Security — Better Together
 You don’t need to look very far back to see the painful impact that vulnerabilities have had on companies’ reputations, executives’ reputations, and even on everyday users and families. It seems like every other month someone happens to find themselves in the headlines reporting a data breach of sorts. This is why when we talk about security, we focus on the Center for Internet Security Controls. The Center of Internet Security (CIS) was developed in order to bring awareness and promote best practice around cyber security.
You don’t need to look very far back to see the painful impact that vulnerabilities have had on companies’ reputations, executives’ reputations, and even on everyday users and families. It seems like every other month someone happens to find themselves in the headlines reporting a data breach of sorts. This is why when we talk about security, we focus on the Center for Internet Security Controls. The Center of Internet Security (CIS) was developed in order to bring awareness and promote best practice around cyber security.
What is Defense in Depth?
When I think about security, I think about defense in depth. There is a saying in sports: “The best defense is a good offense.”
In baseball for example, you can have a rotation of the best pitchers in the world, but if the batters don’t get on base and provide any run support you won’t win any games. So you might wonder how this applies to security and defense in depth. Well, just like in baseball, you can do one thing perfectly. But because you don’t do anything else well—or at all—it can cost you dearly.
Defense in depth is when everything comes together as a team—we get great pitching, some good hitting and runners on base, and even some good defense out in the field. Now that’s a recipe for success; multiple players coming together as a team in order to secure a win!
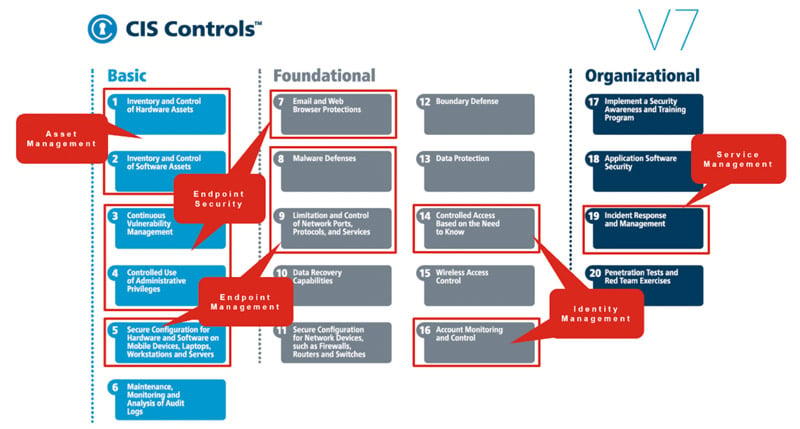
How does this all apply to security? Well, if you’re familiar with the CIS Controls, you know there are 20 controls that are recommended in order to secure your enterprise. These controls fall into three categories: basic, foundational, and organizational. When these controls are implemented together, they work as a team to secure your enterprise. Defense in depth is just that—multiple solutions or controls working together securing the enterprise.
Why Defense in Depth?
We covered what defense in depth is and what that means. Now let’s talk about the why.
Just like our baseball reference from earlier, everyone working together provides a much better opportunity to win than only performing one aspect of the game well. The same holds true when talking about security. For example, let’s say you do a great job at patching the OS, but you don’t patch third-party applications. That means you’re still leaving an attack surface. This is why defense in depth is important. When you have multiple tools or controls working together, you can better mitigate risk and secure the environment.
When we look at Ivanti’s Security strategy it aligns perfectly with the CIS controls. Ivanti’s Security portfolio targets the top five controls, but Ivanti’s broader portfolio covers a number of additional controls with our Unified Endpoint Management, Asset Management, Service Management, and Identity Management solution stacks. Organizations gain a one-stop shop to help secure their enterprise.
The top five CIS controls include inventory and control of all hardware and software assets, continuous vulnerability management, controlled use of admin privileges, and secure configuration. Implementing these five controls successfully has been proven effective against more than 85% of common cyber-attacks.
Let’s put that into perspective. By implementing only 20% of the CIS controls you can mitigate your cyber-attack risk by over 85%. Doesn’t that seem like a good starting point?

It All Starts with Asset Management
When you begin analyzing your security needs, it all kicks off with Asset Management. Your environment can’t be secured if you don’t understand all the hardware and software assets you have in your environment, so making sure you have a good handle on those assets is the first step in securing your environment.
Next, we talk about continuous vulnerability management—logging, tracking, and finding those vulnerabilities so you can remediate them adequately—typically via patch management. This doesn’t mean just patching Microsoft but also patching third-party applications and software in your organization as well. Eighty-six percent of vulnerabilities come from third-party applications, which means patching them is just as important as patching the OS, and maybe even more so.
Defense in depth is when we bring multiple controls together as a team to secure the environment. Better together is bringing multiple controls into a single management solution to help you manage and secure the environment easily.
If you look at the next two items on the CIS controls list, we start considering controlled use of admin privileges and secure configuration of hardware and software assets. This is where Privilege Management, Application Control, and Device Control come into play. The best way to approach security is one step at a time, otherwise we risk leaving a gap.
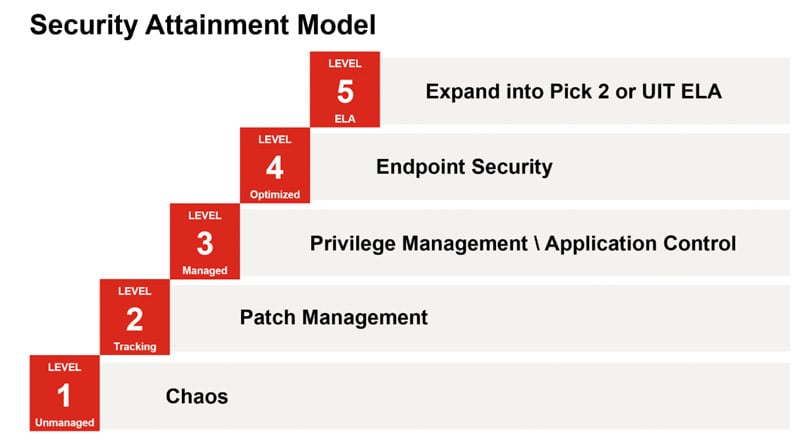
Let’s follow these steppingstones to secure the environment, and let’s begin with the basics patching. Once we have that down, we can continue to grow and enhance our security posture to include Privilege Management, Application Control, Device Control, and beyond. The advantage of “better together” is having one product or one vendor that helps bring this in sync in an easy-to-use, integrated fashion.
