November Patch Tuesday 2017
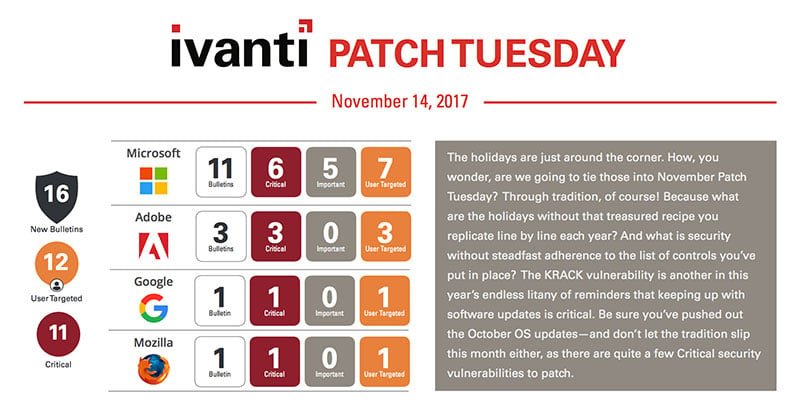
Microsoft’s Patch Tuesday update for November looks fairly tame. There are 47 total unique vulnerabilities resolved across 11 updates. Two of these have been publicly disclosed, which means enough information has been released to the public to allow a threat actor to create an exploit or at least give them a jump start on where to begin.
Be sure to check out all of Ivanti’s patch products:
Patch for SCCM
Patch for Windows
Patch for Linux, UNIX, Mac
Patch for Endpoint Manager
Following are some Indicators of Risk you can use to prioritize where to focus your attention. To start, both CVE-2017-11827 and CVE-2017-11848 affect the Microsoft Browsers. CVE-2017-11827 affects both IE and Edge. This vulnerability could be used in a phishing email or an exploiting website to convince a user to open a malicious attachment or content. Once exploited the attacker would gain equal rights to the current user. If the user is a full administrator the attacker would gain control of the affected system. The second vulnerability (CVE-2017-11848) is an information disclosure vulnerability in Internet Explorer that could allow an attacker to track the navigation of the user leaving a maliciously crafted page.
There are many Critical vulnerabilities that affect the Windows OS this month. There are four Kernel Information Disclosure vulnerabilities and one Kernel Elevation of Privilege vulnerability along with a few more Critical vulnerabilities that affect the server platforms. While not remotely exploitable, these types of vulnerabilities used together give a Threat Actor the combination required to compromise a server. In an advanced persistent threat situation, an attacker would exploit a user-targeted vulnerability to get a foothold then move laterally to other systems such as a server. Once there, they would use vulnerabilities like these to gain control of the system. So, while not your typical headline material, there is a recipe for mayhem in the vulnerabilities resolved this month. They should not go unpatched for too long.
We also have a bit of Zombie action left over from Halloween. Both Microsoft and Adobe have End-of-Support products coming back to life! Windows 10 1511 gets a revival for Enterprise and Education editions for the next six months (April 10th, 2018 is the new end date for those editions). Home and Pro users not included; you should still upgrade to a later branch ASAP. And Adobe had announced End-of-Support for Acrobat and Reader XI last month on October 15th, only to release an update this month! Adobe has nine total product updates this month and many Critical security vulnerabilities being resolved. One thing to note is many of these updates may be rated as a Priority 2, but this means it has Critical vulnerabilities, just none actively being exploited or disclosed at this time. Ivanti recommends any Adobe Priority 2s get resolved quickly, especially for Flash Player.
All of the major browsers need updating this month. IE, Edge, Mozilla Firefox, and Google Chrome all have released updates with many critical security vulnerabilities so make sure they are all on your priority list. Adobe has released nine Security Bulletins this month, most notable are the Flash Player, Acrobat and Reader, and Shockwave updates which all have Critical security vulnerabilities.
Finally, we are in the holiday shopping season now and there will be plenty of opportunists out to take advantage of the KRACK vulnerability in Wi-Fi WPA security protocol. Pretty much any Wi-Fi connection using the WPA or WPA2 encryption could be exploited. This means an attacker could eavesdrop on your connection and gain access to sensitive information including username\password, credit card info, or any other PII being transmitted over the Wi-Fi unencrypted. This vulnerability has already been resolved in last month’s Microsoft update, so be sure you have pushed out the October OS updates. Also, your phones, routers, hotspots, even Wi-Fi enabled IoT devices are likely exposed to this vulnerability, but more importantly all the public Wi-Fi connections you use should be considered vulnerable as well. If you are going to do some online shopping from your phone, you may want to do it from the cellular network. If you do connect to a Wi-Fi that could be exposed make sure you only transact on sites that are encrypted (URL starts with https:// or as soon as you connect, establish a VPN connection to secure any transactions or data traffic you may be using.
As always tune into Ivanti’s Patch Tuesday landing page for updated analysis as Patch Tuesday unfolds and sign up for our monthly Patch Tuesday webinar.