July 2023 Patch Tuesday
This month is going to be a painful one, with:
- Multiple zero-day exploits being resolved by Microsoft,
- Some operational changes for Kerberos and Netlogon vulnerability resolutions, and
- A large lineup of third-party updates releasing on and after July’s Patch Tuesday – including Oracle's quarterly CPU and Java updates.
Kerberos and Netlogon Vulnerability Changes
July is going to be a big month from an operational perspective.
A number of changes are going into effect regarding two previously resolved CVEs:
- An Elevation of Privilege vulnerability resolution in Kerberos (CVE-2022-37967), and
- An Elevation of Privilege vulnerability in Netlogon RPC (CVE-2022-38023).
Both CVEs were resolved in 2022, but the code change alone did not resolve the vulnerabilities.
What to expect in July 2023’s updates for Kerberos and Netlogon vulnerabilities
Microsoft outlined a phased rollout of enforcement for both vulnerabilities, due to the fact that they are changing some core behaviors in two commonly used authentication mechanisms.
- KB5020805 outlines the timing of changes for the Kerberos vulnerability (CVE-2022-37967). For July, Microsoft is stepping up to initial enforcement. The earlier changes have been to add the capabilities to address the security bypass and audit logging to show if organizations had systems that needed attention to prepare for the change.
- This July 2023 OS update will default the behavior to Enforcement mode, but still allow an Administrator to override and set Audit mode explicitly.
- The future October 10, 2023, update will remove the Admin override and default to full enforcement.
- KB5021130 outlines the timing of changes for the Netlogon vulnerability (CVE-2022-38023). For July, Microsoft is stepping up to full enforcement. The earlier changes have been to add the capabilities to address the security bypass and audit logging to show if organizations had systems that needed attention to prepare for the change.
- This July 2023 update will remove the ability to override enforcement and allow compatibility mode for RPC Sealing.
- After deploying the July update, Netlogon will fully enforce RPC Sealing.
Multiple Zero Days and Public Disclosures from Microsoft for July 2023
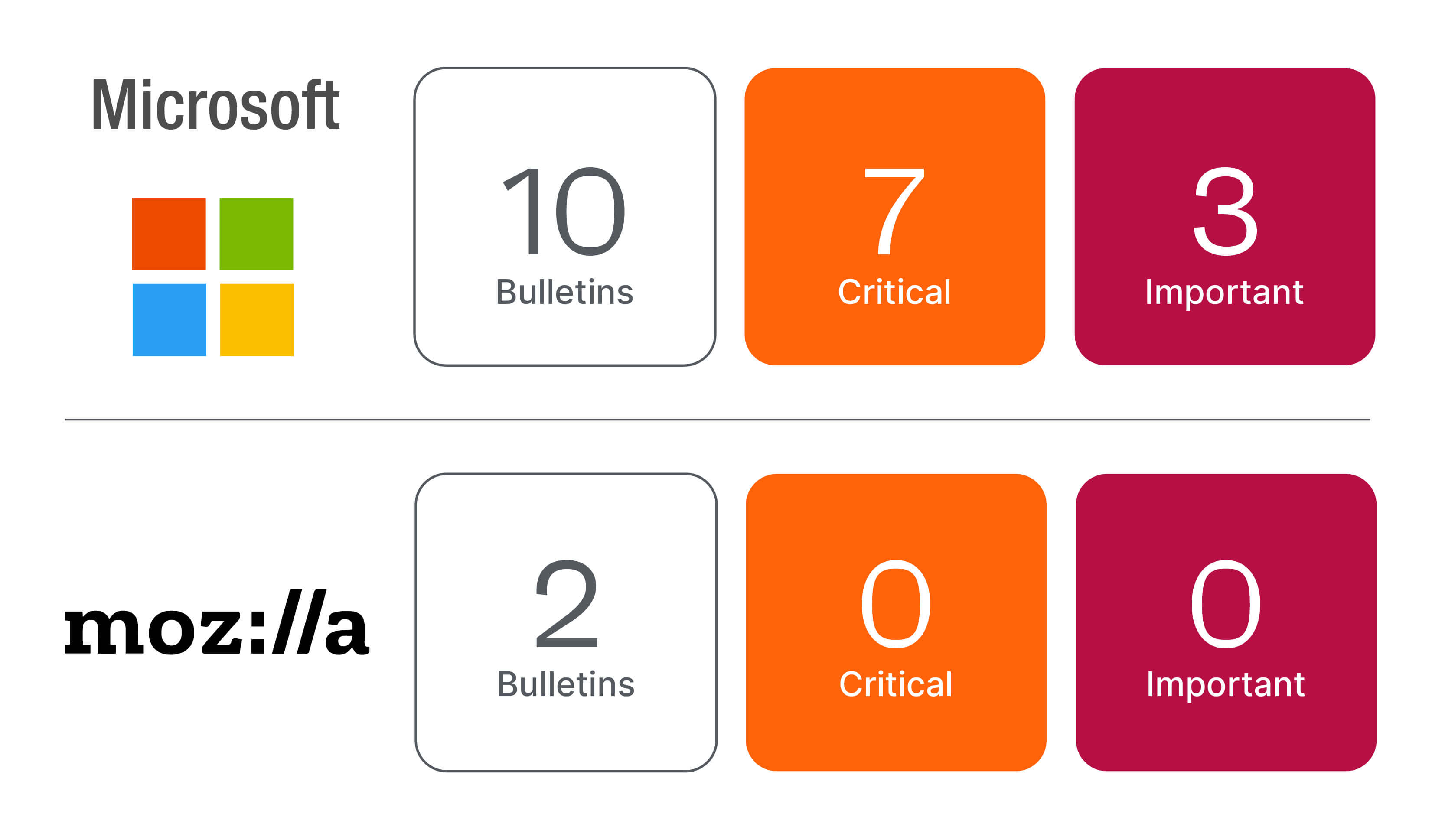
Microsoft has resolved 130 net new vulnerabilities this month, and there are updates to 9 previously released CVEs. Six CVEs and one Advisory have confirmed exploits.
One of the six exploited vulnerabilities released originally in May, and has been updated this month to address all versions of Microsoft Windows.
