January Patch Tuesday 2018
January Patch Tuesday Update Episode II
A long time ago (last Thursday), in a development team far far away (Redmond), a band of developers acted early in a surprise attack to thwart the forces of evil by releasing a series of Operating System updates for the Windows platform. These OS updates helped mitigate the dreaded Meltdown vulnerability.
Meanwhile, their allies, Intel, who is inside practically everything, supported the OEM vendors with firmware updates to mitigate the elusive Spectre vulnerabilities which eluded mitigation at the Operating System level.
Ok, so having written up the same basic info a half dozen times at various levels of detail since last week I had to take a stab at explaining it a slightly different way. Good right? Disney should hire me. I could totally nail that Episode 9 plot. So, I did a writeup of the Meltdown and Spectre vulnerabilities yesterday from a “What to do” perspective. Take a look at that here. In an effort to not rehash that post I will sum it up as this:
Take this update seriously. It is a complex issue that, if left untended, will likely come back to bite you later this year. There are a number of moving parts to these vulnerabilities and a lot of complexity to fully resolve them. You can expect threat actors will recognize this fact and expect many environments may not be able to respond before they could possibly exploit them in the wild. There is a lot of PoC code out there for them to learn from.
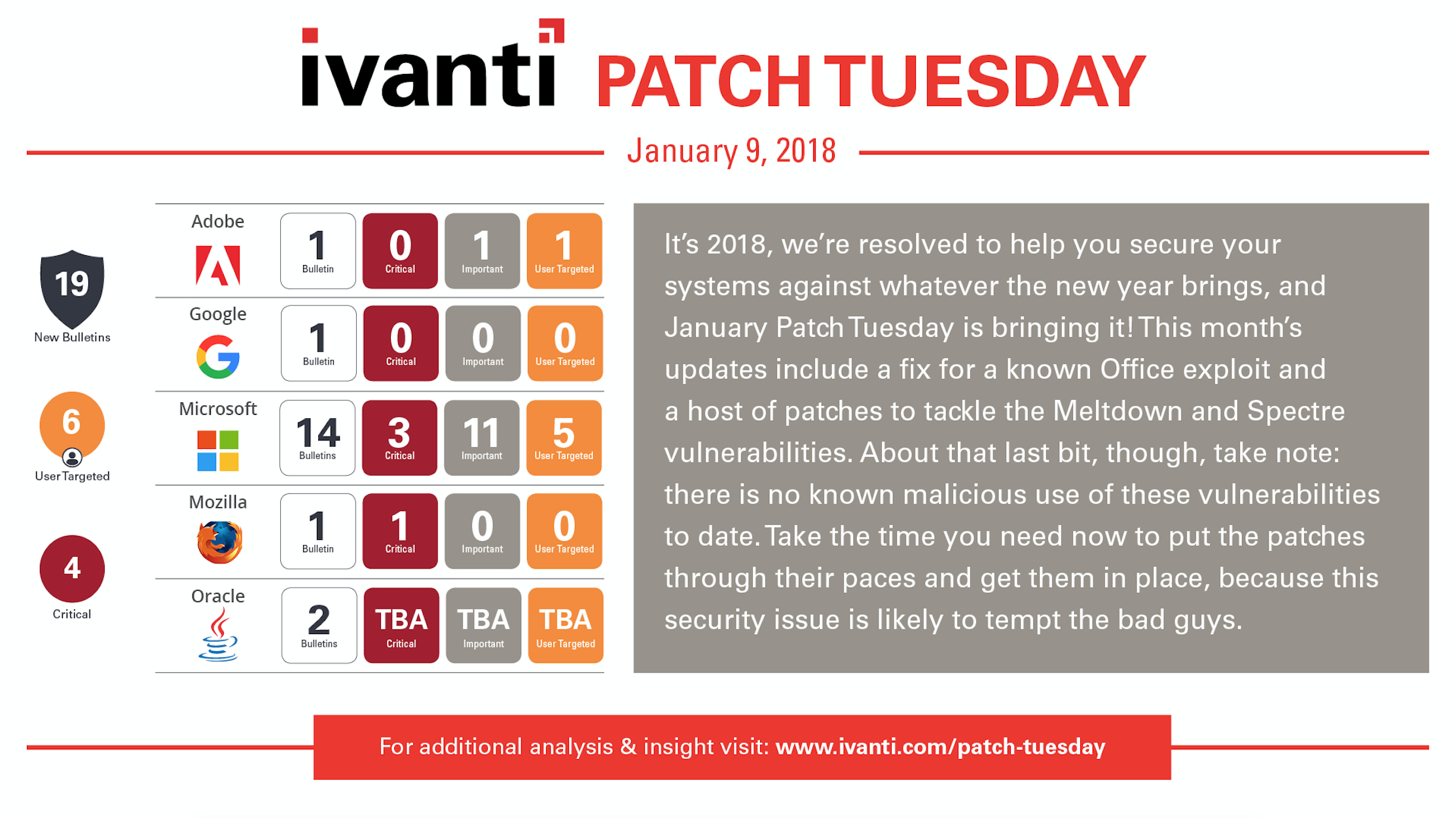
Continuing the January Patch Update today, Microsoft has released a total of 14 updates including the OS, IE, and SQL updates from last week and updates for .Net Framework, Office, and Flash Player for IE today. These updates resolve a total of around 55 unique CVEs including 4 public disclosures and 1 zero day.
Three of the public disclosures are relating to the Meltdown and Spectre vulnerabilities. These were outlined in the Microsoft Advisory ADV180002. Microsoft has resolved the Meltdown vulnerability through code changes to the kernel. The other two vulnerabilities relating to Spectre are mitigated by firmware updates. You must install the OS updates and the firmware updates to fully mitigate these attack methods.
There are a number of known issues with the OS updates this month that I outline in my other blog post regarding Meltdown and Spectre. Suffice it to say you should spend some time testing these as there are BSOD scenarios to avoid and potential for performance impacts.
The fourth public disclosure (CVE-2018-0819) affects Office for Mac and could allow an attacker to spoof antivirus or antispam.
The Zero Day pertains to a vulnerability in Office (CVE-2018-0802) that could allow the attacker to gain control of the target system. This can be mitigated by users running with less privileges. The attacker in this case, could create a specially crafted file or host specially crafted content on a compromised website or user contributed content on a website. A user opening these specially crafted files would allow the exploit to run giving the attacker equal rights to the system as the current user.
Aside from Microsoft there are a number of 3rd party updates to be concerned about this month. Adobe Flash Player resolving a single vulnerability. Mozilla Firefox 52.0.4 implements mitigation for speculative execution side-channel attacks. VMware released vCenter and ESXi updates to resolve\mitigate speculative execution side-channel attacks. And Oracle has their quarterly Critical Patch Update scheduled for next week Tuesday January 16th. You can expect many security updates for all of your favorite Oracle products including, but not limited to, Java JRE and JDK.
As always tune into Ivanti’s Patch Tuesday landing page for updated analysis as Patch Tuesday unfolds and sign up for our monthly Patch Tuesday webinar.