The Right Not to Reply – 5 Steps to Prevent a 'Reply All' Storm
Security threats and breaches are regularly becoming front page news, and malware in its many guises is (quite rightly) front-of-stage as the villain of the hour.
But recently there was a reprise from a seemingly innocent source that can be just as damaging and just as costly within your environment: the dreaded Reply All email storm.
Reply All
Its most recent appearance was within the NHS mail system back in November 2016, but organizations such as Cisco and Reuters have also reported similar Reply All outages in recent years.
What’s unique about this problem is that it is not the work of a crime syndicate demanding a ransom or a bedroom hacker at odds with world. Rather, it is instigated via a simple user or system error that unwittingly sends out messaging to a vast number of recipients. That in itself can cause a strain on large enterprises, but if it stopped there, things would not be so bad.
The real problems start to occur when those emails are not only received, but how they are dealt with by the recipient. For instance, maybe you had a bad commute into work one day and a random email sent to all employees tipped you over the edge and prompted a curt response:
“Can you remove me from this distribution list?? I am not interested in this subject!”
Quite harsh and to the point, perhaps? Sure, but you just sent this via the Reply All option, which duplicated that original mail, and now everyone who had that original mail (who may have had an even worse start to the day than yourself) now has another one from yours truly. Human instinct takes over, and instead of ignoring the response, a barrage of like-minded users start to join the party, all unwittingly using Reply All:
“You're just making it worse, stop replying to everyone."
“Can we please all stop Replying to All!”
“Stop Replying to All, says the person replying to all!”
