Is Your Organisation Ready For The Data Breach Notification Changes?
Nobody wants to contact a customer, and be the one to deliver the news:
“sorry, we got hacked, and your personal records were stolen”.
Anybody getting that news is not likely to be a customer much longer. The next thing they are likely to do, is jump on social media, and ‘thank you’ publicly.
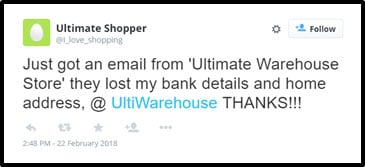
Then, when the media hears about it, you may just find your company name on the front page of the news for the wrong reasons.

If you fail to secure access to customer data, 2018 is the year when you have to notify customers if you have a data breach.
Fundamentals the Notifiable Data Breach Scheme
From February this year, changes to the Australian Privacy Act, mandate organizations must notify affected parties when their data has been accessed by an unauthorized party.
Where an organization, be it government or private. Maintains a repository of customer data. When that data is accessed by any unauthorized party, and harm is likely (more on this later), the individual/s must be notified.
Who is covered by the scheme?
Any organization who is today bound by the Australian Privacy Act, will also be subject to the Mandatory Data Breach Notification Scheme.
This includes any government organization, private business or non-profits generating over $3 million in revenue per year.
Will I really have to notify anyone?
Based on the very specific wording of the act, if customer data is accessed by any unauthorized party. Be it an internal employee who should not have access to a system, or an external entity. The same process must be followed to investigate and decide if notification is required.
The Data Breach Notification Scheme hinges around two key points on your requirement to notify.
- Can you remediate the situation and ensure all accessed data is secure?
- Is harm likely to the individual based on the access?
For this article, we will focus on unauthorized access to data by an external party.
Can we remediate?
Imagine a mobile phone or laptop was lost. The device was encrypted and to access it a complex password is required. An organization could form a case, to say the issue has been remediated by your strategic decision to encrypt and secure that device, and you are confident nobody can access any local data.
Now imagine one of your employees opens an email, and clicks a link from Australia Post. That email was not really from Australia Post and it downloads a malware payload. The cybercriminal now has a backdoor to your organization, and through that door they exfiltrate data looking for anything they can use to sabotage, blackmail you with, or sell to the highest bidder.
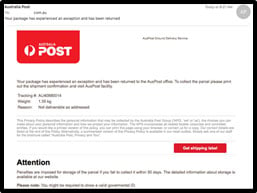
In this scenario, you have lost control of customer data that you will never gain access to again.
This is a common situation faced by organizations every day, with cyber criminals targeting users through social engineering and phishing techniques with the sole aim of exfiltrating your data. With the changes to the Privacy Act. You are now bound, if harm is likely, to notify anyone whose data was lost.
Is harm likely
The definition of harm from the Office of the Australian Information Commissioner (OAIC) covers physical, psychological, emotional, financial, or reputational harm as being reasons to notify of data breach.
A few examples may include loss of data regarding:
- A therapist who has notes on a patient’s job dissatisfaction and stress
- A quote for a customer who is looking to change service providers in a sensitive market
- Travel details for a customer including passport information
- Medical test results to be sent to a customer
- Details of a credit check sent in by a customer
In each of these scenarios the information contained becoming public knowledge, could lead to serious harm to someone in numerous ways.
Preparing for Data Breach Notification: Prevention is Better
The reputation of any organization is directly linked to its success and ability to expand and grow. The best way to protect this reputation is ensure you safe guard yourself against unauthorized access of customer data.
The Australian Signals Directorate (ASD) are charged by the Australian Government to provide a security framework to help our government protect themselves against cyber threat.
The ASD detail 4 key strategies that will help an organization protect themselves against 85% of targeted cyber threats, these 4 strategies in priority order are:
- Application Whitelisting
- Application Patching
- Operating System Patching
- Minimize Administrative Privileges
(https://www.asd.gov.au/infosec/top-mitigations/top-4-strategies-explained.htm)
Ivanti are in the unique position in being able to support our customers in implementing all 4 of these strategies. Implementing all 4 strategies with one vendor brings the benefit of technology integration, less vendors to deal with and of course, price.
At Ivanti we have a diverse number of state & federal government and private organizations using our technologies today. Through the simplicity and ease of deployment. Organizations are able to protect their users, and the business, against cyber threats using the Ivanti endpoint security platform.
Moving in to 2018 this will protect organizations against having to deliver that difficult communication to a customer, to tell them their data was lost.
What Next?
Now you know a bit more about the new Privacy Act, it’s time to act, and protect yourself.
Contact Ivanti and we can provide a tailored demonstration of how we help organizations better protect their endpoints in line with security frameworks such as the ASD. Or, take a look at our dedicated Ivanti ASD compliance page on our website
You may just avoid damaging your reputation forever.

