Latest Ransomware Attack Hits Legal Firms
At the start of this month, three U.S. law firms got hit with ransomware attacks. Ivanti security expert Chris Goettl gives us his take on the incident below.
First, why are legal firms a good target? To answer that we need to look at what makes an ideal payout scenario for a ransomware attack.
For a ransomware attack to be successful—and by successful, we mean the victim will have a high chance of paying the ransom—the threat actor needs a three-part strategy:
- Pain Point: Find a critical service or sensitive data about the victim or their clients. It must be disruptive at a broad scale or damaging in a significant way.
- Payout: Determine a reasonable ransomware amount to make it possible and likely that the victim will pay.
- Ransomware Campaign: Have a repeatable process for executing a series of ransomware attacks as part of a broader campaign.
Let's take a closer look at each of the above.
Pain Point
For a ransomware attack to be successful, the threat actor has to impact the victim in a way that causes significant and immediate pain. Legal firms definitely have a significant pain point. A law firm survives on its reputation and the importance of attorney-client privilege.
The threat actors in this case are hitting law firms right where it counts. Exfiltrating sensitive client data, encrypting it so the law firm does not have access to sensitive information needed to further support their clients, and on top of that, threatening to expose that sensitive data to the public.
Payout
Legal firms definitely have the money to pay out if the pain threshold can be met. Unless, of course, the cybercriminal gets caught, in which case the full might of that legal firm could be brought against them.
Ransomware Campaign
Threat actors don’t want to spend a significant amount of time and effort on every attack. They are looking for repeatable processes and methods to perform their attacks at scale. Remember, for threat actors, this is their business. As is the case with most businesses, you have to figure out your target market, generate leads (or in this case, potential targets), and have enough of those leads to get a conversion rate that makes your campaign successful. Conversion in this case is when a victim pays out.
Let's say a threat actor chooses to target legal firms and they find 1000 targets. For the sake of argument, let's say they successfully penetrate into 10%, or 100 of those legal firms. Of those, let's say they successfully launch the ransomware attack and exfiltrate sensitive data from 10% of those, so 10 companies got an actual ransom. And of those 10 companies, only half pay the ransom. If the ransom is $50K and only five paid the ransom, they only made $250K.
Threat actors are going to look for large volumes of targets or significant enough pain to get a higher payout per attack to grow their “business”.
 How to Defend Against Ransomware
How to Defend Against Ransomware
So what should companies be doing to defend against this type of attack?
No matter which industry is being targeted, the tactics used by threat actors are often very similar. They just get customized to fit the needs, and the easiest way to start the attack is social engineering. As we have seen with the recent ransomware attacks on legal firms, email was a common initial entry point. Here are the ways to prevent an attack:
- User Education
- Email Protection
- Patch Management
- Vulnerability Management
- Application Control
- Privilege Management
- Endpoint Detection and Response
User Education
Pretty much every industry is susceptible to social engineering. With each the tactics just change. In a few minutes, you can Google phishing tactics by vertical and you will find some great statistics about which industries are more likely to click, and specifically what tactics are more likely to work.
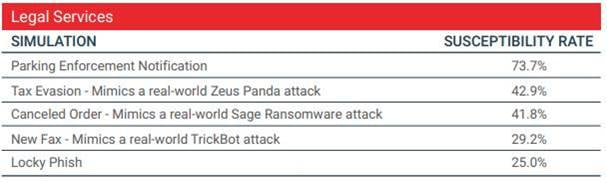
For instance, PhishMe has a report from 2017 that breaks down the five best simulations to run for legal firms to educate users. The are the most likely ways that an attacker is going to create a phishing scam to target a legal firm.
Email Protection
This is an easy entry point for threat actors. Rather than try to find their way in, they can entice a user to let them into the environment. Email protection can significantly mitigate the threat of phishing attempts and malware that come through links and attachments in email.
Patch Management
A vulnerability is a vulnerability. As long as it is exposed an attacker can exploit it and do nefarious things. The most effective way to eliminate vulnerabilities is to remove them. The majority of vulnerabilities are in software. You need to patch your operating systems and applications in your environment quickly and efficiently.
Vulnerability Management
Continuous Vulnerability Management is a process that many companies struggle to keep up with. This is the Security team performing vulnerability assessments using a Vulnerability Management solution and the Operations team patching and updating configurations in the environment to resolve the vulnerabilities that are identified. The majority of vulnerabilities are in software and having a good relationship between the Security and Operations teams and a good Vulnerability Management and Patch Management solution in place will help to keep up with the constant stream of vulnerabilities to mitigate or fix in your environment.
Application Control
Malware, ransomware, RATs, one thing these all have in common is the fact that these are untrusted payloads or applications that a threat actor needs to run in your environment to be successful. There are fileless attack methods as well, but at the end of the day most fileless attacks still need to execute something that can be stopped by an effective AC policy. Traditional whitelisting approaches can be difficult to rollout and maintain. Use of more modern trust models can simplify this and provide a significant amount of protection with a minimal amount of maintenance and setup.
Privilege Management
The keys to the kingdom (or city). We are in an age where we have empowered our users. Many companies suffer from the issue of “Admin Everywhere” or privilege sprawl. In order to reduce support costs and enable users we have given them more control over their systems by making many of them local admins. This also means that an attacker in many cases will have that same power if they compromise that system giving them the power they need to move about your network quickly and efficiently. By reducing privileges a threat actor will have a harder time getting into your environment as they will need to find ways to further compromise systems to get the level of control they need to take the next step in their attack.
Endpoint Detection and Response (EDR)
This is the ability to spot more sophisticated and complex behaviors than AV can spot. Most malware is used in targeted attacks. Threat actors will morph their malware just hours before an attack is launched reducing the effectiveness of AV to block that threat significantly. An EDR solution in the hands of the right team can spot a threat and allow you to respond quickly and effectively to isolate the threat and identify what the threat actor was doing. Then actions can be taken to mitigate or eliminate the means by which they performed their attack (like a specific software vulnerability or configuration in the environment).

