Protect mobile devices against device, network, application and phishing attacks.
Universal activation
Improve the security posture of your organization by achieving 100% user activation.

Real-time zero-day threat protection for corporate and employee-owned devices.
Protect mobile devices against device, network, application and phishing attacks.
Protect mobile devices against device, network, application and phishing attacks.
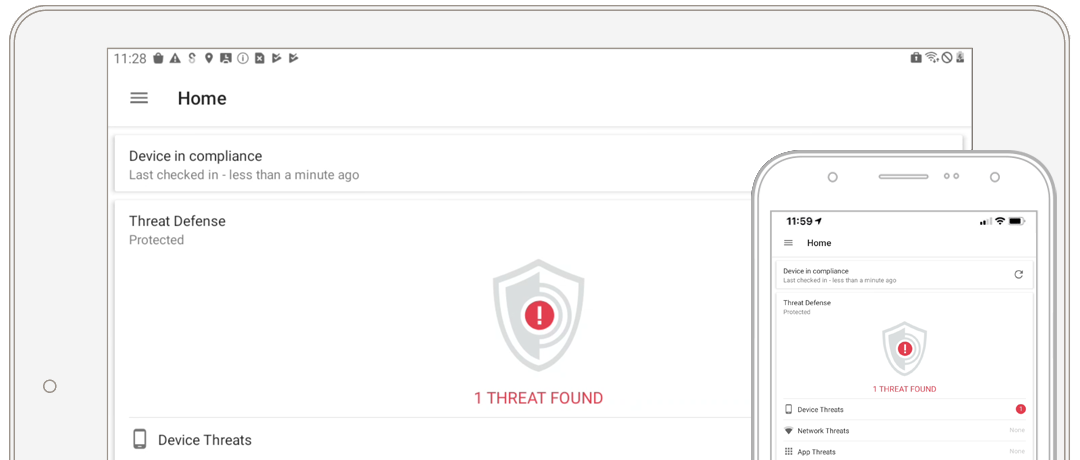
Identify and block phishing and malicious web links in real-time with secure threat intelligence analysis.

Ivanti Neurons for MTD is built into the Ivanti Neurons for MDM and Ivanti Endpoint Manager Mobile clients so that admins can achieve 100% user adoption.

Machine learning algorithms provide immediate and ongoing visibility into malicious threats across all protected Android, iOS and iPadOS devices.

Ensure only safe apps are deployed on employees’ mobile devices.

Stay one step ahead of mobile threats with a range of administrative features.

Improve your mobile security posture without sacrificing user productivity.

Improve the security posture of your organization by achieving 100% user activation.
Proactively protect against unnecessary expenses by reducing exposure, fines and reputation damage.
Machine learning algorithms provide ongoing threat intelligence and secure threat intelligence detects and blocks zero-day phishing and malicious web threats.
Leverage threat assessment scores and gain insights to determine appropriate compliance actions.
Compliance actions and threat notifications on the device mitigate data loss.
All administration is performed through the cloud administration console. No local servers or connectors to deploy and manage.
A multi-layered approach to security provides the best protection against today's mobile threats.
Questions? Contact our team.
Implement mobile threat defence for your IT estate.