August 2023 Patch Tuesday
2023 Year to Date: How Vulnerable Are We?
We are past the mid-way point of 2023. The average ransomware payment is up, but the percentage of victims paying the ransom are down. The shift toward a risk-based approach to vulnerability management is moving along, but slowly. Threat actors are fast to move on zero-day and recently resolved vulnerabilities, but just as likely to target vulnerabilities that have been exposed for years.
The shift to data exfiltration only ransoms
The Ransomware market is constantly shifting and rapidly innovating and trying new things. The latest shift in tactics to skip the encryption and focus on Data Exfiltration only has made a huge impact on the average ransoms being paid this year, but the drop in victims willing to pay is driving the overall percentage of ransoms paid to an all time low.
Coveware’s July 2023 Quarterly Report is tracking the Average Ransom Payment at $740k (+126% from Q1 2023) and attributes this spike to the massive MOVEit campaign executed by CloP impacting over 1000 companies. While the average ransom paid has spiked due to this massive DXF-Only campaign, it has also driven the overall percentage of victims willing to pay to an all time low of 34%.
The shift to risk-based vulnerability management continues
In Ivanti’s May Patch Tuesday Blog, I mentioned the CISA KEV (Known Exploited Vulnerabilities) list had reached 925 CVEs and predicted they would reach 1k CVEs by late August. CISA KEV has reached 982 prior to August Patch Tuesday and appears to be slowing down their additions to the list vs previous years. While my prediction is close, I may have been off by a month or so. We shall see as the month of August progresses.
For those who read Todd Schell’s Patch Tuesday Forecast on Help-Net Security last week or caught some of the recent news regarding the CVSS 4.0 public preview. CVSS 4.0 is the next step towards providing a better risk-based approach to assessing vulnerabilities and prioritizing remediation. The question is, will it be enough of a step forward?
A lot of news focuses on Zero-day vulnerabilities, but CISA KEV is still adding more older CVEs than new ones. Coming into August Patch Tuesday 2023 there have been 114 CVEs added to CISA KEV so far this year. 55 (48.2%) were CVEs first identified in 2023. The additional 59 CVEs (51.8%) were CVEs from 2022 or earlier dating as far back as 2004 (CVE-2004-1464). 76 of the CVEs added in 2023 were CVEs reported in 2022 or 2023 (66%), but one third of the additions were older than 2022. This is a pretty large gap in remediation of exploited vulnerabilities.
Risk-based vulnerability management vs ransomware
A risk-based vulnerability management solution can provide the visibility to shift vulnerability remediation to focus on the vulnerabilities actively being used by threat actors, especially ransomware threat actors. Comparing Ivanti Risk-Based Vulnerability Management data vs CISA KEV you can see that progress is being made, but there is still a gap.
- CISA KEV is tracking 982 CVEs currently vs Ivanti RBVM is tracking almost 39k weaponized vulnerabilities.
- Ivanti RBVM tracks vulnerabilities tied to Ransomware campaigns and is currently tracking 367 vulnerabilities. CISA KEV contains 132 (~40%) of those CVEs.
- 26 of the 367 CVEs tied to Ransomware campaigns were from 2022 or 2023. The majority (341 or ~93%) were older than 2022.
- In the past 30 days there have been 104 CVEs that are trending amongst threat actors (Ransomware, Malware and other sources of exploitation). 18 of the 104 CVEs are from 2023. CISA currently is tracking only 40 of the 104 CVEs.
This is not a product pitch (although it is a good one) but calling out that we are still falling behind in the vulnerability remediation race. CVSS 4.0 is a step in the right direction, but not nearly good enough to keep up with the challenges we face. CISA KEV is a good start but has many gaps in visibility especially for the vulnerabilities that are trending and that are tied to ransomware campaigns.
