Three Components Required for a Complete IT Asset Management Solution (Part 3 of 4): Asset Intelligence
Early in the 1970’s, laws were introduced and adopted to fight organized crime. The RICO Act is well known for bringing down many “crime” organizations. One purpose of the RICO Act was to target individuals who were ordering someone else to commit a crime. With the RICO Act in place, law enforcement agents began to focus on the organization, not just individual suspects.
Intelligence focused on the relationships and connections of people who were suspected to be part of the crime organization. Diagrams and charts were created to give law enforcement a clear view of how the organization was structured. Ultimately, this intelligence was used as evidence to show the role of each suspect in the organization and as a result, many crime bosses were convicted for crimes they had ordered someone else to perform on their behalf.
IT Asset Intelligence
IT Asset Intelligence does not focus on the IT asset. Instead, it focuses on the IT asset’s relationships with other IT assets, IT services, licenses, employees, departments, and business objectives. By focusing on asset relationships, IT administrators gain intelligence which allows them to create diagrams and charts that show a clear view of each asset’s origin, role, and function within the organization.
For example, when applying asset intelligence to a laptop, an IT administrator can quickly identify when it was purchased, why it was purchased, who purchased it, who is using it, who was using it, how it has performed, what software is installed on it, when it needs to be updated, and when it should be returned or replaced. For software, IT asset intelligence establishes an effective license position (ELP) which can help an organization stay compliant with their software license agreements.
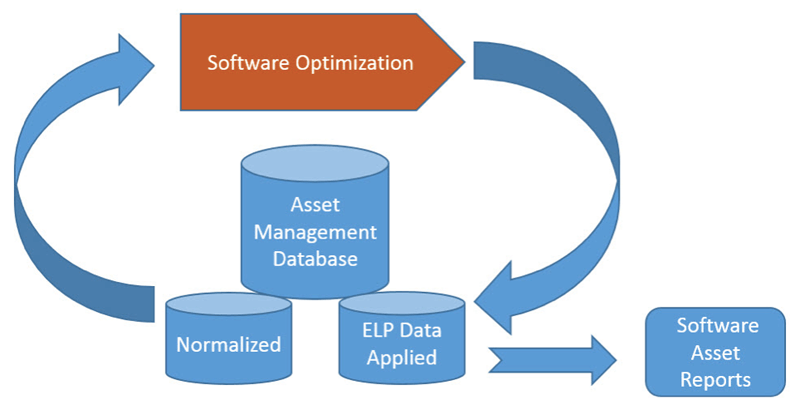
IT asset intelligence is achieved through IT asset normalization and IT asset mapping.
IT Asset Normalization
To ensure that the IT asset database is consistent and accurate, it is important to have a normalization process in place.
In a gated Gartner report titled “Market Guide for Software Asset Management Tools,” Gartner defines normalization as follows:
For example, the first column in this diagram shows raw data as reported from a discovery agent.
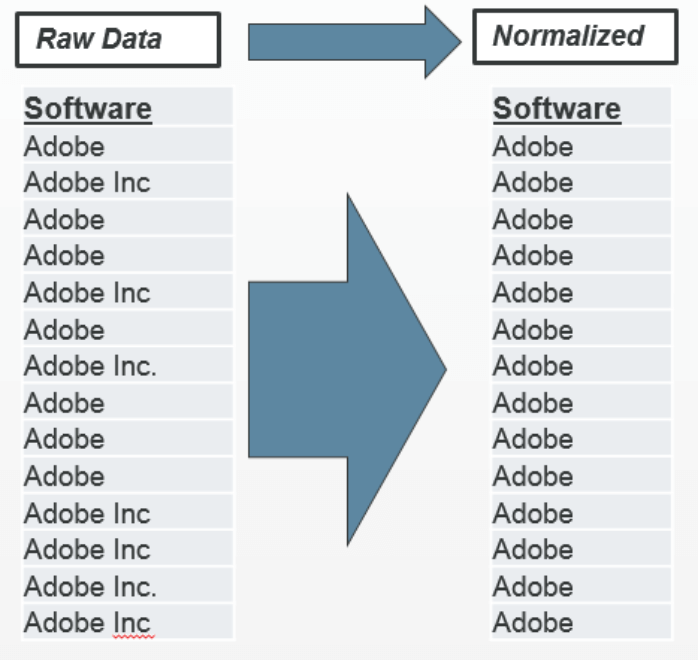
Notice that in some entries, Adobe is reported as “Adobe Inc.”, while in other entries, it is reported as “Adobe”.
Vendors are known for creating these inconsistencies across different versions and releases of their products and as a result, IT asset reports might not be accurate. To ensure consistency and accuracy in the database, it is important to have a normalization process in place that will detect and correct inconsistencies.
When choosing an IT asset management solution, be sure the solution offers normalization capabilities.
IT Asset Mapping
Asset management tools need to be able to map asset information from one table to another. The concept is quite simple when you consider mapping a laptop to the person who is assigned the laptop. However, mapping assets is not always as simple as A=B. When mapping IT assets, it is important to be able to use logic.
