State-Sponsored Hacking out of the Shadows and Into a Business Near You
Last week the Minister for Law Enforcement and Cyber Security made a media release placing responsibility for a wide-scale cyber incident firmly at the feet of Russia. Governments around the world allege Russian state-sponsored hackers infected Cisco routers globally, targeting government agencies and critical infrastructure providers.
The incident is thought to have targeted up to 400 Australian businesses; was yours one of those?
Which countries lead hacking efforts?
State-sponsored hacking is widely associated with major players like Russia, China, and the USA. The reality is the bar is so low now that even developing countries are getting involved. They have a lot more to gain than others: technology they don’t have, bulk personal information, or upcoming foreign investment. And while Russia takes the headlines, these countries can often fly under the radar.
Figures published in 2017 showed the top 5 countries originating cyber-attacks were:
- USA
- China
- Brazil
- India
- Russia
Three of the names on that list I am sure most people would pick; the other two, not so much.
What do state-sponsored cyber hackers want?
Why are we targeted? What do they want? Sometimes it’s money, but when it comes to state-sponsored hacking it’s intellectual property and knowledge, including foreign policy details, large government/private sector projects going to tender, business processes, contracts, research, and plans for a new product or technology.
The reality is anything can be valuable in the right context.
The slogan for the Australian Signals Directorate (the ASD, tasked with helping to protect Australian government and business from cyber threats) is Reveal Their Secrets – Protect Our Own. This simple slogan shows the true value placed on Australia’s intellectual property and that of other countries.
What’s the target?
While the highlighted attack was targeting hardware, in 2017 the human attack surface reached 3.8 billion people, making humans the targets now and not machines. The 2017 threat report from the Australian Cyber Security Centre (ACSC) showed an overwhelming number of the reported incidents were user targeted, with malicious email and spear phishing leading the stats.
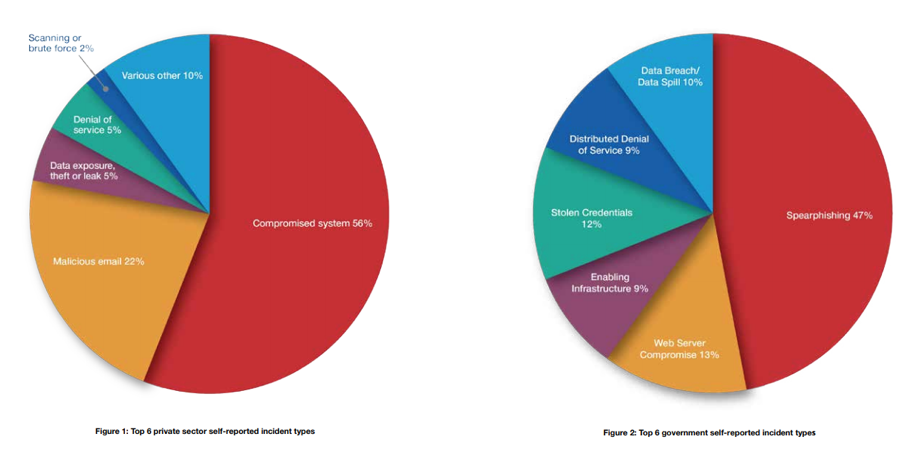
ACSC Threat Report 2017
How do you protect yourself?
The ACSC report details how implementing foundational cyber security controls is a true business investment:
"Prevention is better than a cure. The initial cost of implementing robust cyber security mitigation and incident management strategies, such as ASD’s Essential Eight, may seem high for some organisations, however, it represents an important investment, reducing long term costs and risk."
Ivanti can help our customers implement 6 of the ASD Essential 8 security controls using just one vendor.
| Essential 8 Control | Ivanti Solution | |
| Application whitelisting | Block zero-day malware and ransomware | Ivanti Application Control |
| Patch Applications | Protect against the known vulnerabilities | Ivanti Patch |
| Patch the Operating System | Protect against the known vulnerabilities | Ivanti Patch |
| Restrict Admin Privileges | Protect against lateral privilege attacks and slow down successful attacks | Ivanti Application Control |
| Configure MS Office Macros | Only allow trusted known good macros | Ivanti Environment Manager/Application Control |
| User App Hardening | Block or disable vulnerable features or integrations | Ivanti Environment Manager |
| Configure daily backups | Restore critical data in a disaster | |
| Multi Factor Authentication | Ensure the user logging on is who they say they are | |
Operational security?
With a keen focus on what we consider ‘operational security,’ Ivanti has best-of-breed solutions and a suite of technologies aimed at fast and simple deployment with a low cost of management going forward.
Based on our 30 years of experience in the desktop market we understand the desktop, what users need, and how they expect IT to support and empower them.
For more detail on how Ivanti can help your organization implement the ASD Essential 8 security controls, please see our dedicated web page.