What Does Adversaries Weaponising Operational Technology Have to do with the ACSC Essential 8?
I recently read an article from Gartner, Inc. about attackers weaponising your Operational Technology (OT) environment to physically harm people. That really stood out to me. It would be a total shift in the cyberattacks we are used to, which mainly impact big corporations for financial gain. “Who cares” say the public, sometimes forgetting our personal data is being stolen in these attacks.
Examining recent attacks focusing on these types of environments including a ransomware attack on a pipeline in the U.S., that led to thousands stock piling petrol in the fear it would run out (some putting it in carrier bags, potential for human harm?). Also a water treatment facility in the USA where attackers tried to increase the level of sodium hydroxide to poison the water supply. Cyber attacks directly affecting peoples lives and possibly health and well-being!
The question for many organisations responsible for managing this kind of critical infrastructure is changing:
- How do I protect this system from compromise?
- How do I protect our business from reputational damage?
- How do I protect our customers from potential physical harm? (a pre cursor question in Australia to a Notifiable Data Breach)
According to the article I mentioned above, Gartner predicts that by 2023 the financial impact of attacks on OT networks will reach $50 billon.
Defence in Depth Frameworks
For a long time, we have spoken about defence in depth frameworks, having several layers and processes to help protect us against attack so if one control is penetrated, we are still protected.
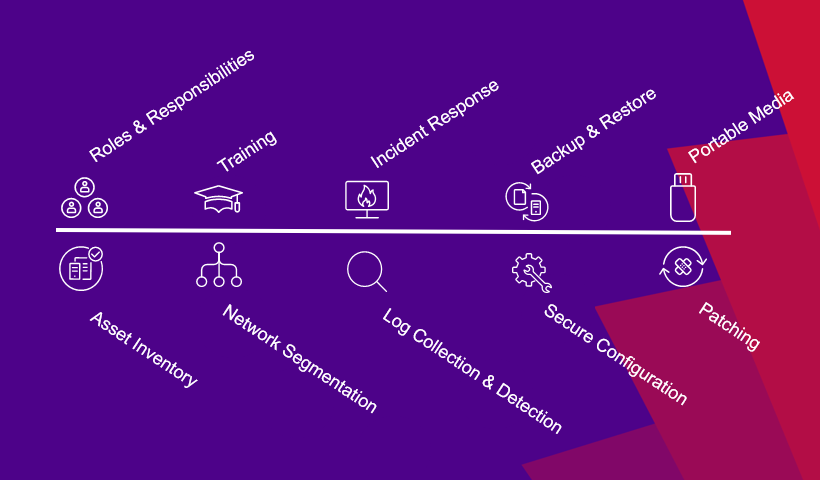
In that Gartner article, it talks of 10 key security controls /processes that are recommended to be implemented/documented in OT environments. Unsurprisingly, there are several of the ACSC Essential 8 controls defined as recommended by the Australian government.
I wrote a blog last year on 10 years on from Stuxnet one of the most infamous OT breaches that all stemmed from a USB device with a piece of malware on it. Could that be executed in your OT today? Could that have gone slightly differently and caused a real incident to harm people?
Fast & effective patching is still a real struggle in 2021. Due to the volume and severity of vulnerabilities many organisations are starting to look at a risk-based prioritisation. This can mean checking two or three vulnerability scanners, trawling threat feeds and cross checking a bunch of spread sheets of assets to work out a plan, let alone deploy a patch in the recommended 48 hrs.
Having said all that, based on conversations I have had with organisations most do have many of these security controls in place at differing levels of maturity and success.
If organisations have these critical security controls in place what’s the issue?
The security controls implemented are often fractured, siloed and integration can be difficult when there are so many point solutions and vendors involved in the security strategy.
A support issue can have three vendors trying to sort out whose technology is at fault or often who can I point the finger at. Upgrading any one of those five-point solutions may break the integration, so I can’t upgrade anything for fear of what might happen.
The point here is its too complex, too expensive and still too manual.
How can Ivanti help secure your operational technology?
The breadth of Ivanti solutions can provide customers defence in depth across a range of capabilities. We deliver seven of the ACSC Essential 8 Controls plus supporting controls like asset management and inventory. We can also support six of the ten security controls Gartner recommends for an OT environment.
With Ivanti’s acquisition of RiskSense we can provide Risk Based Vulnerability Management. If you have multiple vulnerability scanners for infrastructure, network and applications and can’t see the key risks that pose the greatest threat, and, you don’t know where to focus your efforts and prioritise based on risk of exploitation and ransomware – then we can help.
Here are the security controls aligned with those recommendations that Ivanti can support you with.

If your vision and strategy align to the following three key outcomes, then partnering with Ivanti is going to be of value:
- Less vendors to deal with to reduce cost and complexity
- Integrated security solutions and outcomes
- Automation of common security operations
If you want any more information check out our security solutions page on the website, or if you are looking for some basic foundational controls check out our ACSC Essential 8 page. Or reach out and ask me a question [email protected].
1Source: Gartner, “Gartner Predicts By 2025 Cyber Attackers Will Have Weaponized Operational Technology Environments to Successfully Harm or Kill Humans,” 21 July 2021.

