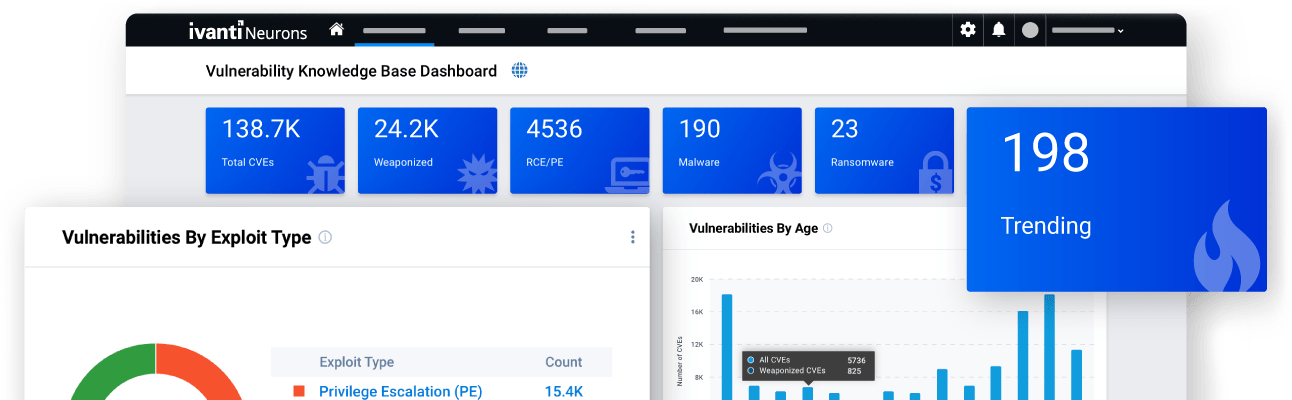
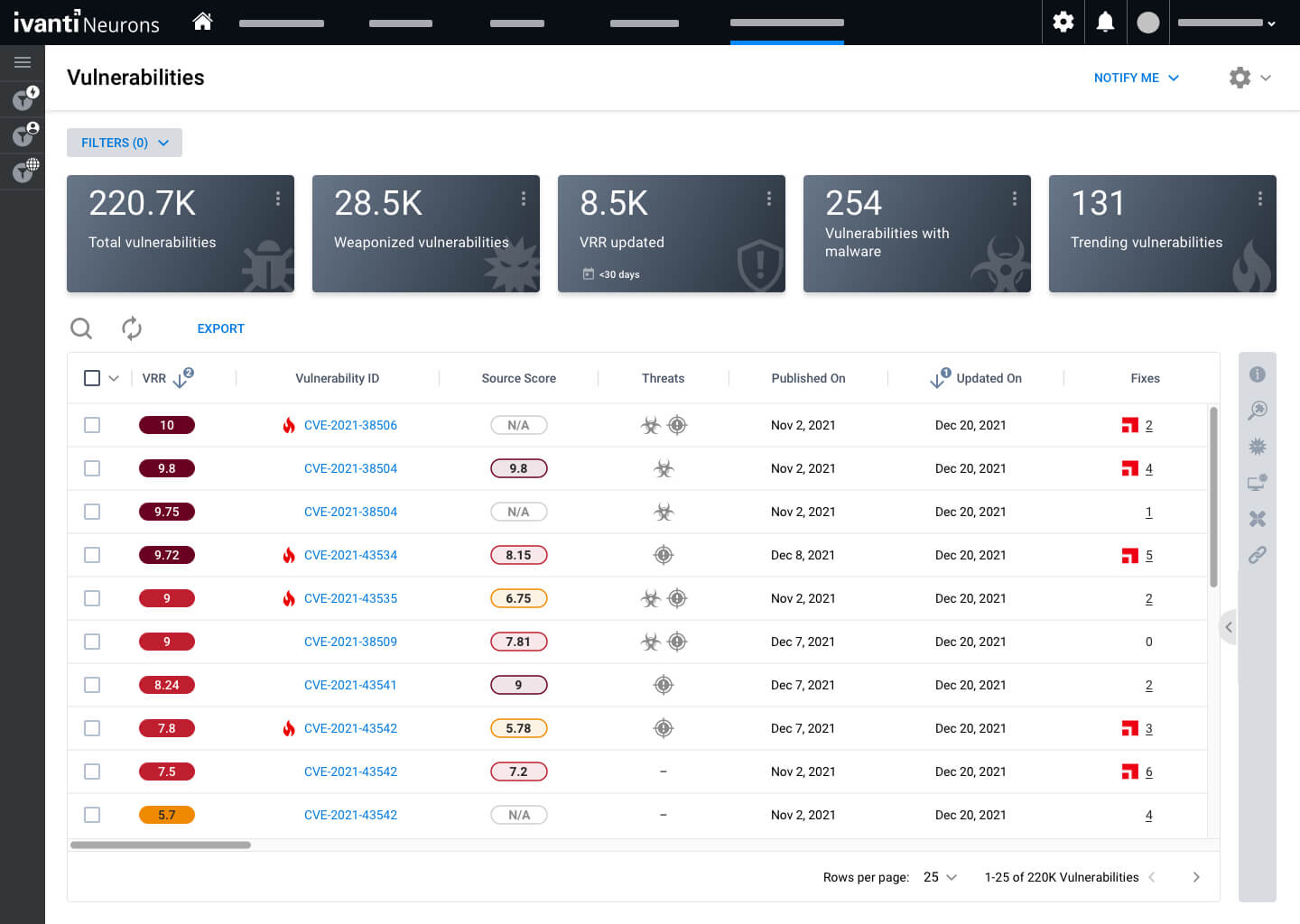
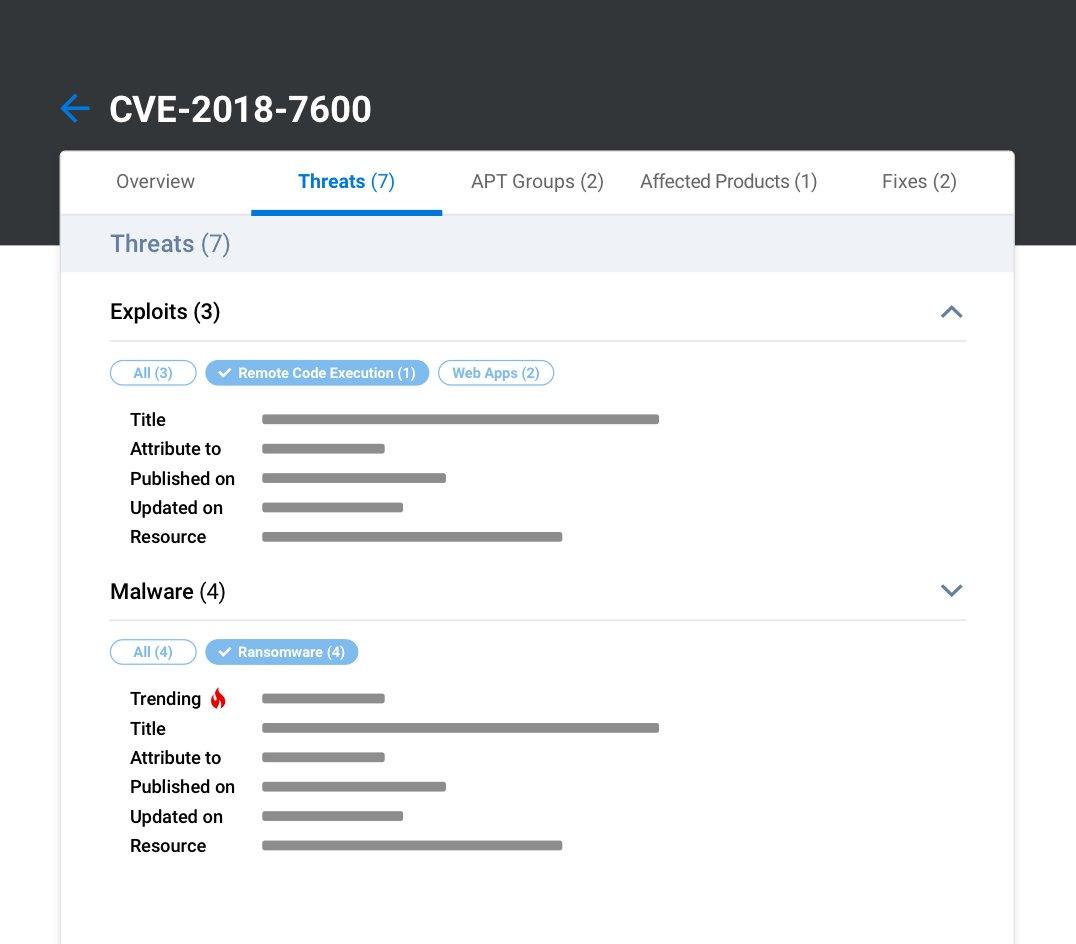
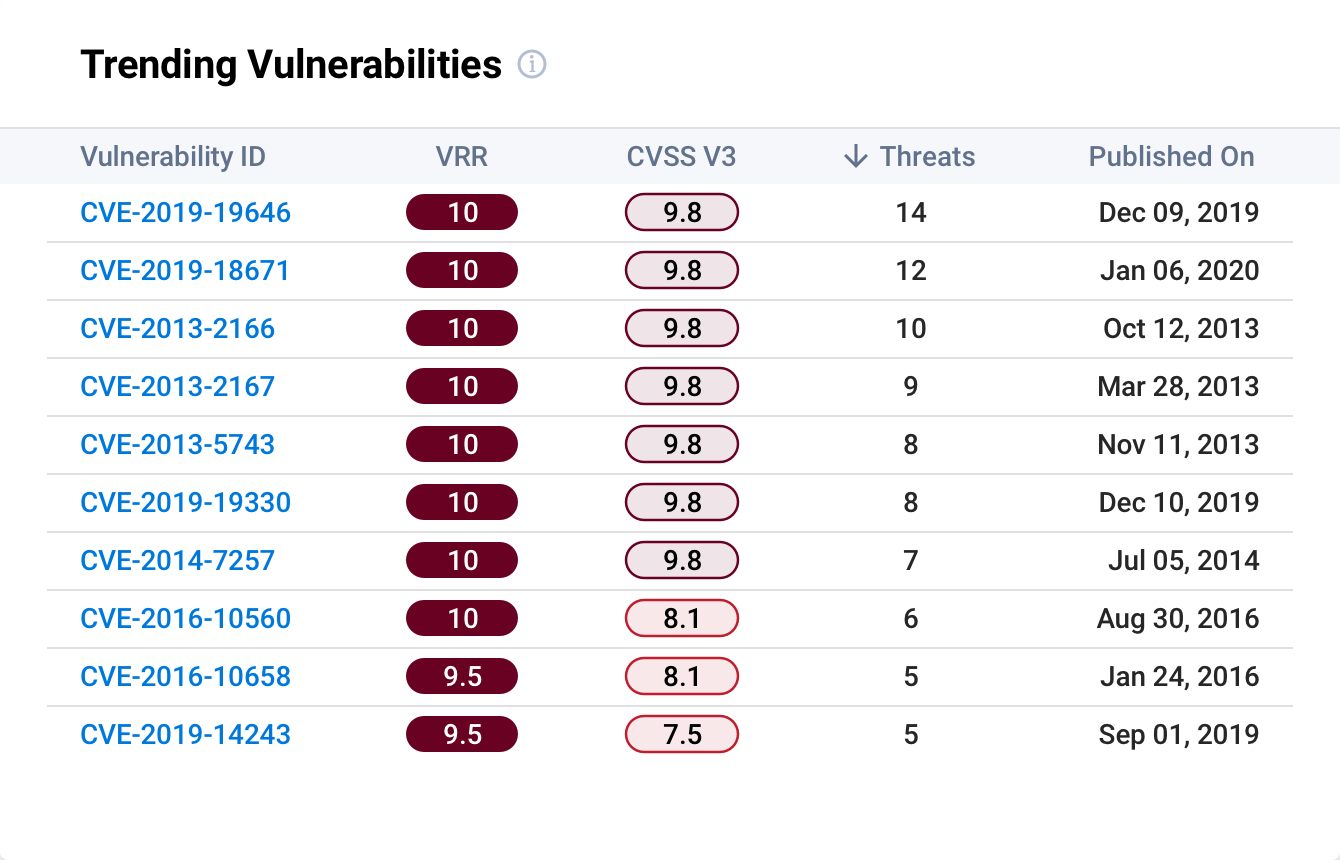