This month, I'd specifically like to highlight:
- CVE-2023-24932 (Security Feature Bypass - Secure Boot): Critical Confirmed Exploits
- CVE-2023-36871 (Security Feature Bypass - AD): Functional Code Maturity
- CVE-2023-35311 (Security Feature Bypass - Outlook): Critical Confirmed Exploits
- CVE-2023-36884 (Remote Code Execution - Office and Windows HTML): Critical Confirmed Exploits
- CVE-2023-36874 (Privilege Escalation - Windows Error Reporting): Reported Exploits
- CVE-2023-32049 (Security Feature Bypass - SmartScreen): Critical Confirmed Exploits
- CVE-2023-32046 (Privilege Escalation - MSHTML): Important Confirmed Exploits
- Microsoft Advisory ADV23001 - Malicious Signed Drivers
Microsoft CVE-2023-24932 (Security Feature Bypass - Secure Boot): Critical Confirmed Exploits
Microsoft has updated CVE-2023-24932, which is a Security Feature Bypass in Secure Boot.
The CVE was originally resolved in May 2023, but Microsoft has expanded the affected OS versions, and is recommending customers update to the July update on all affected Windows OS version this month. The vulnerability has confirmed exploits in the wild.
The CVSS v3.1 base score is 6.7 and it is rated as Important by Microsoft. However, with confirmed exploits and publicly disclosed functional code, this vulnerability should be treated as Critical.
Microsoft CVE-2023-36871 (Security Feature Bypass - AD): Functional Code Maturity
Microsoft has resolved a Security Feature Bypass in Azure Active Directory (CVE-2023-36871). The CVE is rated as Important and has a CVSS v3.1 base score of 6.5, but the temporal metrics list code maturity as functional.
An attacker would require a low privileged session on the user’s device to obtain a JSON web token. The token could thenbe used to create a long-lived assertion using the Windows Hello for Business Key from the victim’s device.
In this case, the fix is to:
- Update to the July update on all AD FS servers.
- Then, enable the setting required to turn on the EnforceNonceInJWT setting.
- The PowerShell command to enable this setting is provided in the CVE article.
Microsoft CVE-2023-35311 (Security Feature Bypass - Outlook): Critical Confirmed Exploits
Microsoft has resolved a Security Feature Bypass in Microsoft Outlook (CVE-2023-35311). This vulnerability has confirmed exploitation.
The attacker could send a user a specially crafted URL to bypass the Microsoft Outlook Security Notice prompt. The Preview Pane is an attack vector for this vulnerability, but user interaction is required.