For example:
If A = B, Then A = F
If A = C, Then A = G
Take, for example, IT asset location; many IT asset administrators want to know where their laptops are physically located, but they do not always have access to that information or the laptop users are often changing their location. However, asset managers probably have information that could help them find the location of the asset.
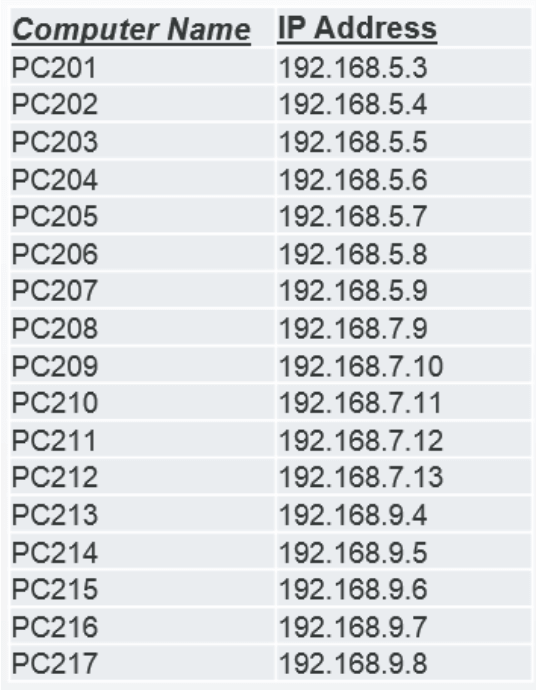
In this example, IP addresses are discovered along with the laptops, then documented in the asset management database.
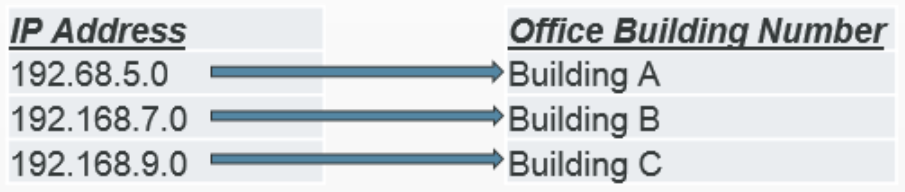
If the asset manager knows that IP addresses are associated with a location, such as a building, logic could be applied to map laptops to the building where the laptops are located.
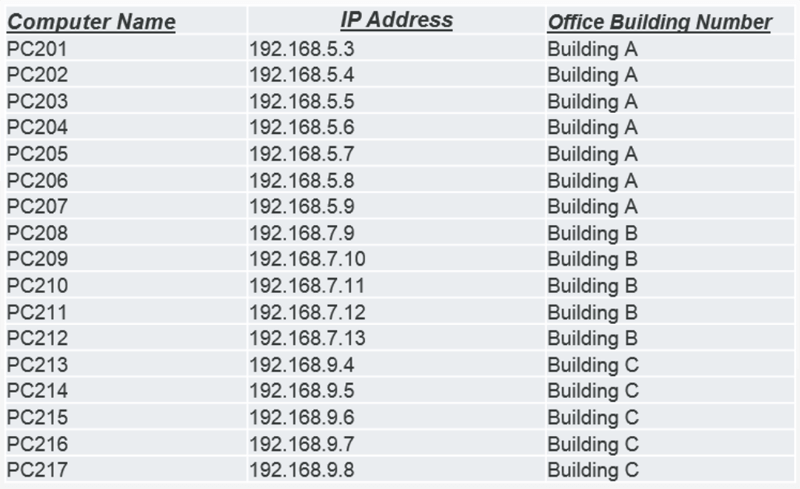
As a result, laptops can be assigned a location in the asset management database, which then enables asset managers to create reports that show the location of each laptop.
Mapping Software to Software Licenses
IT asset mapping becomes much more complicated when mapping software to software licenses. For example, discovered software, such as Microsoft Word could be associated with a license entitlement for Word, or a license entitlement for the Microsoft Office Suite.
Complexity increases when mapping software licenses to software hosted in the data center because licensing models and SKUs for software in the data center are typically complex and are often changed. For this reason, asset management solutions need to be able to map to external sources that contain up-to-date license reconciliation models. Gartner refers to this process as “Reconciliation of External Information.”
Mapping to SaaS
When mapping discovery data to software licenses associated with a cloud (SaaS) solution, it is important that discovery tools are able to monitor and document user activities as well as user access to relevant cloud services to establish an ELP. Applications such as Microsoft Office 365 and Salesforce do not leave a footprint on the end-user devices because these software solutions are hosted in the cloud and accessed through the local browser. No software is installed on the end-user’s device.
Summary
IT asset intelligence data is created by normalizing, then mapping IT assets to relevant information. Asset intelligence establishes the relationships that an asset has with other assets, services, contracts, ELP, departments, cost centers, vendors, warranties, utilization, environment, location, and related business objectives. Asset intelligence is a critical component for a complete IT asset management solution.
Other posts in this series:
- Three Components Required for a Complete IT Asset Management Solution (Part 1 of 4): Six Common Objectives
- Three Components Required for a Complete IT Asset Management Solution (Part 2 of 4): Discovery
- Three Components Required for a Complete IT Asset Management Solution (Part 4 of 4): Lifecycle Management