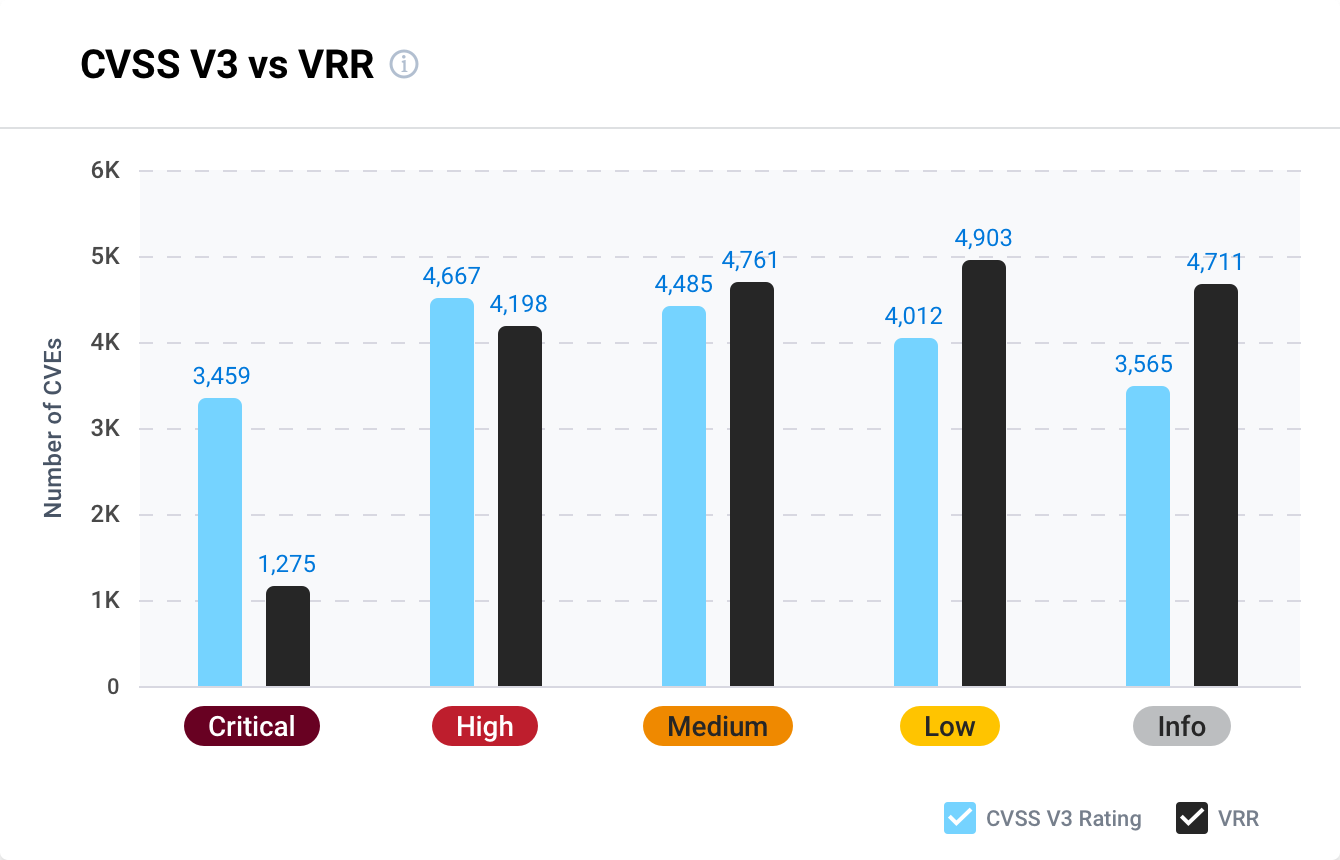
Expedite vulnerability assessments and prioritization with access to near-real-time vulnerability threat intelligence so you can quickly pivot to planning mitigation and remediation strategies.
Diverse data sources
Achieve a wide view of cyber risk with a platform that ingests vulnerability findings from over 100 independent sources plus manual findings from research and pen testing teams.