Invigorate Your Security State with the CIS Top 5
It’s probably no surprise to you that all top cybersecurity threats are on the rise. But why is that? IBM reports that 40 percent of spam contains ransomware and that one in two executives experience a ransomware attack.
In addition—as you’ll read in the information-packed white paper What to Do BEFORE All Hell Breaks Loose: Cybersecurity for Today’s Extreme Threats—the rise in threats is due in part to how much easier it is to take up the mantle of cyber attacker. It’s safe to say that hackers don’t need to knuckle down and apply the Malcolm Gladwell “10,000 hours of practice” principle made memorable in his Outliers book published in 2008.
You Don’t Need to Be Good … at Bad
Today’s exploit kits simplify cyber attacks for even inexperienced hackers. ZDNet reports that hackers can buy easy-to-use “as-a-service” options for attacks for $19.95 per month.
DarkReading cites a report from Carbon Black that ransomware is a $6.2 million industry. Revenue from illicit ransomware marketplaces has soared. Some of the best sellers on the Dark Web include do-it-yourself ransomware kits that range from 50 cents to $3,000, with the median price at $10.50. Hackers don’t need to know how to code to get their business up and running.
These malicious toolkits come with pre-written exploit code and require no knowledge of how it works. Often a simple web interface allows licensed users to log in and view active victims and statistics. These kits may even include a support period and updates, much like legal commercial software.
Impacts on Critical Infrastructure
Hackers today can have a major impact on critical infrastructure worldwide, and their attacks are also growing in sophistication and evolving in intent. For example, WannaCry ransomware crippled computers at hospitals, banks, and businesses around the world. Hospitals in the UK had to turn patients away while they grappled with computers held hostage. NotPetya affected hospitals too—leading to canceled surgeries—and other major organizations like airlines, banks, the Chernobyl nuclear power plant, and a global shipping company, which was forced to shut down container terminals in ports from Los Angeles to Mumbai.
Now’s the Time to Implement Cybersecurity Best Practices
Cyber watchdogs like the Center for Internet Security (CIS) are contributing their knowledge and expertise to identify, validate, promote, and sustain the adoption of cybersecurity best practices. Derived from practices forged from actual experiences at the NSA, the CIS Critical Security Controls both support and reflect many of the other leading sources of cybersecurity guidance.
In particular, the Top 5 CIS Critical Security Controls establish a solid foundation for radically improving an organization’s security posture. That’s why they refer to these as “Foundational Cyber Hygiene.”
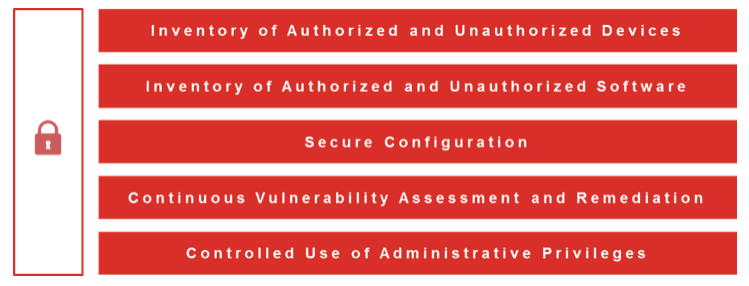
The takeaway is this: with each business-critical asset in your organization, you should compare your existing security controls against the CIS Critical Security Controls. Pinpoint exactly which sub-controls within those you already meet and those you do not. Then, based on identified gaps and specific business risks and concerns, take immediate steps to implement the Top 5 Controls and develop a strategic plan to implement the others.
Download the white paper to learn more. In addition, please join Ivanti, The Chertoff Group, and our partners in Seattle, Washington, on Wednesday, November 8, for our Security Summit where we’ll tackle “Cybersecurity for Today’s Threats.” Register today.

