Extending the Zero-Trust Security Framework to Your Home
Mixing your personal and work devices while connected to your home network and accessing the Internet is a risky proposition from a security and privacy standpoint. Why? I frequently monitor my firewall logs. What I observe on my WAN interface are blocked IP addresses sourced from adversarial nation states which makes the hair on the back of my neck stand up. Add to that unknown threat actors from friendly countries including domestic locations performing Shodan IP reconnaissance and port scans for vulnerable internet-connected devices to exploit further adds to that paranoia. Just from a data privacy perspective, think of your home filled with a bunch of endpoints that act as telemetry sensors whose main function is to constantly collect your personal information and then store it for an indefinite period of time. These endpoints can be used by anyone in your household for work or entertainment with constant access to the insecure Internet. The likelihood of being phished for your user credentials or a family member unknowingly downloading and installing leaky or malicious apps and games onto these endpoints is very high. Throw in a couple of inherently insecure IoT endpoints that includes your smart televisions and personal assistant devices like Google Home or Amazon Echo that are used for home automation systems and require an always-on internet connection in order to work, leaves your home network and endpoints vulnerable to being easily exploited by threat actors.
I also closely monitor my intrusion detection and prevention system (IDS/IPS) alerts and see some scary network traffic on my LAN interfaces as well. These IoT devices and smart televisions inside my home generate a lot of outbound network traffic when they call home, and when my family and I are accessing social media or retail websites, are two of the most common scenarios for leaking your stored personal and work data. Threat actors commonly use phishing and pharming attacks, malicious ads and drive-by malware downloads as threat vectors to grab that sensitive data. My family and I would never know that threats existed in our home network and connected devices if I didn’t add network detection and prevention tools. Using just a home wireless router with a rudimentary firewall and network address translation (NAT) as a barrier to try to keep threat actors out will absolutely not suffice, today.
With the onset of the pandemic and the fundamental shift for employees to work exclusively from home, these scenarios have been playing out during the past year. The company you work for can enforce zero-trust security policies by fully managing and enabling controls for endpoints while physically connected to the corporate network including devices connected via remote access VPN. This is great for your work devices, but security for your personal devices that are also connected to the same home network are insecure and requires additional tools and implementing best practices to mitigate today’s sophisticated threats.
As the pandemic hit last year, we wrote a quick blog about securing your working from home environment. That was just the beginning. The goal of this blog is to extend the zero-trust security framework to your home by providing some additional tools and techniques to further protect you and your family from threat actors lurking on the Internet. What do I use for my home network and connected endpoints? Over a year back, I finally retired my trusty Cisco ASA 5505 firewall because as my internet speed became faster, the fast Ethernet (FE) switch port connections became a bandwidth and speed bottleneck for all my home network and Internet traffic. I couldn’t enable link aggregation via EtherChannel on the firewall switch ports to accommodate a faster link especially connected to the gigabit Ethernet (GE) interfaces on my wireless access points. The ASA 5505 did not support this feature.
My inexpensive solution was to buy a 4-port gigabit Ethernet (GE) LAN mini-PC and quickly installed pfSense firewall. pfSense has an intuitive admin user interface (UI) and there are several websites that walk you through working configurations to get you up and running quickly. Another option is OPNsense firewall which has a much easier to follow admin UI layout. Besides the WAN interface, I created three separate subnets because I had three physically separate LAN interfaces on the firewall.
I segmented my networks into the following configuration. Network traffic between LAN interfaces is not allowed. Only upstream traffic is permitted from each LAN segment destined for the Internet through the WAN interface. The downstream Internet return traffic is permitted from the WAN interface back to the source LAN segment. All other external ingress traffic is blocked.
- The LAN interface is directly connected to my WiFi 6 access point where my personally-owned wireless mobile and IoT devices, and laptops are connected. I enabled WPA3-Personal WiFi security on my access point and all our wirelessly-connected devices that support this newer protocol.
- The OPT1 interface provides an uplink connection to my managed switch. Connected to the switch are my work laptop and a second wireless access point to connect my work mobile device.
- The OPT2 interface provides an uplink connection to a 5-port unmanaged switch. Connected to this switch is our smart television so we can stream movies. The TV does not have a front facing camera. Also connected is the hub to our home alarm system. Premium video streaming services and alarm systems require your location data in order to work properly.