August 2023 patch tuesday
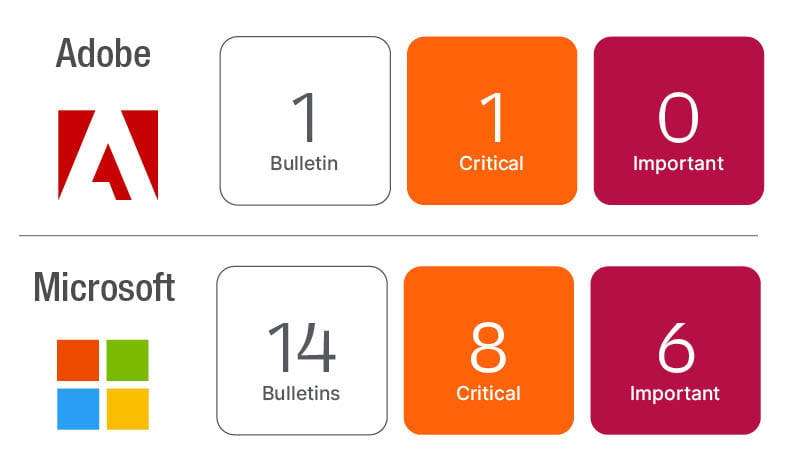
Microsoft has released updates resolving 74 new CVEs this month, one of which is confirmed exploited and six are rated by Microsoft as Critical. Microsoft also updated CVE-2023-36884 released in July to split the Office products out into a separate Defense in Depth Advisory (ADV230003). Besides the OS and Office updates, Microsoft has updates for Exchange Server, .NET, Azure, SQL Server, and Teams making for a significant lineup this August.
Additional updates from Google Chrome released on August 3rd and Microsoft Edge (Chromium) updated on August 7th and a lineup of updates from Adobe should also be included in your update activities this month.
Ivanti EPMM vulnerability remediation update
Ivanti continues to collaborate with threat researchers after the joint release of Cybersecurity Advisories on CVE-2023-35078 and CVE-2023-35081 on August 1, 2023, and urged organizations to apply the patches released by the organization. Ivanti is continuing to work actively with customers to upgrade their appliances and helping them apply the fix.
An additional advisory (CVE-2023-35082 - Remote Unauthenticated API Access Vulnerability) was released on August 2nd and updated on August 7th. An update and additional script is required to remediate the vulnerability. Guidance on how to remediate can be found on the Ivanti Community. The update to resolve the previous two CVEs with the additional RPM script will remediate all three vulnerabilities.
While not confirmed to be used in active exploits in the wild, CVE-2023-35082 has been publicly disclosed by the researchers who discovered it. Ivanti is recommending customers update to the latest version and apply the script as soon as possible to respond to confirmed exploits of CVE-2023-35078 and CVE-2023-35081 and to stay ahead of any attempt to utilize CVE-2023-35082.
Microsoft updates
Microsoft updated the affected products listed in CVE-2023-36884 removing the Office products originally listed in the CVE. The Office products listed in ADV230003 are not directly vulnerable, but can be used in an attack chain to exploited CVE-2023-36884. Microsoft has clarified the changes in the Office updates were a Defense in Depth measure. Microsoft recommends applying the Office updates discussed in the advisory in addition to the August Windows OS updates.
Microsoft has resolved a Denial of Service vulnerability in .NET and Visual Studio (CVE-2023-38180). According to the CVE details code maturity has reached proof-of-concept and it is confirmed to be exploited in the wild. The CVE is only rated as Important and the CVSS v3.1 score is 7.5, but taking a risk-based approach this should be treated as a higher priority this month.
Third Party Updates for August 2023 Patch Tuesday
- Google Chrome released Chrome 115.0.5790.171 on August 3 resolving 11 CVEs.
- Microsoft Edge (Chromium 115.0.5790.171) released on August 7 resolving 11 CVEs.
- Adobe released Acrobat and Reader (APSB23-30) resolving 30 CVEs.
- Adobe released Commerce (APSB23-42) resolving 3 CVEs.
- Adobe released Dimension (APSB23-44) resolving 3 CVEs.
- Adobe released XMP Toolkit SDK (APSB23-45) resolving 1 CVE.

