Ivanti Device Control provides effective, scalable protection. Ideal for servers, fixed-function assets (e.g., POS, ATM, and pay-at-the-pump systems), and thin-client or virtualized endpoints, Device Control allows you to quickly identify and lock down endpoints to prevent unauthorised use of removable devices and ports, and to prevent unknown apps from being installed and executed—reducing your attack surface exponentially.
Ivanti Device Control
Device Control Software
Protect data from loss or theft while keeping employees productive
Protect endpoints from malware
Enhance security policies
Secure productivity tools
Enterprise file encryption and data copy restrictions
On a per-user basis, manage file types that are denied or allowed to be moved to and from removable devices and media and restrict the daily amount of data copied to removable devices and media. Add forced encryption and prohibit downloading of executables from removable devices for an added layer of malware protection.

Secure, flexible and scalable architecture
Provide organisation-wide control and enforcement using scalable client-server architecture with a central database, supporting Windows, macOS as well as Microsoft Surface devices (ARM64). Ivanti Device Control agents are protected against unauthorised removal — even by users with administrative permission.
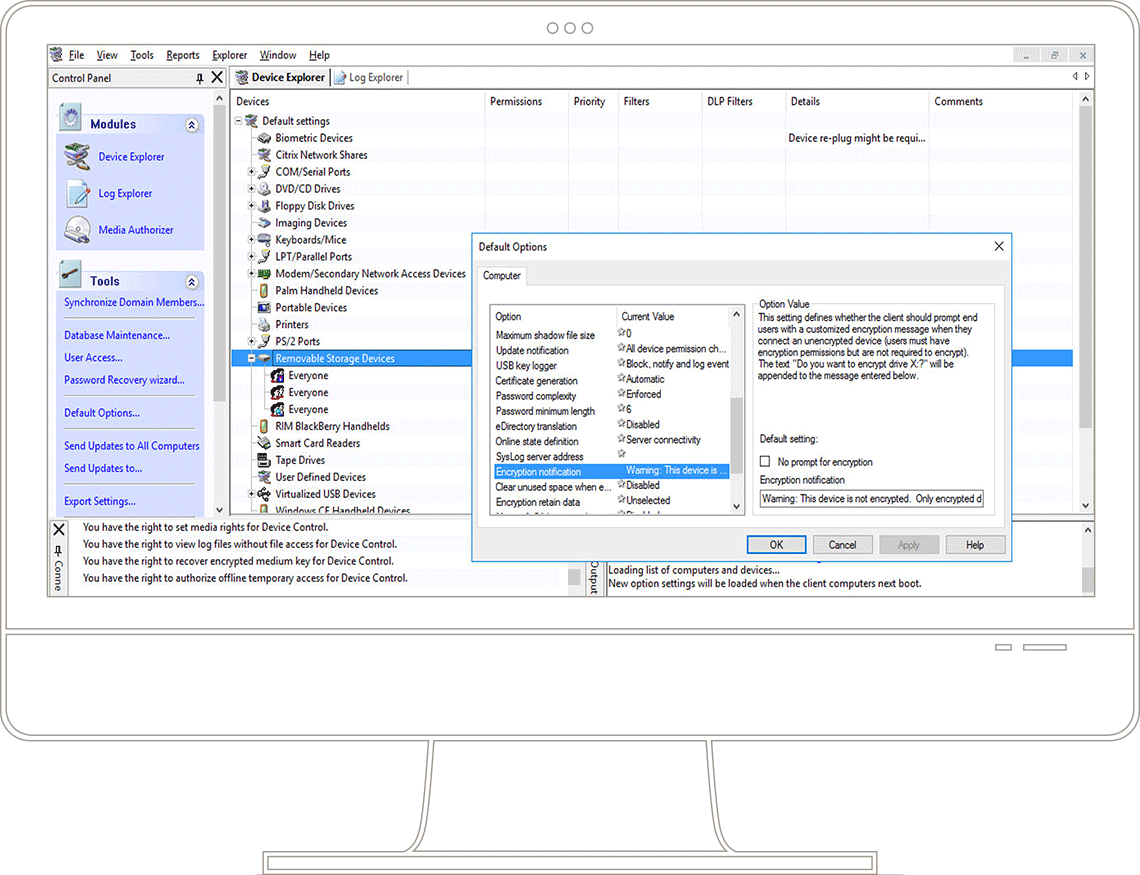
Centralised device management
Centrally define and manage user, user group, workstation, and workstation group access to authorised devices, cloud storage systems as well as Microsoft Bitlocker System Drive encryption. Devices, media and users that are not explicitly authorised are denied access by default.
