Managing Security Threats Using a Risk-Based Approach
Since the pandemic began its felt like life has been viewed through the lens of continual risk management, “Should I go to the store/pub/shops/cinema”. What’s the risk? What’s the value of taking the risk, how do I mitigate as much of the risk as possible?
With the covid rules relaxing in Australia live in-person conferences are now rolling out so it was with excited anticipation I recently attended the CISO Sydney event to talk about risk!
The topic was not covid risk unsurprisingly but rather: ‘Gain Compliance Using a Risk-Based Approach with Less Effort’. In this blog I’m going to detail how you can achieve this.
Addressing the Skills Shortage with Automation
We have a massive shortage of cyber security professionals in Australia, it’s estimated we need 18,000 in the next four years! For those looking it’s tough to find new hires, it’s also a competitive market so holding onto the skills you have is a challenge, plus they are expensive resources so most organisations can’t afford nearly as many as they need.
So, the logical approach is to do more with less, a topic that really resonated with the conference attendees as we discussed how to prioritise their vulnerability management (VM) programs.
Most of the CISO’s in the audience advised they used one or more VM scanners to identify all the weaknesses in their environment, the challenge came in trying to respond to what was found. The common story being the list gets longer every month and the team can’t keep up, and the work is not that rewarding. It’s a common theme resulting from the impact of covid on the workforce, that unhappy workers tend to find interesting work elsewhere if you can’t satisfy their needs.
What’s the Vulnerability Challenge?
There are 250k vulnerabilities in the National Vulnerability Database (NVD). What’s actually important is how these can be exploited:
- Less than 20% of those are actually weaponised and could be used to breach your organisation.
- Less than 3% use remote code execution (RCE) and privilege escalation (PE) exploits which are the really dangerous ones, 80% of all breaches use these types of attacks.
- If ransomware is your biggest fear only 255 CVEs relate to its use, are you sure you know which they are?
So what’s the takeaway from all these facts and figures?
Well, the problem is if you don’t focus in the right area, you can spend a lot of time, resources and money remediating vulnerabilities that your organisation is very unlikely to be breached by, and you won’t reduce your attack surface significantly.

Apply a Risk-Based Lens to the Problem
Risk Based Vulnerability Management (RBVM) was the number two security project for 2021 based on Gartner insights, with the point being to “focus on vulnerabilities that are actually exploitable”.
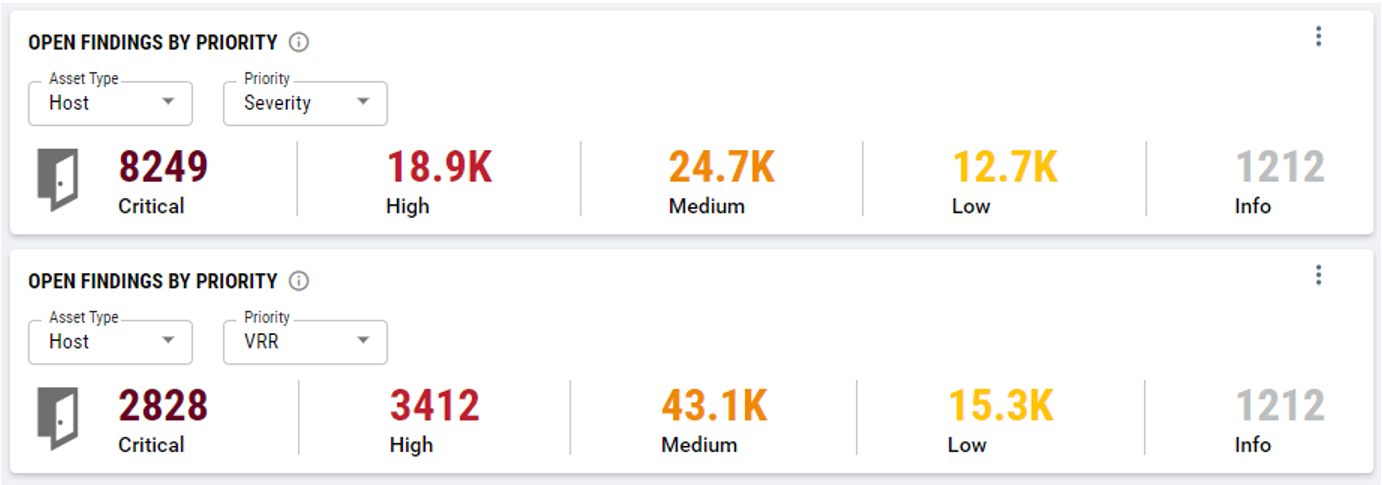
Below I have included some data from a customer we’ve recently worked with.
