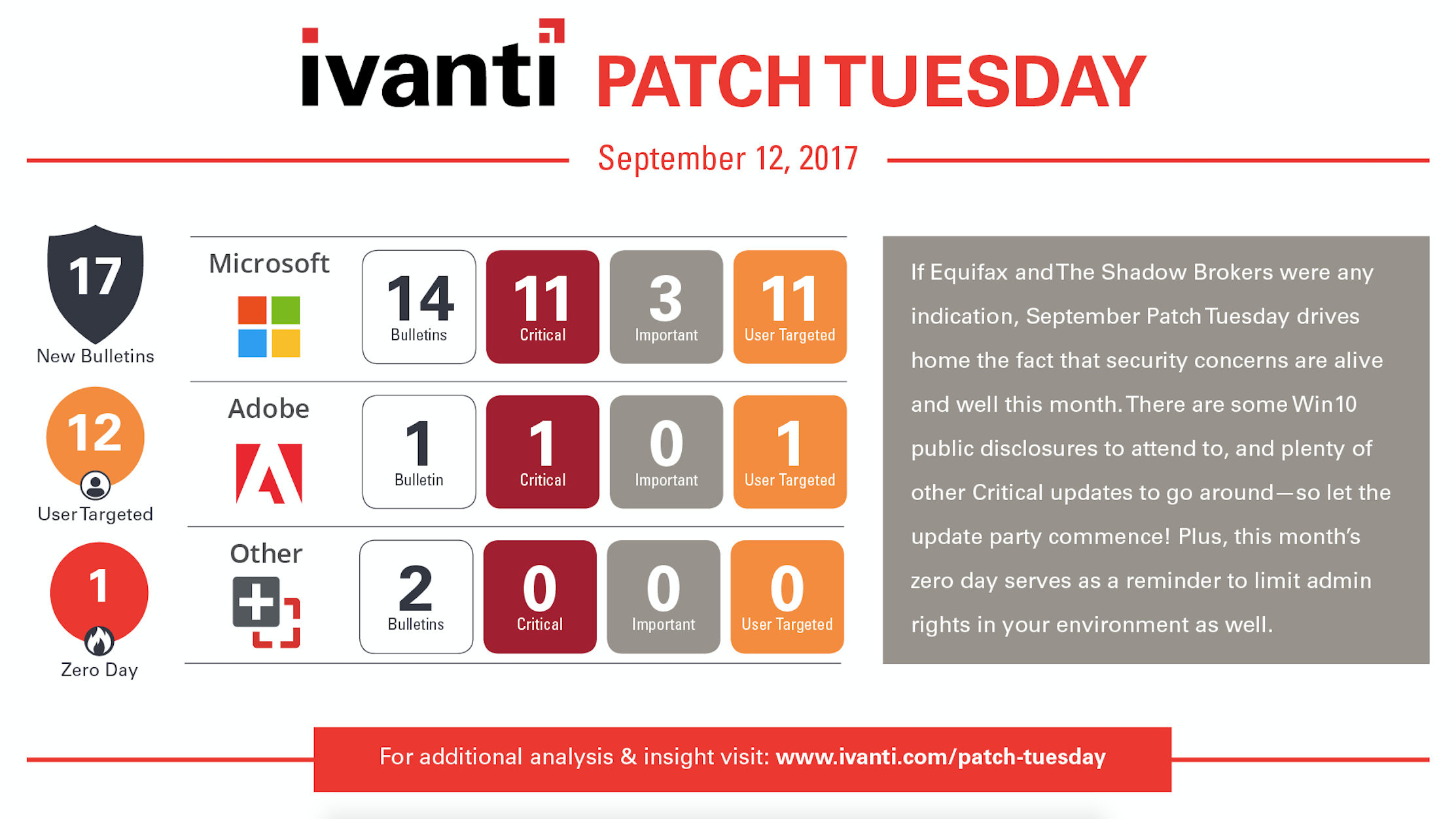
September Patch Tuesday 2017
September Patch Tuesday is in and it brings a high CVE count along with some public disclosures and a Zero Day to be concerned about. We also have a Flash Player update with a pair of CVEs needing some attention. In non-Patch Tuesday related news, there was the recent Equifax breach bringing the large-scale data breach to the top of the headlines with a bit of controversy and some storm clouds on the horizon with the latest teaser from The Shadow Brokers foreshadowing potential things to come. Also, read on for a bit of comic relief at the end in a series of security related news items that have come up recently.
