed from an iOS or iPadOS device to prevent data loss. After the threats are removed, the managed apps are restored to allow the user to continue to be productive. (See video below that demonstrates this capability.)
macOS Exploits
Apple macOS desktop devices are also not immune from malicious exploits as evidenced by the list of high severity arbitrary and remote code execution vulnerabilities within the Common Vulnerabilities and Exposures details database. Fortunately, security updates exist for these known and former zero-day vulnerabilities.
More recently, a new variant of the AdLoad malware has been detected out in the wild and been able to evade Apple’s built-in malware XProtect scanner. Adload is a trojan, specifically targeting macOS platforms and is currently used to push malicious payloads like adware, bundleware, and Potentially Unwanted Applications (PUAs). It is capable of harvesting system information that can then be deployed to the infected remote web servers under the control of these malicious threat actors. Other macOS malware strains have been able to bypass XProtect as well and infect macOS devices with chained malicious payloads that exploited zero-day vulnerabilities to evade Apple’s File Quarantine, Gatekeeper, and Notarization security checks. Future versions of AdLoad can also evolve into dropping exploit kits that can harvest your personal information, perform lateral movement onto the network, and potentially ransomware.
iCloud Exploits
Back in June of 2014, an iCloud ransomware attack succeeded with victims in Australia, New Zealand, and the United States.
On infected iOS, iPadOS devices and macOS laptops, their lock screens were overlaid with a demand for payment message to unlock them. How did the malicious threat actors pull this off? Personal user account information was harvested using sophisticated phishing tactics and brute-force password cracking techniques from vulnerable iCloud accounts.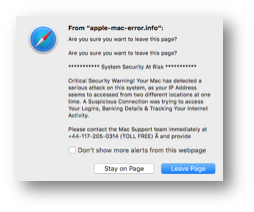
These threat actors used the Find My iPhone, Find My iPad, Find My Mac, or Find My iPod services within iCloud that allow the owner to try to locate their lost device from any web browser. If the lost device were still connected to the internet, the rightful owner could display a message on the screen instructing the person in possession of the device to contact them, remotely set a locking PIN (Personal Identification Number) or wipe the contents of the device.
Once the threat actors obtained the victim’s iCloud account credentials, they remotely changed the PIN and locked the device from the rightful owner. They could then display a ransom message demanding the $100 payment to unlock the device.
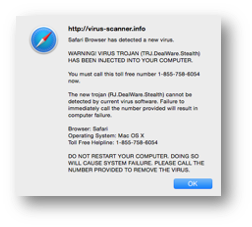 Other similar exploits include fake antivirus support pop-up messages that inform the user to call a telephone number to remove the malware. Victims would then be coerced to pay money to remove the malware from their devices or laptops. The simple solution was to restore from a Time Machine backup.
Other similar exploits include fake antivirus support pop-up messages that inform the user to call a telephone number to remove the malware. Victims would then be coerced to pay money to remove the malware from their devices or laptops. The simple solution was to restore from a Time Machine backup.
The good news is iCloud exploits have decreased in severity and total count in recent years. Although, credential theft and ransomware attacks, some leveraging the same machine learning (ML) artificial intelligence tactics and techniques applied by reputable security researchers, are now used by nation-state backed advanced persistent threat (APT) actors to evade detection and cover their tracks after a successful data breach, have gone up dramatically in the Everywhere Workplace. According to the Verizon 2021 Mobile Security Index, there was an increase of 364% in phishing attempts in 2020 versus 2019. That is mind blowing! What will the outcome for 2021 reveal?
Additional iOS, iPadOS and macOS Remediation
These settings are applicable within the iOS, iPadOS and macOS device:
Apple devices require a 6-digit, 4-digit, or random length alphanumeric passcode as the entropy source to initiate the Data Protection mechanism that leverages file-based encryption on iOS and iPadOS devices, and disk volume encryption for macOS desktops. The stronger the user passcode, the stronger the encryption key and lessening the likelihood of a successful brute force attack by malicious threat actors. Unified endpoint management platforms like Ivanti Neurons for UEM and Ivanti Mobile Threat Defense (MTD) can enforce strong and complex passcodes onto the managed device.
Only download apps from the iOS or Mac App Stores.
If your company employs a UEM platform and deploys an enterprise app store, download apps from the company app store only, as well.
These settings are configured within Ivanti UEM Neurons for UEM or MobileIron Core:
- Create a Software Updates configuration to automatically update to the latest available iOS, iPadOS or macOS version for the device. For iOS and iPadOS only, Ivanti MTD can also enforce that the latest OS version is running on the device and if not, alert the user and UEM administrator that the device is running a vulnerable OS version and apply compliance actions like block or quarantine until the device is updated.
- For macOS desktops, create a FileVault 2 configuration to enable volume-based encryption.
- For iOS and iPadOS devices, enable Ivanti MTD on-device (using MTD Local Actions) and cloud-based to provide multiple layers of protection for phishing (Anti-phishing Protection) and device, network, and app level threats (using the Threat Response Matrix within the MTD management console).
- For macOS desktops, augment the built-in malware scanner by also installing a reputable antivirus agent that updates its detection signatures and engine regularly.
- For BYOD (Bring Your Own Device) deployments, create a deny list of disallowed apps on the device. For company-owned devices, create a allow list of allowed apps that can be installed on the device.
- Backup data automatically onto a cloud storage provider like iCloud, Google Drive, OneDrive, Box or Dropbox. Make secondary and tertiary copies of backups using two or more of these personal storage providers since some offer free storage. Also, backup personal data onto a local hard drive that is encrypted, password-protected and disconnected from the device and network.
- Create a Wi-Fi configuration that enables WPA3 Enterprise for your wireless connection when you are back in the office. At home, enable WPA3 Personal on your home router to secure your wireless connections from eavesdroppers.
- Create a Web Content Filter configuration to limit access to adult content and specific websites prescribed by your company’s security and acceptable use policies. Ivanti UEM and MTD also provide a robust and multi-layered anti-phishing protection that updates the on-device engine’s database every 8 hours and is augmented by the cloud-based lookup engine’s database, which is updated every hour.
- Create an Encrypted DNS (Domain Name System) configuration setting that enables DNS over HTTPS (DoH) or DNS over TLS (Transport Layer Security) (DoT) to encrypt and secure your DNS queries.
- Configure a VPN client on a device like MobileIron Tunnel, Ivanti Secure Connect or Zero Trust Access to protect sensitive data-in-motion between the mobile device and MobileIron Sentry or Connect Secure or ZTA gateways.
- Enable Ivanti Zero Sign-On (ZSO) for conditional access rules like trusted user, trusted device, and trusted app authentication to critical work resources on-premises, at the data center, or up in the cloud. Also, enable MFA (Multi Factor Authentication) using the stronger inherence (biometrics) and possession (device-as-identity or security key) authentication factors. Passwords and PINs can be phished, guessed or brute forced.
In the third blog in this series, we will discuss ransomware attacks and remediation of Windows 10 laptops and desktops. Stay tuned.