This phenomenon even has its own Twitter hashtag: #ReplyAllGate.
I doubt there are many organizations who have yet to have come across this issue, but there is a simple way in which Ivanti's Environment Manager can help.
How Ivanti can help
The Ivanti approach to policy and control has always been to empower administrators with the functionality to configure secure but productive workspaces for their users.
In this scenario, the silver bullet is our policy lockdown action which now includes full support for Office 2016 (as well as previous Office versions) with the release of Environment Manager 10.1. We can apply this control to not only the locally installed Outlook application, but if your users access Outlook via Office 365 in an IE Browser, this can also be locked down.
Five steps to configure:
1. Open up the lockdown wizard, and select the Spy Tool option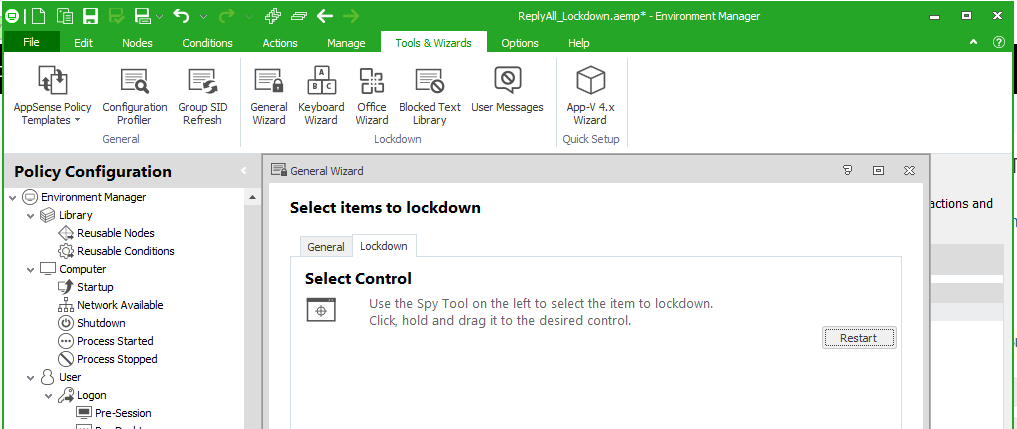
2. Identify the Reply All option within Outlook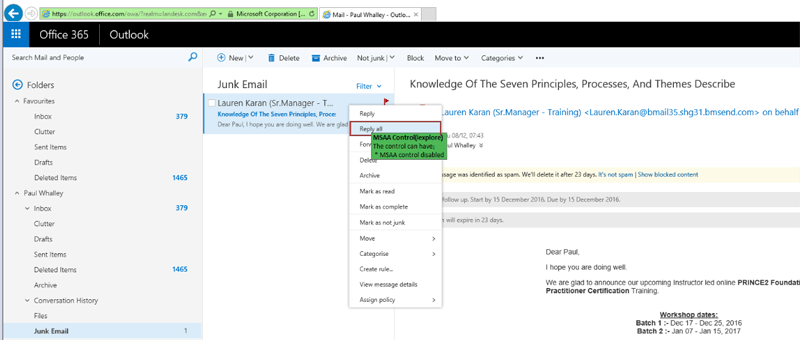
3. Once targeted, the Policy Action will be created for you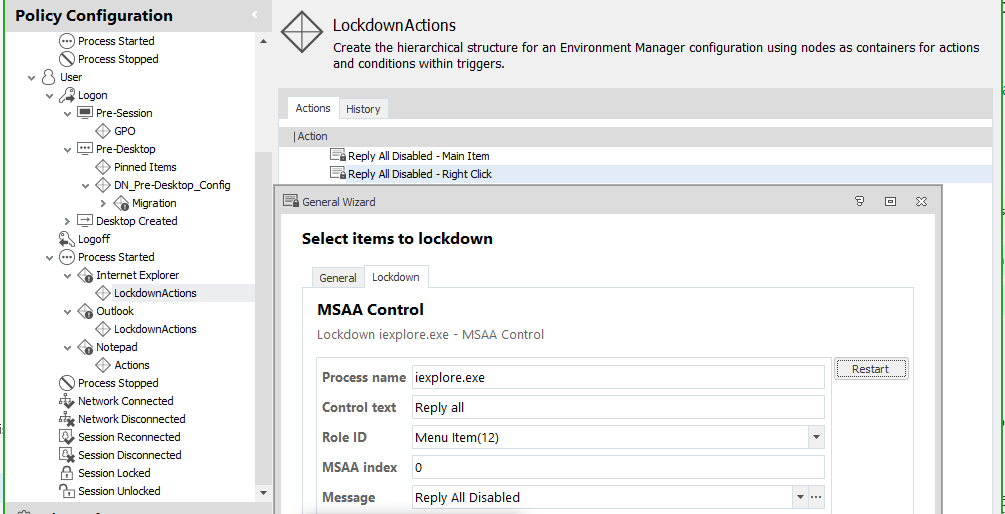
4. Now create a custom message, this will be displayed when a user next attempts Reply All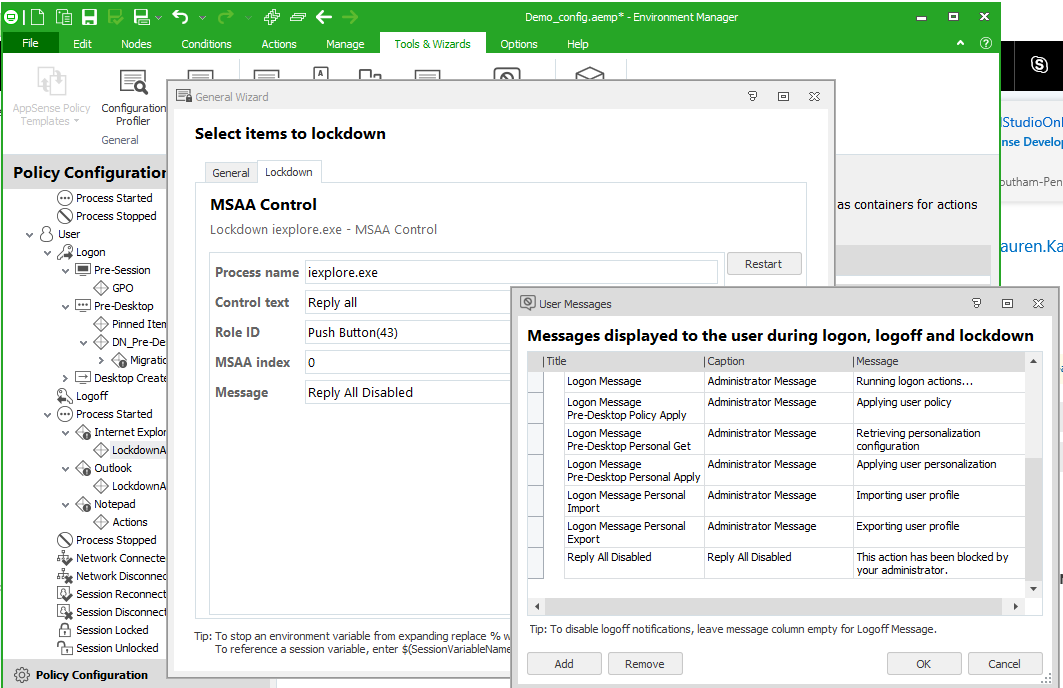
5. When a user attempts to Reply All, they will now be prevented and receive the configured message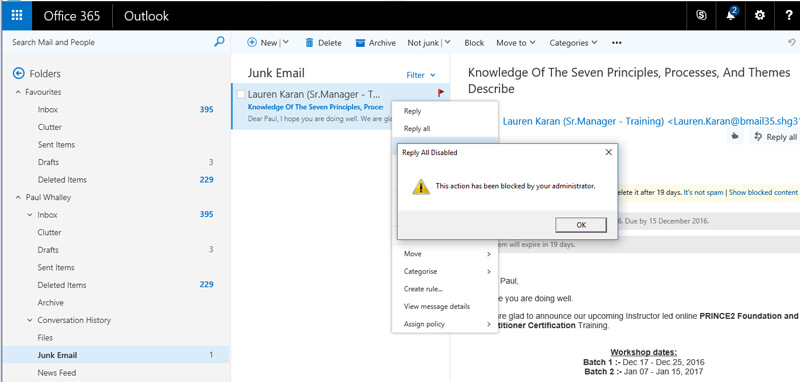
It is worth noting that the Reply All option is available in a couple of other places within the Outlook UI, but by repeating the technique above, you can similarly prevent access from those areas too. By using our contextual condition engine, you could provide granular control over who and when this lockdown action comes into play, perhaps for a particular active directory group or subnet of endpoints.
However you decide to implement, by following this approach, Environment Manager can prevent you from becoming the next organization in the #ReplyAllGate saga.