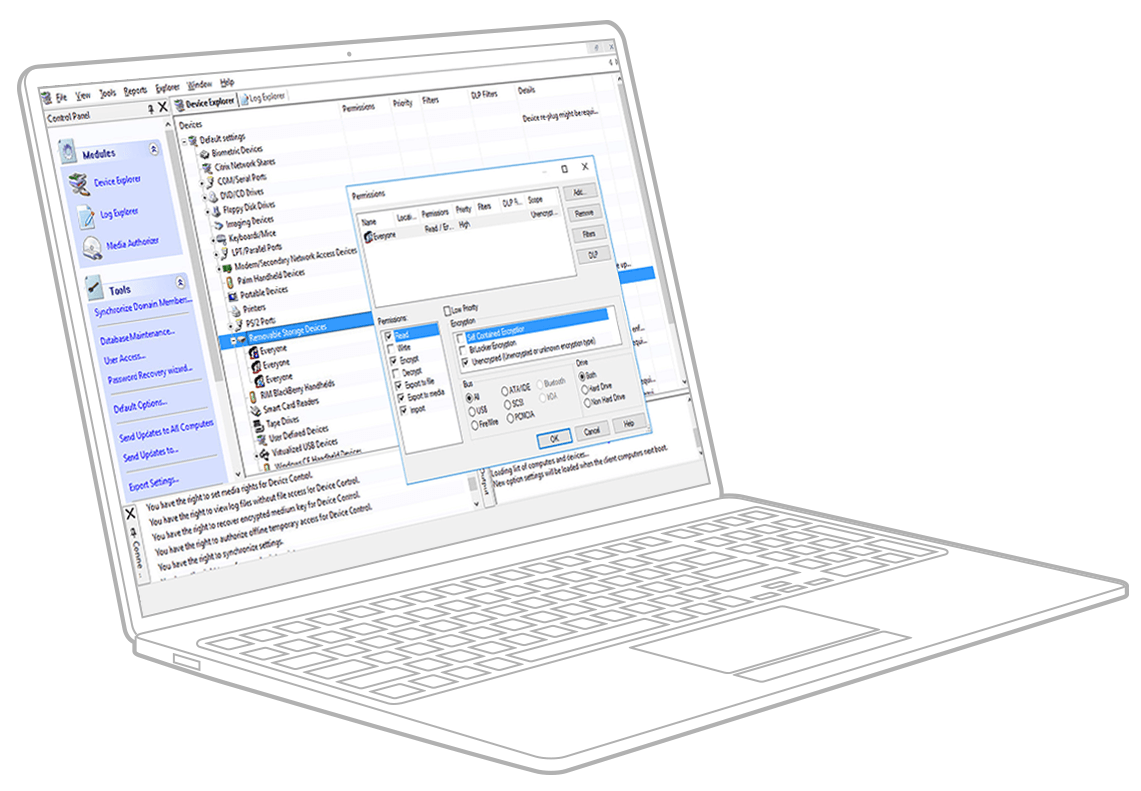
Get proactive with data access and device control without putting user productivity on hold.
Your users need easy access to data. But, that can open the door to data loss and malware. Malicious or accidental, these incidents can be a nightmare. Get ahead of threats by reducing your attack surface without disrupting your workforce and the pace of business today.
Device Allowlisting
Assign permissions for authorized removable devices and cloud storage to individual users or user groups.
Context-based permissions
Assess and apply policies to all “plug and play” devices and cloud storage by class, group, model, or specific ID.
Temporary access
Grant your users temporary or scheduled access to removable devices and cloud storage, so they can access what they need, when they need it.
Shadowing capabilities
Enable file name shadowing or full file shadowing to capture and store all copied data in a centralized place to be able to monitor what has been copied as well as restore entire files in case of theft or hardware failure.
Role-based access control
Assign permissions to users or user groups based on their Windows Active Directory or Novell eDirectory identity.
Actionable insights
Unify your IT data without scripting. More transparency across silos helps you stay proactive and responsive to security threats.
Slay device vulnerabilities without disruption
Your users need easy access to data, in and out of the network. Give them the ability to use devices when needed, without leaving the door open to attack.