Given the fact that phishing a user is a statistical challenge, the priority for getting this fix rolled out is Critical, even though Microsoft’s severity rating is only Important.
Microsoft CVE-2023-36884 (Remote Code Execution - Office and Windows HTML): Critical Confirmed Exploits
Microsoft has resolved a Remote Code Execution vulnerability in Office and Windows HTML (CVE-2023-36884). The CVE is rated as Important, but has confirmed reports of exploitation in the wild and functional code has been publicly disclosed for this vulnerability.
An attacker could create a specially crafted Microsoft Office document that enables them to perform remote code execution in the context of the victim.
Microsoft has not yet released an update to fix this issue, but has provided a configuration level mitigation to block Office applications from creating child processes. Running as least privileged could also help to mitigate the attack and require the attacker to execute additional exploits to elevate their privilege level.
Microsoft has released a blog entry describing steps that can be taken to protect systems until a fix becomes available.
Microsoft CVE-2023-36874 (Privilege Escalation - Windows Error Reporting): Reported Exploits
Microsoft has resolved an Elevation of Privilege vulnerability in Windows Error Reporting (CVE-2023-36874). The CVE is rated as important but has reported cases of exploitation. An attacker – with local access to the target machine with permission to create folders and performance traces on the machine – could gain administrator privileges.
Microsoft CVE-2023-32049 (Security Feature Bypass - SmartScreen): Critical Confirmed Exploits
Microsoft has resolved a Security Feature Bypass vulnerability in Windows SmartScreen (CVE-2023-32049). The CVE is rated as Important, but Microsoft has confirmed reports of exploitation for this vulnerability increasing the urgency to Critical.
The attacker can send a user a specially crafted URL that could allow the "Open File – Security Warning" prompt to be bypassed, opening additional opportunities to further compromise the target system.
Microsoft CVE-2023-32046 (Privilege Escalation - MSHTML): Important Confirmed Exploits
Microsoft has resolved an Elevation of Privilege vulnerability in Windows MSHTML (CVE-2023-32046). Microsoft has rated the CVE as Important and has reports of exploitation in the wild.
An attacker could target a user in a variety of ways, including email- and web-based attack scenarios. If exploited, the attacker would gain the rights of the user that is running the affected application. So, running least privilege would help to mitigate the impact of this vulnerability, forcing the attacker to take additional steps to take full control of the target system.
While IE 11 has been retired, you will see a reference to IE Cumulative updates listed for Windows Server 2008, 2008 R2, 2012 and 2012 R2 due to the MSHTML, EdgeHTML and scripting platforms still being supported.
If you are installing the Security Only updates on these platforms, Microsoft is recommending running the IE Cumulative update as well to fully resolve the CVE.
Microsoft Advisory ADV23001 - Malicious Signed Drivers
Microsoft has released an Advisory (ADV23001) providing guidance on Microsoft Signed Drivers being used maliciously.
Several developer accounts for the Microsoft Partner Center (MPC) were engaged in submitting malicious drivers to obtain a Microsoft signature.
Microsoft has released Window Security updates (see their "Security Updates" table) that untrust drivers and driver signing certificates for the impacted files, and has suspended the partners' seller accounts. All the developer accounts involved in this incident were immediately suspended.
Additionally, Microsoft has implemented blocking detections (Microsoft Defender 1.391.3822.0 and newer) to help protect customers from legitimately signed drivers that have been used maliciously in post-exploit activity.
For more information about how the Windows Code Integrity feature protects Microsoft customers from revoked certificates, see Microsoft Support's "Notice of additions to the Windows Driver.STL revocation list".
Third-Party Updates for July 2023 – Including Java Updates from Oracle
- Mozilla has released updates for Firefox and Firefox ESR.
- Adobe Acrobat and Reader has an update that appears to be non-security related, but has released updates for Adobe InDesign and ColdFusion.
- Google Chrome is likely to update on July 11th or shortly after.
- Oracle’s quarterly CPU (Critical Patch Update) is due to release on July 18, with updates for the lineup of Oracle products – including Java.
As you begin your maintenance this cycle, keep in mind that – after the Oracle Java release – there is a stream of additional updates that will occur, including:
- RedHat OpenJDK,
- Amazon Corretto,
- Azul Zulu,
- Eclipse Adoptium,
- Adopt OpenJDK, and
- Other Java frameworks.