The top analysis shows data that comes from their VM scanner, it illustrates that they had over 27,000 Critical and High severity items to resolve, an insurmountable task for their security team, the reports to the Senior Executives were worse every month and people were burnt out with no progress being made.
Compare this to the results when they used a risk-based approach to prioritise based on those that were weaponised, had RCE/PE exploits, were trending, or, had ransomware exposure. The customer could focus on the Critical and High 6,240 items that were their biggest risk. This meant a huge 75% reduction in their workload, so they could focus on reducing the actual attack surface of the organisation which made a significant impact.
Is Ransomware our Biggest Threat?
At the CISO conference one of the topics spoken about by the Minister for Home Affairs Karen Andrews and the head of the Australian Cyber Security Centre (ACSC) was the threat ransomware poses. This was detailed in a report available on the ACSC website: 2021 Trends show increased globalised threat of Ransomware.
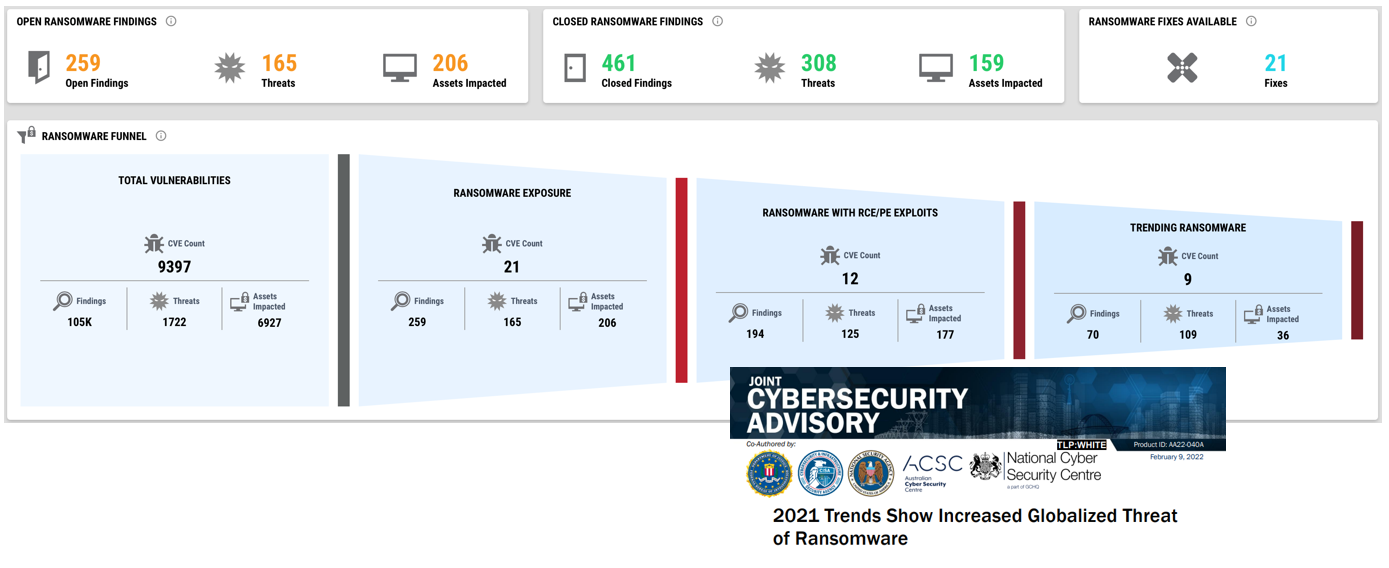
If you look at your VM data through this risk-based lens and you can prioritise based on threat, you can gain visibility into exactly where you are vulnerable to ransomware attacks and should focus effort to improve your security posture.
In this example the security team can provide visibility to their executive team to illustrate the limited exposure they have to ransomware attacks. Of the 10,000 vulnerabilities in the environment across 7,000 devices, only 206 devices and 21 vulnerabilities need attention. It’s also possible to see in green the stats the team achieved to improve protection against ransomware.
Our Prioritisation Offer to You
If you are struggling in a world of too many vulnerabilities and prioritisation with an ability to automate workflows, assignment and service ticket integration doesn’t meet your requirements while your attack surface continues to expand then please get in touch. The only solution isn’t to increase the size of your security team.
Ivanti has proven with customers worldwide that we can help reduce cyber risks with less manual effort.
Provide the Ivanti team an output from any vulnerability management tool and within a few hours we can show you how we can prioritise it, giving you three key outcomes:
- Reduce your workload by up to 80% by focusing on risk
- Reduce the cost to deliver your vulnerability management program through risk-based prioritisation
- Reduce your attack surface faster to reduce the risk of breaches and ransomware infections
Reach out via email to [email protected]

