With Microsoft Endpoint Configuration Manager and Intune you may have your Microsoft software covered. But what about third-party applications such as Adobe Acrobat Flash and Reader, Google Chrome, Mozilla Firefox, and Oracle Java? They account for 86 percent of all software vulnerabilities, and are the apps and browser add-ons hackers target most. How do you keep track of, remediate, and report on all your vulnerabilities—without breaking the bank or creating headaches for IT?

Full‑coverage patching for Microsoft Endpoint Configuration Manager
Extend Configuration Manager
Full‑Coverage Patching
With Microsoft Endpoint Configuration Manager and Intune you may have your Microsoft software covered. But what about third-party applications such as Adobe Acrobat Flash and Reader, Google Chrome, Mozilla Firefox, and Oracle Java?
They account for 86 percent of all software vulnerabilities, and are the apps and browser add-ons hackers target most. How do you keep track of, remediate, and report on all your vulnerabilities—without breaking the bank or creating headaches for IT?
Simplified Configuration
Built-in Scalability
Greater ROI
Best in class patch management
Ivanti Patch for Configuration Manager uses your existing Microsoft Endpoint Configuration Manager (MECM) and Intune consoles to patch your most vulnerable applications. Our plug-in instals in minutes. All you do is choose what to publish from our extensive catalogue, and the packages show up alongside Microsoft updates. You can use the systems and workflow you know so well, and our solution scales right along with configuration manager.
Features and capabilities
Patch all software with the tool you know well
Microsoft’s Endpoint Configuration Manager and Intune are working for you. So what if you could add comprehensive third-party patching to it—without adding infrastructure or training?
Native patch management plug-in
There’s no need to deploy extra servers or additional agents other than Microsoft Endpoint Manager’s configuration and Intune consoles. What’s more, the installation is easy, fast, and verifies your configuration for a better user experience.
Automated patching
Our solution checks the latest patch definition automatically. You can also set it to publish new patches automatically. It even has logic that expires superseded patches and helps with installing difficult patches such as Java.
Award-winning patch catalog
Select and publish patches from a comprehensive catalog of vendors that includes Adobe, Apple, Citrix, Google, Mozilla, Oracle, and much more.
Expert research team
Our patch content engineers spend countless hours ensuring all patches are thoroughly tested before we release them to you. Secure your environment successfully: take advantage of our years of experience delivering accurate, timely patch data.
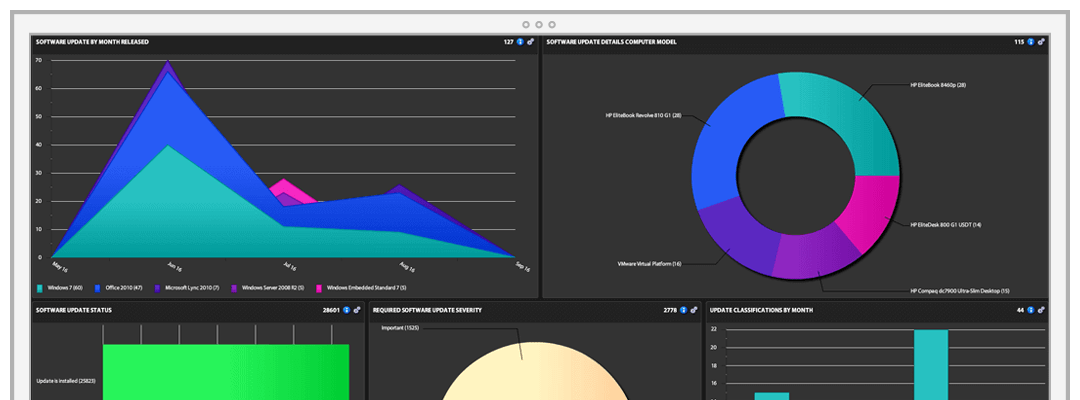
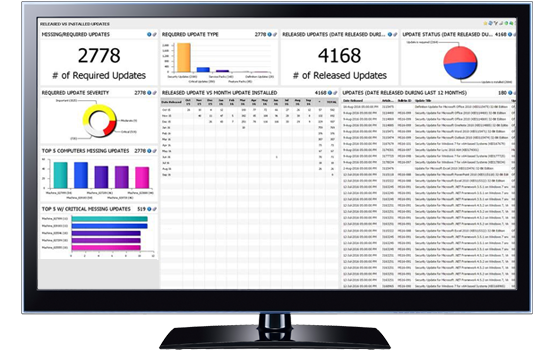
Integrated reporting features
How do you demonstrate patch compliance throughout your organization? Through the reporting features inside the Microsoft Endpoint Configuration Manager and Intune consoles, you can view and verify delivery and installation of third-party patches.
Customized patching
Edit and customize individual patches to meet specific company policies. Publish patch metadata separately, for compliance reports and audit requests or to see if a patch needs to be deployed fully.
Patch completely for peace of mind
Third-party patching can be a struggle. Manage risk effectively by ensuring patches are delivered properly.