What is a human attack surface?
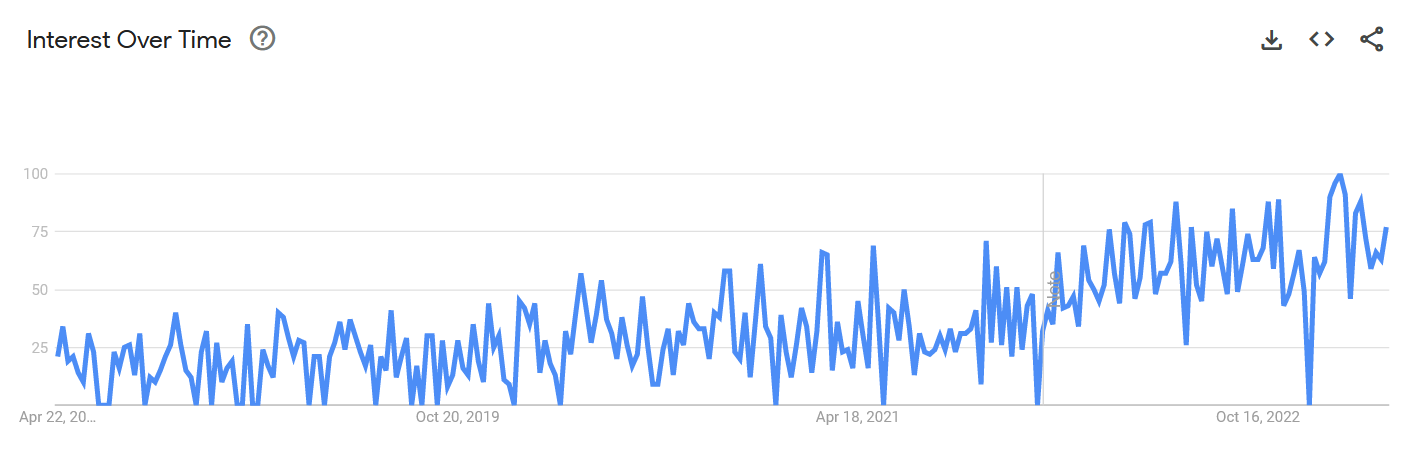
Much attention is given to the attack surfaces of networks and endpoints, but there’s another attack surface that's often overlooked: the human attack surface. That may explain why 74% of the breaches analyzed for the 2023 Data Breaches Investigation Report (DBIR) from Verizon involved a human element.
Human attack surfaces are formed through the failure of users or administrators to adhere to security best practices. These failures mainly consist of people falling for social engineering attacks. According to the Verizon report, phishing and pretexting – which is often used in conjunction with phishing – are the two types of social engineering that claim the most victims. No wonder 43% of organizations surveyed for the Press Reset: A 2023 Cybersecurity Status Report have experienced a phishing attack in the past two years.
Other components that make up a human attack surface may include:
- Failure to patch systems regularly.
- Use of weak and repeated passwords.
- Improper assignment of user privileges.
- Propping the door to an office building open.
- Letting unauthorized persons tailgate or piggyback into a secure space.
- Failure to eliminate network design flaws.
- Allowing sensitive information to be stolen via shoulder surfing.
- Falling for a baiting attack by plugging an unknown USB drive into a computer.
- Improperly discarding of sensitive data.
The list is endless. And while the examples shared thus far are typically unintentional acts that can be attributed to naiveté and negligence, human attack surfaces also include the intentional actions of malicious insiders. According to the Cybersecurity & Infrastructure Security Agency (CISA), an intentional threat is “the potential for an insider to use their authorized access or understanding of an organization to harm that organization.”
Note that different attack vectors can be considered part of multiple types of attack surfaces. For instance, the propped door example could be considered part of both a human attack surface since it was propped open by a human and a physical attack surface as the door is a physical object offering entry to a physical location. What’s ultimately important isn't the type of attack surface an attack vector is attributed to, but that you identify, manage and — where possible — eliminate the vector.
Learn more: Attack Surface Discovery: How to Identify Your Organization's Attack Surface