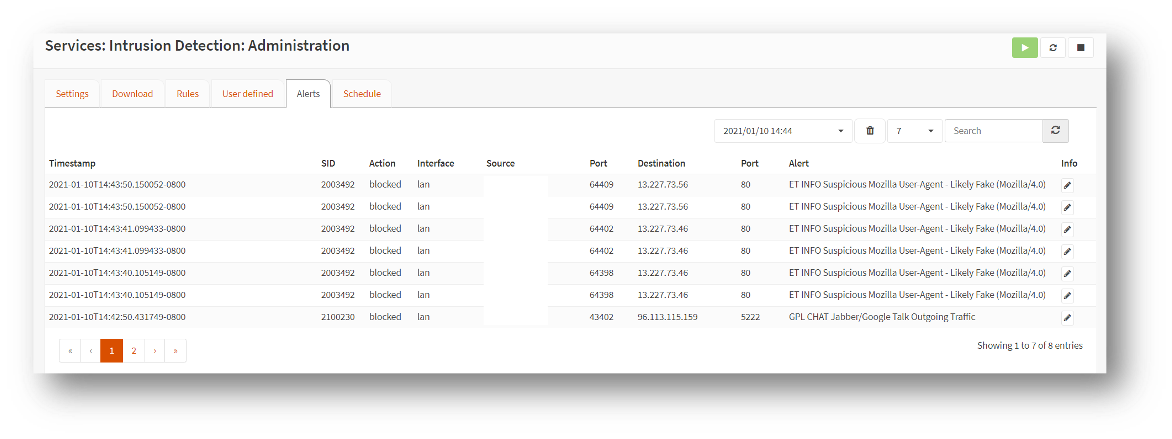
On the firewall, I initially enabled intrusion detection system (IDS) only on all three LAN segments for a week so that I could closely monitor and gain visibility into the types of network traffic and any potential threats that were traversing my home network. When I had a good idea of my internal network traffic, I enabled intrusion prevention system (IPS) mode and began blocking known and emerging threats in both the upstream and downstream traffic directions. I spent a lot of time tweaking several of these threat signatures and modifying rules that were inadvertently blocking me from accessing my normal work resources. I also did a lot of research into several blocked threats that I later found be false positives. I tweaked those IPS rules from block to alert only. Being too aggressive by enabling and blocking numerous emerging threats can wreak havoc with your connected endpoints. Spend some time researching and tweaking which threats could affect your normal work and personal routines, but take into account the amount of security and privacy risks you are willing to accept. I initially chose to enable Snort but was easily overwhelmed by the sheer number of threat signatures, which rules to enable and then whether to block or alert only. I chose to enable Suricata instead which automatically enables the vetted threat signatures and blocking rules for you without having to pay a subscription.
 There are many home firewall appliances with robust security options out there to purchase if you decide that you don’t want to ‘build your own’. These home and commercial security appliances span the price spectrum. Often you aren't just paying for the hardware, but also the added security feature subscriptions. The best advice is to do a fair amount of research on their security capabilities besides a stateful firewall and network address translation (NAT). A good solution should also include physical or virtual network segmentation capabilities, an IDS and IPS, a VPN server, and audit logging as a minimum set of security controls. You can also freely download several reputable and mature Open Source network scanning apps for your home that scans for vulnerabilities on connected endpoints as well as alert you if a potentially rogue device has just connected to your home network.
There are many home firewall appliances with robust security options out there to purchase if you decide that you don’t want to ‘build your own’. These home and commercial security appliances span the price spectrum. Often you aren't just paying for the hardware, but also the added security feature subscriptions. The best advice is to do a fair amount of research on their security capabilities besides a stateful firewall and network address translation (NAT). A good solution should also include physical or virtual network segmentation capabilities, an IDS and IPS, a VPN server, and audit logging as a minimum set of security controls. You can also freely download several reputable and mature Open Source network scanning apps for your home that scans for vulnerabilities on connected endpoints as well as alert you if a potentially rogue device has just connected to your home network.