Be sure to check out all of Ivanti’s patch products:
Patch for SCCM
Patch for Windows
Patch for Linux, UNIX, Mac
Patch for Endpoint Manager
Starting with Microsoft - September Patch Tuesday resolves 76 unique vulnerabilities across 14 total updates. As many as 11 of the 14 updates are rated as Critical and 3 are rated as Important. There is one Zero Day this month and three Public Disclosures to discuss.
Affected Microsoft Products:
- Internet Explorer
- Microsoft Edge
- Microsoft Windows
- Microsoft Office and Microsoft Office Services and Web Apps
- Adobe Flash Player
- Skype for Business and Lync
- .NET Framework
- Microsoft Exchange Server
.Net framework has returned after a three-month hiatus. The last update we have seen for .Net Framework was back in May Patch Tuesday. This month’s update is rated as Important and only resolves one CVE, but that CVE is flagged as a Zero Day, meaning it was known to be exploited in the wild prior to this update being released. CVE-2017-8759 is a vulnerability in Microsoft .Net Framework’s processing of untrusted input. This is a user targeted vulnerability, meaning an attacker could convince a user to open a malicious document or application resulting in their ability to take control of the affected system. If the user is configured as less than a Full Administrator, the attack would be mitigated somewhat by only allowing the attacker to perform actions in the context of that user’s permissions, so least privilege helps here. Open question as to why it is only rated as Important if it is a user targeted vulnerability and already known to be exploited.
The three public disclosures this month are all on the Windows 10 platform. Two in the OS and one in the Edge browser. While all three of these have lower exploitability index ratings, the fact that they have been Publicly Disclosed means a Threat Actor has enough information to potentially create an exploit. Public Disclosures are a threat indicator to watch for as they are at higher risk of being exploited since some of the busy work of research and finding how to exploit may have been done for them already.
- Device Guard Security Feature Bypass Vulnerability (CVE-2017-8746) – An attacker can inject malicious code into a Windows PowerShell session bypassing the Device Guard Code Integrity policy. The attacker would need to have access to the local machine and then inject malicious code into a script that is trusted by the Code Integrity policy.
- Broadcom BCM43xx Remote Code Execution Vulnerability (CVE-2017-9417) – A vulnerability exists in the Broadcom chipset in HoloLens where an attacker could send a specially crafted WiFi packet to exploit how HoloLens is handling objects in memory. If exploited, the attacker could then install programs; view, change, or delete data; even create new accounts with full admin rights.
- Microsoft Edge Security Feature Bypass Vulnerability (CVE-2017-8723) – A vulnerability exists in Microsoft Edge where the Content Security Policy (CSP) fails to properly validate certain specially crafted documents. An attacker could trick a user into loading a page containing malicious content or into visiting a website hosting the malicious content. The attacker could also inject the malicious page into a compromised website or an advertisement network.
On the Adobe front this month, the Flash Player update includes fixes for two vulnerabilities (CVE-2017-11281, CVE-2017-11282). Both are rated as Critical. The priorities assigned to each distribution do vary. For Flash Desktop and Flash for Edge and IE the update is rated as Critical (Priority 1 by Adobe terminology). Flash for Chrome is rated as Important (Priority 2). Both vulnerabilities are Remote Code Execution vulnerabilities involving memory corruption to exploit.
Let’s turn to some recent headlines:
There has been a lot of news around Equifax and the controversy around the disclosure. There has also been a bit of news from The Shadow Brokers on new drops coming with a new set of tools. Equifax is a shining example of the Data Breach being alive and well. The latest from the Shadow Brokers is a tool set that enables a Threat Actor with a perfect tool set to carry out an Advanced Persistent Treat. If we merge the two topics we get Shadowfax. I had a weird Friday afternoon and as I was reading the two of those back to back and there is where my mind went.
Continuing with a more lighthearted lineup of topics:
- This is a couple months old now, but a friend tweeted me on it today and it made me laugh. A hacker used a fish tank to hack into a casino, which could change the way IoT technology is handled by businesses. Just think of all the #phish related pun possibilities!
@ChrisGoettl #fearthetoaster is so 2016, it is time to #fearthefishtankhttps://t.co/vYsyHkzswb
— Mike Robinet (@mrobinet) September 12, 2017
- At Def Con hackers demonstrated a successful “Rick-Roll” of a WinVote voting machine.
For deeper analysis on the September Patch Tuesday release join us live for the September Ivanti Patch Tuesday Webinar!