5G and the Journey to the Edge
Recently, AT&T Cybersecurity published important findings in the tenth edition of their Insights report entitled, “ 5G and the Journey to the Edge.” Ivanti was thrilled to contribute to the report, which outlines the most pressing security concerns organizations face in a world embracing the revolutionary transformation to 5G and edge technology. The report provides rich insights into the question, “How should enterprises protect emerging edge networks that will unlock compelling innovations and new user experiences?” The key findings reveal how companies are thinking about cybersecurity as we transition into a world of edge computing with 5G leading the way. The report highlights below can serve as data points for enterprises as they consider their 5G security strategies and the future of computing in their organization.
The “Edge” is the key to unlocking new user experiences
When standalone 5G becomes more ubiquitous in a few years, the highest speeds and lowest latencies will utilize a high frequency wavelength 5G technology called URLLC (Ultra-Reliable Low Latency Communications). This technology promises speeds up to 10 GBPS (20 in some tests) and, under ideal conditions, as little as 1 Millisecond of latency. Some examples of technologies that might need to take advantage of low latency and high speeds are robotic surgery, V2X (Vehicle to Anything, think drones and self-driving cars, or driverless truck fleets), and VR/AR (Virtual or Augmented Reality.)
Although it’s great to provide low-latency connections between endpoints and a 5G small cell or tower, in order for an application to truly take advantage of quicker network transit, it’s going to require many less hops between the client app and the server it’s communicating with somewhere deep in the network. These highly sensitive servers are going to need to move closer to the Edge to reduce network latency. To enable this migration of compute power from the core to the edge, Microsoft recently partnered with AT&T to create 5G Edge Compute zones, Google Cloud Platform announced Anthos for Telecom, and Amazon has introduced Wavelength to offer Elastic Compute at the edge.
The Edge Must Be Protected
So, the Edge is where the app servers will reside that are enabling critical 5G applications that require decisions to be made in thousandths of a second. But what will this infrastructure look like? It could be Unix/Linux or Microsoft servers (or even MacOS now!). The edge could and likely will be running on a virtualization layer. The applications may power critical infrastructure like smart cities or may allow a forklift to stop on a dime when someone stumbles in front of it. These servers are going to need critical attention and constant supervision. For instance, CVE’s and Zero Day vulnerabilities will need to be addressed immediately, and from a trusted supply chain, because often the stakes for autonomous vehicles alone are life and death. Patching and keeping servers current will be critical, but the report also recommends investing in network segmentation, which will allow us to restrict lateral movement of hackers when a breach occurs.
What’s attaching to the Edge?
We’ve seen an explosion in IoT devices over the past few years, from smart electric meters, to the proliferation of internet enabled devices in hospitals including wireless pacemakers, to the security system running in your home. It’s possible we may not even know what’s attaching to our wireless 5G edge networks, and it will be challenging to ascertain if they are compromised or malicious devices. It’s going to be very important for robust discovery services to run on edge networks, and the AT&T Cybersecurity Report corroborates that “Identify Assets” is one of the main calls to action.
We’ll need to map out what type of devices are connecting, but even more importantly, assign a risk posture based on enterprise risk tolerance. And then we’ll need to decide if we allow the connection, or if we need to take some other action. Networks and servers that can self-heal, enabled by security policies that allow for remediation or by harnessing autonomous bots to protect and ensure their integrity will have a head start in the Zero Trust journey.
Protect Your Network
Another key finding in the report is “Build virtualized security into the network”. Often when we talk about Zero Trust this refers to Software Defined Networks (SDN) and network segmentation, but an equally important component is the Virtual Private Network (VPN). On the edge, we may have data that is so sensitive that it can never touch a public network, but it may also need to transit public 5G infrastructure. Deploying a robust VPN that works across every OS and encrypts on a per-app basis may be an important capability. When combined with conditional access technology, that can perform a biometric user authentication, an application integrity check (is it malware?) and can verify the posture of a device before access is granted to the edge resource, the enterprise will have a powerful tool in their Zero Trust arsenal.
Zero Trust
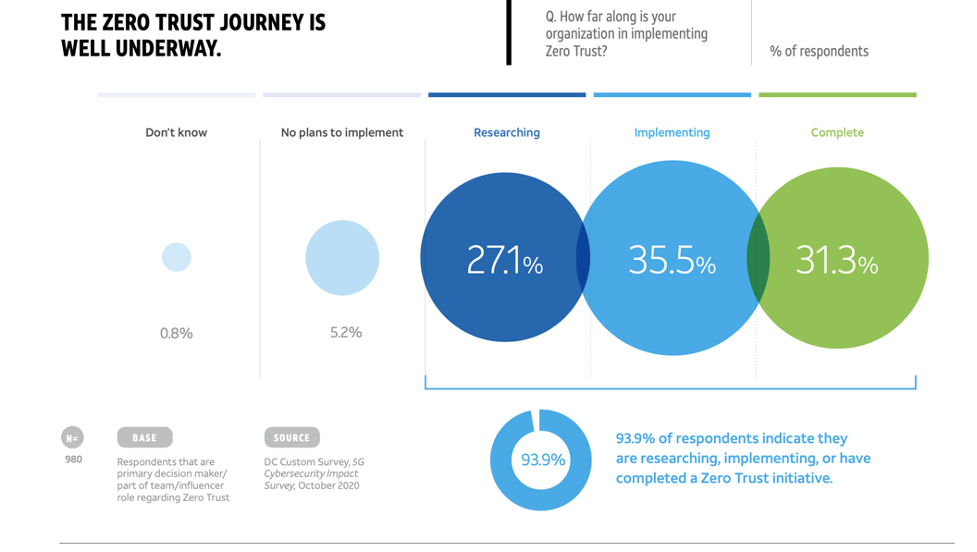
Moving to Zero Trust model, a security framework first developed by Forrester in 2009, is the key recommendation of the AT&T report. The framework, which encourages adopting a “Never Trust, Always Verify” approach to security, is increasingly becoming a focal point for companies that are evolving from traditional firewall-focused security models. One key finding in the report is that in a survey of 1,000 security professionals, IDC and AT&T found that nearly 94% were researching, implementing, or had completed Zero Trust initiatives, and nearly a third had completed implementations. Ivanti is proud to be recognized as a Wave Leader in Forrester’s 2020 Zero Trust Wave report. If you are beginning an organization's Zero Trust journey, or even well on your way, don’t hesitate to reach out to trusted partners like AT&T Cybersecurity to help you navigate the complexities of our shifting security landscape. Together, we can all enjoy a safe and secure journey to the 5G Edge.