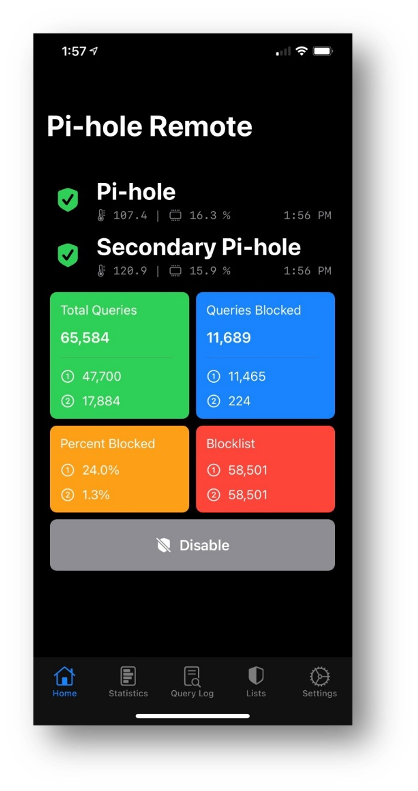
As an optional project, I had two spare Raspberry Pi computers lying around so I installed an Open Source DNS server called Pi-hole which automatically blocks malicious ads (malvertisements) and content by sinkholing blocklisted DNS requests with false results. Today, DNS is one of the most exploited Internet service so I decided to deploy DNS servers on my LAN and OPT2 network segments. Pi-hole acts as a recursive DNS server that queries top-level domain (TLD) authoritative DNS servers for domain name resolution from Google, OpenDNS, Cloudflare, Quad9 and others that employ DNS security (DNSSEC). DNSSEC is used to protect DNS exchanges over the Internet using either DNS over HTTPS (DoH) or DNS over TLS (DoT). All our personal endpoints are pointing to the internal DNS servers using DHCP to serve their IP addresses when they first boot up. The OPT1 network segment points to external DNS servers that employ DNSSEC because my work endpoints are always connected via VPN to my company’s network.
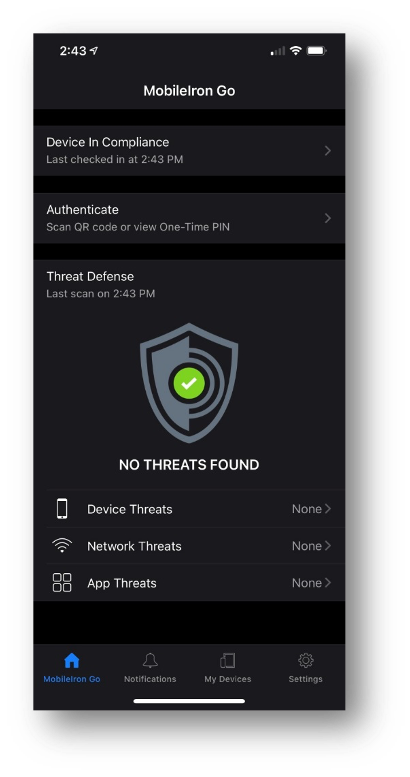 My work laptop has the Pulse Connect Secure client running always-on VPN and my work mobile device has MobileIron Tunnel configured for per-app VPN so that both endpoints can securely connect to corporate resources located on-premises at the company headquarters, in the data center, and up in the Cloud. The VPN clients were automatically installed and configured by MobileIron unified endpoint management (UEM). MobileIron UEM also provisioned and activated the anti-virus software on my work laptop and MobileIron Threat Defense (MTD) on my mobile device. MTD protects me and my work and personal data from phishing, device, network and malicious app threats. I purchased a reputable anti-virus program for my personal devices.
My work laptop has the Pulse Connect Secure client running always-on VPN and my work mobile device has MobileIron Tunnel configured for per-app VPN so that both endpoints can securely connect to corporate resources located on-premises at the company headquarters, in the data center, and up in the Cloud. The VPN clients were automatically installed and configured by MobileIron unified endpoint management (UEM). MobileIron UEM also provisioned and activated the anti-virus software on my work laptop and MobileIron Threat Defense (MTD) on my mobile device. MTD protects me and my work and personal data from phishing, device, network and malicious app threats. I purchased a reputable anti-virus program for my personal devices.
MobileIron Zero Sign-On (ZSO) was also enabled by UEM that provides multi-factor authentication (MFA) by employing strong biometrics like Apple's Face ID as an additional factor that grants me access to my work email, unified communications and collaboration tools, and to other corporate resources. On my Windows 10 laptop and desktop, I enabled Windows Hello Face to sign-in to my desktop and a YubiKey security key to access my Google and social media accounts.
In conclusion, the mindset is to place as many impediments in front of threat actors by applying a defense-in-depth strategy which is an integral part of the zero-trust security framework. At a minimum, deploying a battle-hardened firewall with IDS/IPS, audit logging, and network segmentation to deter threat actors from attacking your home network and go after less secure targets instead. Additionally, UEM can manage and deploy an always-on and/or per-app VPNs, provision identity certificates, enable MFA, enable WPA3 WiFi security, and activate threat defense and anti-virus software programmatically onto your mobile devices, laptops and desktops. All these security controls help to protect your work and personal data, and reduce your security and privacy risks while working from home in the new Everywhere Enterprise we are living in today. Stay safe and secure everyone!

